Are you struggling to completely remove Mac apps that refuse to be uninstalled, are incompletely uninstalled with lots of leftover files, or even continue to run actively after you drag the apps to the trash, and empty it? Or you can’t install, update or upgrade the app due to an incomplete uninstall? The drag-to-trash app removal process usually does not thoroughly remove all elements of the apps, leaving behind a lot of useless digital clutter that takes up your disk space and slows down your overall Mac performance. Fortunately, you can always use the go-to Mac uninstaller Osx Uninstaller to effectively solve these uninstall problems and completely remove all the items of the to-be-removed apps with ease.

The application installation stops and displays error messages on your Mac computer that previous versions were found and must be completely removed before the installation can continue. The application can’t be updated or upgraded due to an incomplete uninstall, or the application is still actively running when you think you’ve removed it by dragging it to the Trash. You’ll learn how to fix these installation problems with Mac application uninstaller Osx Uninstaller, which has been rated the best Mac app uninstaller by our editors for years.
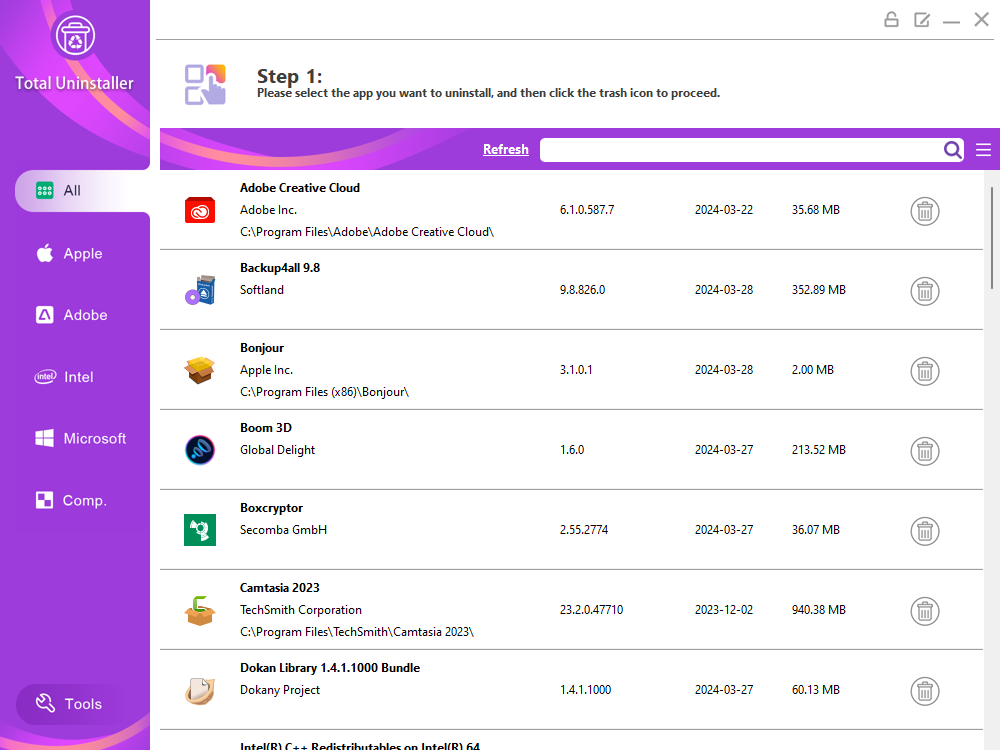
Maybe you’ve received error messages on your Windows that the uninstall process can’t continue and nothing happens when you try to use the built-in uninstaller, or the app installation stops and quits due to an incomplete uninstall of previous versions. You may also want to uninstall unused or rarely used applications and clean up the leftovers to free up disk space – you want to manage them conveniently in one place. Fortunately, a good Windows uninstaller can do it all. In this guide, you’ll learn how to solve these uninstallation problems with Total Uninstaller, which has been our editor’s choice for the best Windows uninstaller over the years. Total Uninstaller is a must-have Windows uninstaller built for thorough app removal, with the best combination of sleek, modern & intuitive interface, easy-to-use app removal workflows, best-in-class app uninstaller, thorough leftover cleaner and powerful cleanup tools. If you’re looking for a well-rounded Windows uninstaller, this is the choice for powerful removal capabilities and attractive & affordable one-time pricing models: Free updates, free upgrades and free technical support for life.

Are you looking for solutions to the problems that the applications can’t be installed due to incomplete uninstallation with lots of leftover installation files, or the installer is corrupted and terminated. Or the applications cannot be updated or upgraded on your Windows PC?
Have been searching for a tool to remove Mac apps & related files completely as well as the useless leftovers? Is your Mac running slowly and slowly with lower disk space and don’t know which apps should be removed, and how? Is your Mac bootup taking longer time with loads of apps run at startup? Are you looking for an app removal tool that can run on your nearly 10-years old Mac? MacRemover is the solution to get all these issues resolved without any hassle, and the one-time pricing model is more than welcome at the era of higher inflation. It is the first Mac uninstaller released on 2012 and has praised by power users and professionals as one of the most essential apps you need to keep your Mac in good shape.
In this post, we will use the latest version MacRemover 2024 to uninstall apps like n-Track Studio Suite, AudFree Audio Capture, and others to justify how the new version holds up its high reputation as it used to be.
StrongVPN is a virtual private network (VPN) service that provides online privacy and security by encrypting your internet traffic and routing it through their servers. Founded in US on 1995, StrongVPN is one of the longest serving VPN services you can depend on to keep your privacy when surfing online.
StrongVPN is an US-based company named Strong Technology, LLC, a Ziff Davis company, which has been developing popular consumer security software and security tools for years. StrongVPN is one of the first VPNs introduced to protect online privacy. The company want to provide a best-in-class VPN network infrastructure that enables their customers to safeguard their online privacy wherever they go, whether they are using desktops or smartphones. With the mission, StrongVPN follows a no logging or tracking policy and features with unlimited bandwidth and military-grade encryption protocols (OpenVPN, Ikev2/IPsec). It is available for Windows, Mac, Android and iOS and allows up to six devices at the same time with unlimited data. Consumers who use StrongVPN will be able to easily switch between different country locations and always the peace of mind that they are no longer being tracked online. Proton VPN VPN hides your origin IP address, preventing others, including ISPs and government organizations, from monitoring your online browsing activity. It also helps encrypt your internet traffic, making nobody can snoop on your browsing via a public Wi-Fi to capture your passwords.
Overall, StrongVPN is an all-around security solution that gives user complete privacy and flexibility to safely and securely access the Internet. It covers VPNs, strong antivirus, firewalls, password safety solutions and more. Get total freedom online with StrongVPN now!
Where to get the latest Unlocator coupons, discounts and lifetime deals? Unlocator VPN is offering the biggest discount of the year to its users who can get up to 66% off Unlocator coupon code (Get a code by clicking on any buttons and apply with it to get extra discount). For Unlocator VPN on 2-year plan, now it costs only $4.99/mo, plus you’ll get a FREE Smart DNS. Unlocator VPN stands out from its competitors because it supports more than unlimited connections on ALL OF YOUR DEVICES! How to get this limited offer from Unlocator VPN by using Unlocator coupon code, discount code or promo code? You can learn more below to get the special deal. No more geo-restrictions. No more buffering. People will get total protection during this shopping season with Unlocator VPN. Learn more below on how to start no logs on the internet from just $1.84/month after coupon code applied.
Are you looking for a verified Proton VPN Coupon Code? If so, you’ve come to the right place. Here we will show you on how to get 55% off Proton VPN coupon code on 2-Year plan at Proton VPN. Fake discount codes for VPNs are everywhere online, so many users don’t know where to get the real Proton VPN coupon code. They spend most of time trying to save money, but finally none of them work properly. Here, we offer the latest VPN coupon codes for our readers. Any readers on our site can have a chance to grab the 55% off Proton VPN coupon code of the year. This is the best value you should never miss out. Learn more below on how to take this special offer.

MediaTek Announces Dimensity 7200 Processor
On February 16, MediaTek announced the launch of the Dimensity 7200 processor, which is based on the second generation TSMC 4nm process, and features two 2.8Ghz A715 performance cores and six A510 performance cores of unknown frequency, and a Mali-G610 GPU that supports up to 1080P and 144Hz displays. 144Hz display. In terms of video, the 7200 processor comes with a 14bit IPS, 4K HDR recording and a 200 megapixel camera, and in terms of networking, not only sub-6Ghz cellular 5G network, but also tri-band Wi-Fi 6E and Bluetooth 5.3.
Apple Launches Apple Music Replay 2023 Campaign
Apple is relaunching the Apple Music Replay for Music Memories campaign on January 30. Through the Music app on iPhone, users can access Apple Music Replay playlists from 2023 and additional content such as top musicians, top albums and total listening time. Playlists dating back up to 2015 are available for subscribers. Unlike Spotify’s annual recap, Apple Music Replay provides users with ongoing tracking of their top songs.