Srv.ailereonx.com site lists merits of it downloads onto web browser and provides with various pop-up ads aimed at coaxing target computer users into being tapped in established deceptive tricks. Srv.ailereonx.com is seemingly a legitimate ads-supported website and dwells on the centralization in upgrading users’ online experience by offering Deals, coupons, review, and search that save you time and money. Actually, the Srv.ailereonx.com is carefully crafted intrusive site by hijackers to cheat online computer users with tactics and acquire money from them.
Worm:MSIL/Necast.D is one kind of computer malware produced by cyber criminals, which runs as a self-contained program or a set of malign procedure. Worm:MSIL/Necast.D is not new for computer users, as it has assaulted a mass of arbitrary machines significantly. Different from other common computer virus, Worm:MSIL/Necast.D is not required to attach itself to the host program in order to perform operation. By default, Worm:MSIL/Necast.D takes advantage of network connection so that to reproduce its copies and propagate (worm) parts of itself onto other computers forcibly. Specifically, the Worm:MSIL/Necast.D is mainly delivered by Internet and SPAM E-mail, which has been compromised to the developers of malware. The original worm infection outbreak as a worm shape showing on affected monitor in the DOS environment, which may randomly devour the letters on the screen to change its shape.
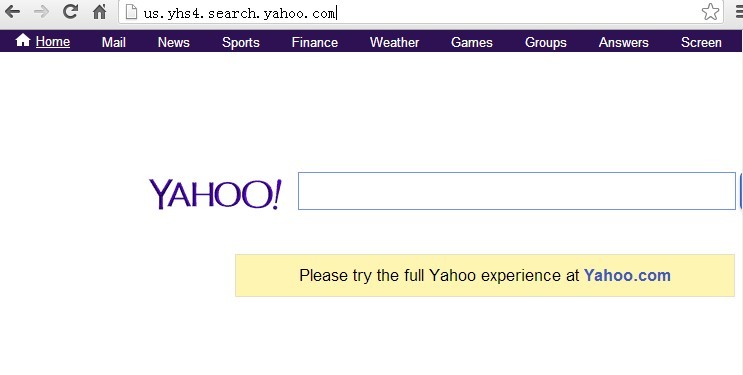
Hackers/ spammers have enhanced techniques to make almost the same interface as genuine ones to obtain PC users’ trust so that evil conducts can be carried out and on without too much disturbance. Us.yhs4.search.yahoo.com is one of the virus made by such hackers/ spammers just like FBI MoneyPak virus. Us.yhs4.search.yahoo.com and the genuine Yahoo share the same interface except URL. With a line of phony kindly reminder saying “Please try the full Yahoo experience at Yahoo.com” totally gains one hundred percent trust from victims.
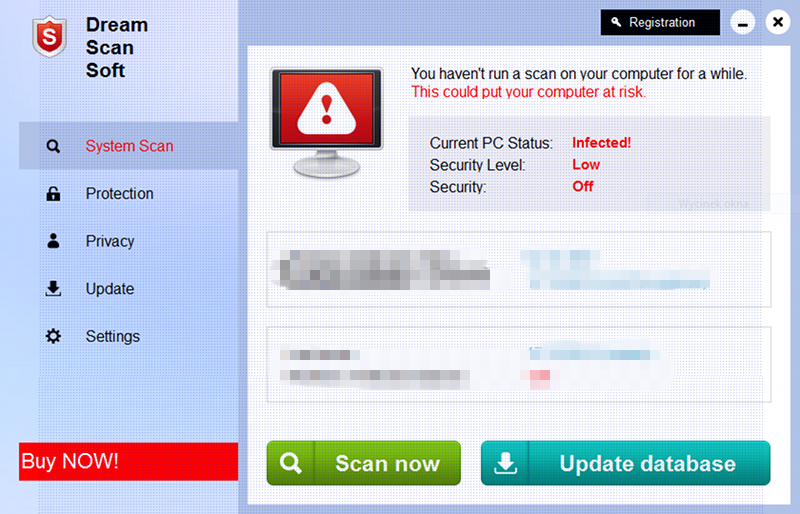
Dream Scan Soft has been proved to a fake security protection tool which has victimized numerous PC users and cause their computer with serious damages. The rogue often got installed into the targeted computer in improper ways, gradually disabling and replacing the original antivirus or antimalware installed in the system without authorization. In this case, it would have the ability to totally be in charge of the computer. It must be noted that the Dream Scan Soft is definitely not a beneficial software for the system security, on the contrary, it would only weaken the computer and destroy it sooner or later.
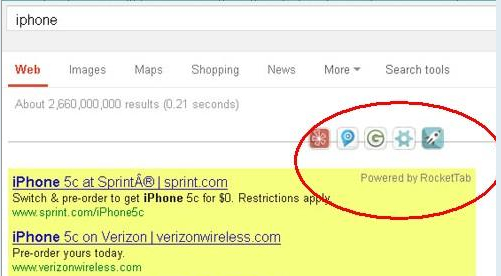
RocketTab Adware now draws influxes of specific attention across the Internet security circles. On one side, the RocketTab pop-up adware declares it is quite useful add-on plugged in Web browsers in order for improving online experience. And inform online computer users RocketTab add-on is a free search engine has ability to be compatible for Internet Explorer, Google Chrome, or Mozilla Firefox, which aims at luring users into putting their trust in and download it. In addition, the RocketTab pop-up reads it is capable of straightforward turning out the epidemic local sites without having to open any additional windows or site tabs, and ongoing multiple sites can be performing at each engine powered by RocketTab.
There have been some complaints reported on computer help forums last month about getting strtsv.com pop-up message mainly telling that credit card information may have been compromised to worry receivers. After some search on the Internet, VilmaTech online experts found that few document on strtsv.com popup virus is recorded given the fact that it is quite a tough popup virus to deal with. Considering the period strtsv.com popup virus has been found to be existent and its superb capability of clinging to a target machine, its rage time, based on past experience, can be anticipated in a couple of months.
Search-india.net is not a reputable website, which utilized by cyber crooks to boost web traffic and obtain benefit from pay-per-click techniques. On account of its aggressive attributes, Search-india.net has been recognized as a browser hijack or redirect virus concentrating on generating destruction on popular-used browsers (IE/Firefox/Chrome). One representative property of Search-india.net browser hijack virus should be the transformation on default homepage or start-up page, which has been typically modified to Search-india.net domain or other related URLs. Thereupon whenever Internet users open a new tab or link on their browsers, the Search-india.net website may pop up automatically out of expectation. Meanwhile, the malign Search-india.net browser hijack virus could also redirect user’s search results to arbitrary materials that have nothing to do with the original ones.

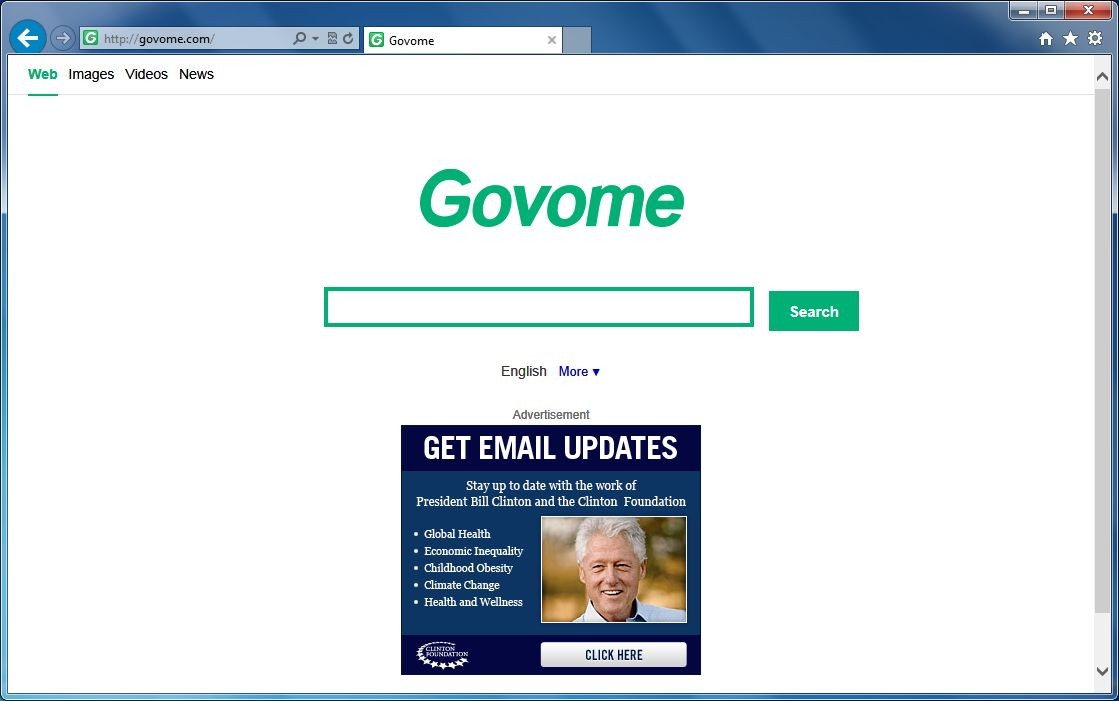
Many computer users are confused about why it redirects to Govome.inapsearch.com when they open a new tab or homepage. Actually, their browser and homepage are hijacked by a malicious browser hijacker Govome.inapsearch.com which changes your browser settings without permission. Once a Windows platform computer was infected with this malware, it would soon be installed automatically in system aimed at the target browsers like Internet Explorer, Mozilla Firefox and Google Chrome. And then it would change the default setting of user’s browser and when you tried to open a desirable page it appeared another website. What’s more irritated was that it also popped up unwanted advertisements in quantities. In addition to that, it would alter the default search engine, add unwanted websites as well as add-ons and give users the wrong connections when they clicked on the links.
Solteratop adware is an unsolicited invader suddenly arising in user’s browser. Most of the Internet users did not care that much at first, making a mistake of thinking it was just an internal program coming with the browser. However, Solteratop usually installed itself into the targeted browser with improper ways, then forcibly displaying all kinds of pop-up ads moment by moment in the computer screen or the browser without authorization. Being constantly disturbed by the nonstop pop-ups, users were easily getting agitated and seriously affected.
Trojan.Win32.Runner.amo is one of the variants of Trojan.Win32.Runner that can be traced back to the year of 2008. Adopting UPX technique, trojan.win32.runner.amo manages to compress its original program code to a size an approximately 35,328 bytes, making it easy to piggyback on whatever programs intended. As a consequence, PC users with less carefulness may very well end up with trojan.win32.runner.amo affection by: