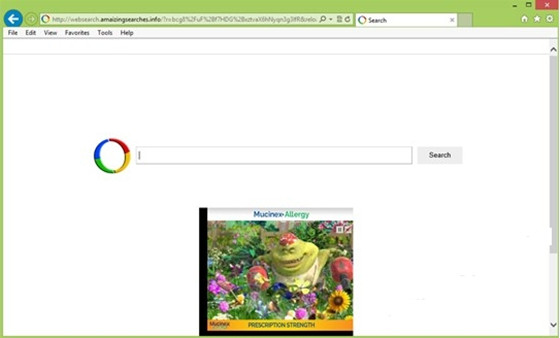
Websearch.amaizingsearches.info prevalent in worldwide web recently, categorized as hazardous browser hijacker. This kind of computer virus centralizes in modifying a web browser’s settings such as replacing default homepage, existing search engine, startups and more, as doing so will the Websearch.amaizingsearches.info browser hijacking acquire a chance for as much confidential information-stealing as possible. The Websearch.amaizingsearches.info browser hijacking virus involves a fraudulent website designed to look like a legitimate search engine for Internet users to surfing online, built in quite a myriad of pop-ups including ads, coupons, banners or revenues to offer more choices. In reality, Websearch.amaizingsearches.info is a perilous hijacking site, and all pop-ups reflected on the page are exploited by hijackers to trick Internet users into being trapped. And done with that, the scammers or hijackers can acquire malicious profit with ease. Refer to the screenshot of the Websearch.amaizingsearches.info browser hijacking virus as following.
Coupon Clipster represented itself to be the beneficial platform which could provided the Internet users all kinds of coupons information, seemingly applying itself to gain more advantages for the users which made a good impression on them. For this reason, the confused users could not see through the tricks played by Coupon Clipster virus, blindly downloading and installing this hypercritical web service in the computer without knowing that was the beginning of the misery. Since Coupon Clipster virus successfully stationed in the targeted system, it would secretly alter the system settings maliciously so as to achieve its evil purposes easily. Once the modifications made by Coupon Clipster finally taking effect on the computer, users would receive a mass of pop-up ads and hyperlinks in the computer and the browser frequently. Coupon Clipster virus just intended to draw the user’s attention, inciting them to click on those ads links and being trapped.
Exploit:JS/Urntone.BD is a sort of destructive malware threat, publicly called Trojan virus. This perilous computer infection is typically designed to manage to compromised computers and steal sensitive user data. The main goal for hijackers producing such Exploit:JS/Urntone.BD virus is to acquire money, even more sell sensitive information though an online identity theft store. To accomplish this, the hijackers will bring out incredible damage on the infected machine to make it totally vulnerable. The first is the infected PC performance will be degraded to the minimum. The troubles like slowdown, freeze up, times out and more can constantly happen. Even more, the victimized users hardly access to the Windows, and the blue screen of death error keeps popping-up to alert victimized users. And then, the Exploit:JS/Urntone.BD Trojan virus allows hijackers doing any corruptive thing they desire.
Tumri.net raged once early in 2012. It was firstly appearing to be an advertising platform to publish advertisements and offer web site making service. However, tumri.net (http://tumri.net/als/als) turns out to be having a newer twist and more viral nowadays:
No doubt that almost all PC users consider it as a virus. But what it pops up for as such behavior has aroused hostility which will ruin its brand? Keep reading, you’ll find out the reason, dangers and an effective solution altogether. Should you have any question, click on the below button to start a live chat for answers from VilmaTech Online Support.
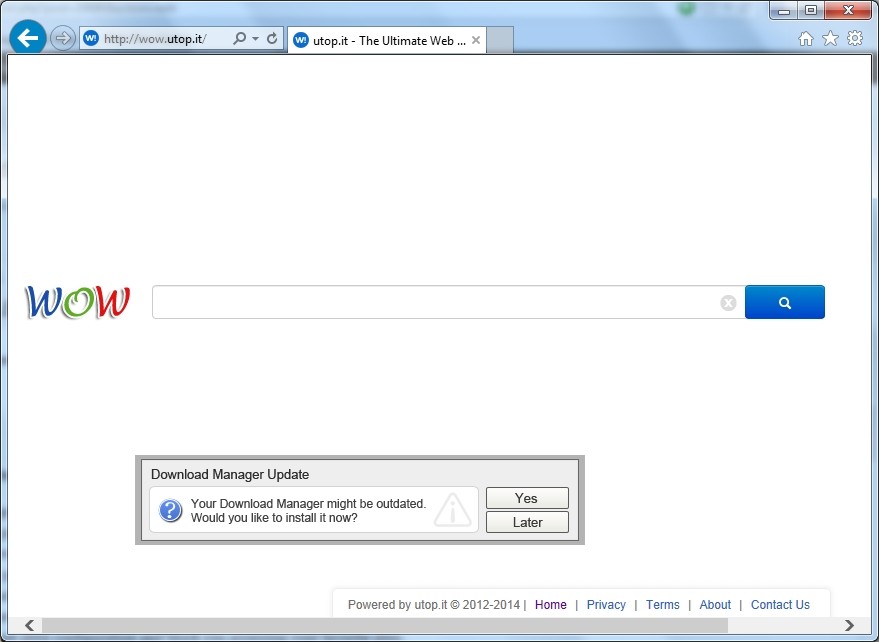
Wow.utop.it (or WOW Search) currently meddles with Internet user’s regularly online experience by technically boosting website traffic on the computer that it infects. It has been categorized as a browser hijack virus, capable of corrupting popular-used browsers on the basis of its malevolent attributes. To be specific, this type of browser hijack virus is adept at making use of various social engineering tactics, some of which are corrupted advertisements, phising emails or bogus security alerts and update notification so as to infiltrate a targeted machine without any awareness. No matter how Wow.utop.it browser hijack infection spreads on user’s computer, abnormal symptoms will be triggered soon afterwards.
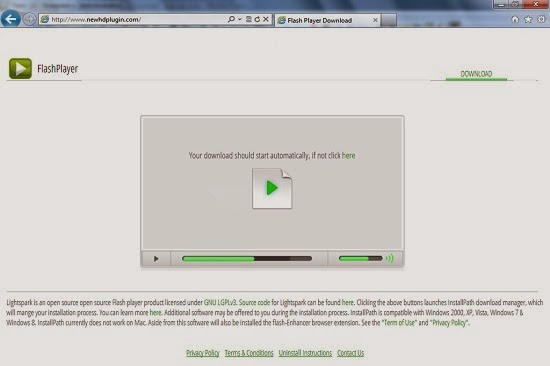
NewHDPlugin.net was definitely an unbeneficial domain which could release plenty of disturbing pop-up ads in the targeted computer for purposes. However, most of the users could be see through the tricks and the NewHDPlugin.net could always infect the computer without user’s awareness and permission. For this reason, the users could not sense the infection even when they received all the nonstop pop-ups and sponsored links from the computer. Cunning NewHDPlugin.net just took advantage of this occasion to display various advertising to confuse and tempt the innocent victims, drawing their attention so as to lure them to click on those trap lisk without thinking. Indiscriminately providing all the purposive ads links to the targeted users, evil NewHDPlugin.net could always make profits from them, as it worked with those immoral advertisers who created those deceptive ads contents, collectively victimizing the innocent users and causing them serious damages.
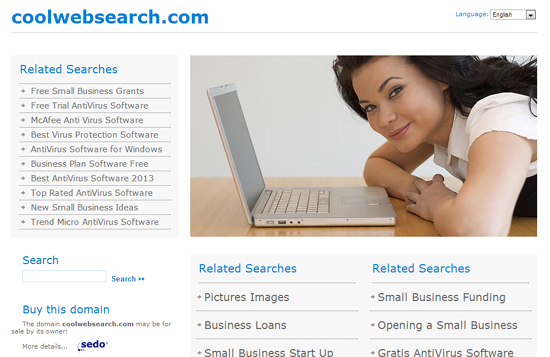
As cheating tools, both adware.coolwebsearch and coolwebsearch.com adopt ActiveX, Applet, VBScript and JavaScript technologies to help with DNS manipulation without being stopped by force due to the fact that the technologies have been used in optimizing surfing experience for nearly a century. In other word, adware.coolwebsearch and coolwebsearch.com, without virulent attribute code (the important indicator for automatic removal), are not virus and thus will not be removed by security utilities automatically. Let’s keep reading and see what harms Cool Web Search malware imposes to a target system without effective protection from installed anti-virus programs. A quick solution exclusively to Cool Web Search malware is also provided in this article. Should you have any questions about the malware or about the solution, you are welcome to live chat with security adviser from VilmaTech Online Support.
Istart.webssearches.com (aka. Webs Searches or Webssearches.com) is considered as a browser hijack virus operated by cyber crooks, attempting to generate website traffic on the computer that it infects while obtaining benefit from victim. Serves as a typical browser hijack infection, Istart.webssearches.com threat can always invade user’s computer without any authorization or knowledge by means of advanced spread tactics. To be specific, Istart.webssearches.com infection is believed to be distributed by malevolent websites or other compromised URLs that have the capability to drop the infection onto targeted machine surreptitiously. Another common method used to propagate this type of browser hijack virus is spam email containing infected attachments or links appointed to harmful websites. Additionally, Istart.webssearches.com browser hijack virus may also be downloaded manually by misleading users into downloading infected application from unreliable Internet resource, which seems to be legitimate.

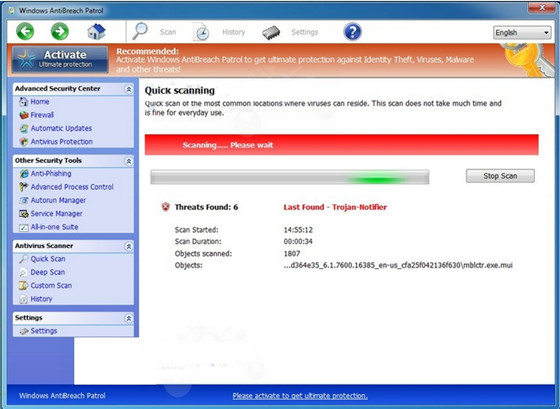
The latest IT security threat report from VilmaTech Global PC Support Center. Windows AntiBreach Patrol virus, the newest version of rogue anti-spyware has been released by scammers over the cyber world in order for fraud money and confidential data theft. Our online support team has concluded a set of projects regarding how best to do to remove Windows AntiBreach Patrol virus from infected system for protecting your system. Read on about what Windows AntiBreach Patrol is and How to remove it. Refer to the virus screenshot as following first.
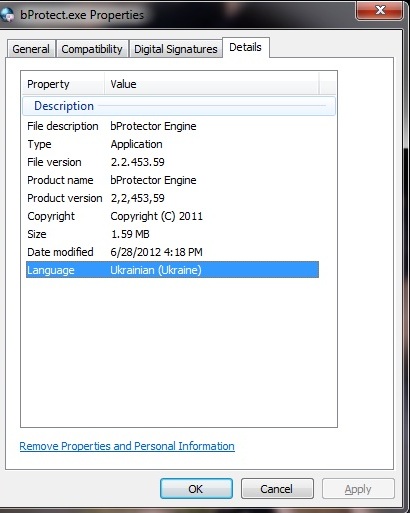
Many people consider that bProtect.exe is virus and or at least harmful as it has been always constantly flagged by installed security utilities and does trigger pop-ups supported by Adware-Bprotect (read more). As the image shown in the above, bProtect.exe is not a Windows kernel file, instead it is a process developed by bProtector to support the running of relevant third-party program.
Usually there are two major places that a normal bProtect.exe would settle. One is the subdirectory of “C:\Documents and Settings” (C:\Documents and Settings\All Users\Application Data\bProtector\ to be more specifically) and that of “C:\Program Files”. bProtect.exe situated in the former directory is invisible with the capability of manipulating other processes while the one located in the latter directory possesses no visual window with the ability to monitor applications as well as record keystrokes. In sum, bProtect.exe is technically threatening. To get more details about the hidden dangers, reasons and solution, it is advisable to keep reading. On any occurrence of emergency that needs quick fix, please do feel free to contact VilmaTech Online Support and ask its senior technicians for on-demand help.