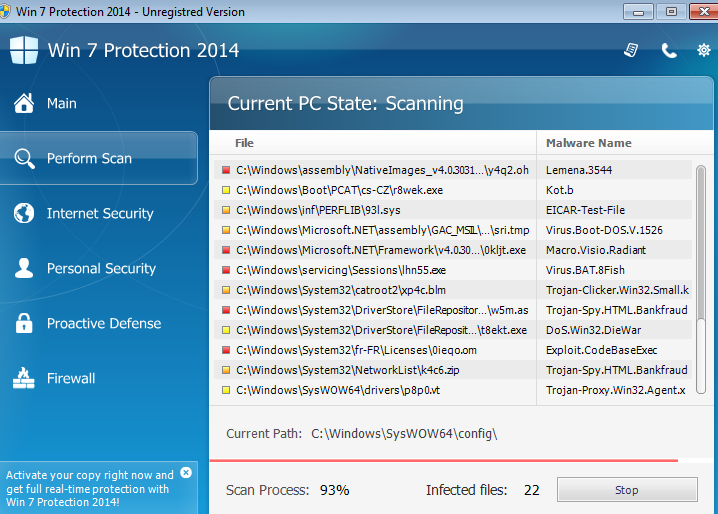
Win 7 Protection 2014 has been confirmed to be a fake protection software pretending to be useful and beneficial for the computer system and in fact, it could only bring nothing but damages to it. In most cases, Win 7 Protection 2014 gets installed into the targeted computer without user’s awareness, and once it succeeded, the whole system would be put in serious danger that most of the users could not realize in a timely manner. For this reason, users might mistakenly use Win 7 Protection 2014 as the default protection and help the wicked wicked malware with wicked deeds. As long as using Win 7 Protection 2014 to scan the system, users could receive an appalling report about the current status of the computer, noticing about those infected files remaining in the computer so as to keep the users worrying.
Simply, Findamo.com virus is supposed to be a kind of malware which is aimed at causing redirection and lead to browser hijacker infection. This redirect virus may cause bad surfing experience on web and threat to Internet security.
Many people call FixSpeedy Optimizer virus and some call it Trojan horse due to the fact that its manufacture is based in India and that there seems to be no way to uninstall FixSpeedy Optimizer. Its name implies that the program is created to speed up the performance as well as operation. In reality, more pop ups come up from nowhere afterwards to not only ruin surfing experience but also slash down the PC performance. Obviously, FixSpeedy Optimizer has put more focus on intercepting traffic to make money and it is thus not able to speed up performance. Therefore, according to VilmaTech Online Support, FixSpeedy Optimizer is not a virus, it is no more than a PUA (potentially unwanted application) that can impose potential dangers. This is why anti-virus programs are not removing FixSpeedy Optimizer.
TorrentLocker is the term used to depict one new form of ransomware variant that may result in hazardous symptoms on personal computers (PCs) as well as nettlesome Android security issues on Smart Phones. The infection was first born in Australia and has keeping assaulting PC users and Android users worldwide. To strengthen the collapsing force of TorrentLocker, the infection assimilates the most advanced attributes from traditional ransomwares, some emblematic examples of which are CryptoWall Lock virus, CryptoLocker Ransomware and more. In consequence, TorrentLocker virus can often infiltrate onto a targeted machine without asking for any approval; and PC users becomes the main victims whose computers are restricted to access. In computing, TorrentLocker is malware designed by cyber crooks for data kidnapping, attempting to extort money from victims through locking affected machine or encrypting the files stored on hard drive or network disks.
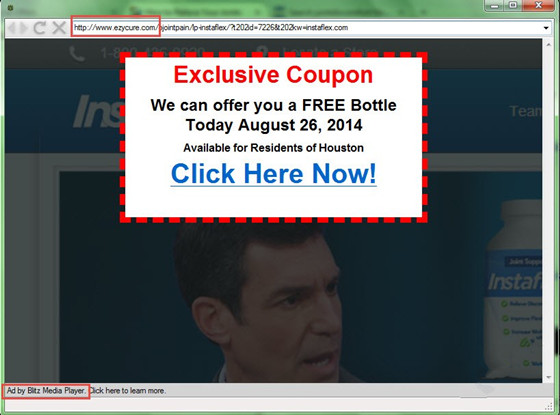
ezycure.com is categorized as perilous pop-up malware, which can carry out browser hijacker to victimized computers and effort to compromise the infectious system so that give rise to a complete control by cybercriminals. If you have seen several hijacking sites in the past that used to steal confidential information from the compromised computer, the ezycure.com also does the similar harm. The ezycure.com browser hijacker mimicks as an useful search engine just like Internet Explorer, Google Chrome, Google Chrome and more, as doing so to achieve the trusts of those targeted users and then persuade them to do some risky operations as the cybercriminals expected. Usually the ezycure.com pop-up malware suggests that the users should download a particular web plugins or software in order for improve PC performance. When users download this recommended download, the ezycure.com malware could gain access to allow malicious payload drop down on the targeted machine. And since that, the ezycure.com will try efforts to mislead victimized users to enter their login-credentials and simultaneously achieves the stealing. Refer to the Searchult.com virus similar to Ezycure.com malware.
Fix25.com was a tricky domain suddenly showing in the targeted browser without the computer user’s permission. Fix25.com is not a computer virus but it could cause more trouble to the targeted computer just like the regular virus and malware. Since the computer was infected by Fix25.com, users would receive nonstop pop-ups from Fix25 which might seem so beneficial for users but it is not as it appeared. Fix25.com just takes the chance to distribute all the malicious pop-ups to the computer while the users were surfing on the Internet. In that case, the users might be easily attracted by Fix25.om pop-ups because it pretended to be friendly and nice to them. As long as the innocent users were fooled by Fix25.com and blindly clicked on those links or button that Fix25 asked them to, they would be trapped.

If you are annoyed by the non-stoping pop-ups from Downasd.com regardless of whatever browser and search engine you are using, your computer must be infected with Downasd.com pop-up virus. Though it is not typically technical virus, it is able to make a mess to your browser and interfere with your normal online surfing.
Before answering the question, we should figure out the real property of securepaths.com. Securepaths.com usually pops up with random ads and its URL is followed by a long line of letter and number combination. This is what we call pop up which belongs to adware. Clearly, Securepaths.com is not technically a virus, it is at worst being put to the category of PUP (potentially unwanted program) that does impact adversely on surfing experience. While anti-virus program fights against infections, Securepaths.com popup cannot be removed/stopped by automatic methods.
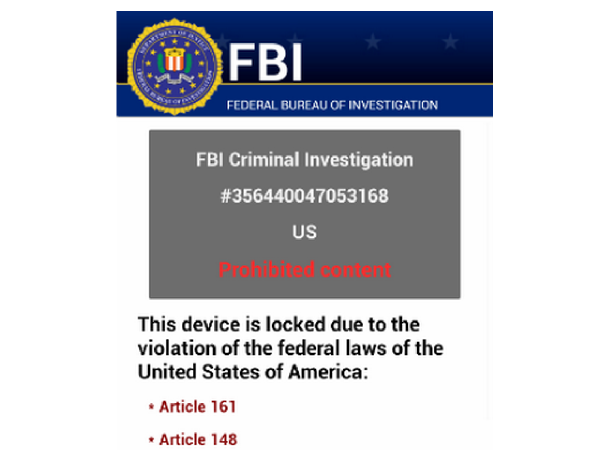
More recently, a new Police or FBI virus is delivered from Android Smart Phones, the devices that are often short of appropriate security protection. Symantec once made a statement that one certain ransomware campaign had the capability to implement illicit money extortion from victims up to $400,000 in a month; and a huge amount of confidential data, which is equivalent to $5 million, may be stolen by malware distributors in a year. Police or FBI virus spreading on Android phones can be collectively classified as one new form of ransomware called Troj/Koler that specifically attacks unsubstantial Android operating system. Similar as the traditional FBI or Police virus on Microsoft windows operating system, this type of Android ransomware always restricts the access to GUI (Graphical User Interface) by displaying a bogus warning notification on the monitor.
New release of the Searchult.com browser hijacker in the cyber world has hit a merely of online users’ computers, and its makers cybercriminals are once again using it to steal victims’ money and confidential information. Searchult.com exactly is classified as the perilous malware called browser hijacker, also publicly known as the redirect malware that focuses on redirecting victimized users to some malicious sites, pop-ups and phishing. The victimized users whose computers are attacked with the Searchult.com malware have to be reminded that it is often possible to exposure personal sensitive information, even be taken advantage to participate in illegal online commercials for malicious benefit-making. Once attacked by such Searchult.com browser hijacker, one of the most notable symptoms is the redirect. All searches will be redirected to some established malicious pop-ups related with the Searchult.com.