Once again, a latest findings of perilous Trojan virus called Trojan.Win32.Bublik.cfgi has been increasingly epidemic in the cyber world, which distributed by hijackers aimed at attacking Internet users’ computers and stealing confidential data there. The Trojan.Win32.Bublik.cfgi virus is categorized as hazardous Trojan virus, which main work includes the large increase in sensitive data breaches and targeted attacks. The sensitive information such as log-in credentials, banking data, or online transaction data must be at the high-risk of exposure. Furthermore, the hijackers also can let Trojan.Win32.Bublik.cfgi virus constantly exploit system vulnerabilities to get the infectious machine totally vulnerable, which allows opening backdoor and hijackers accessing to the infectious computer for confidential information-stealing.
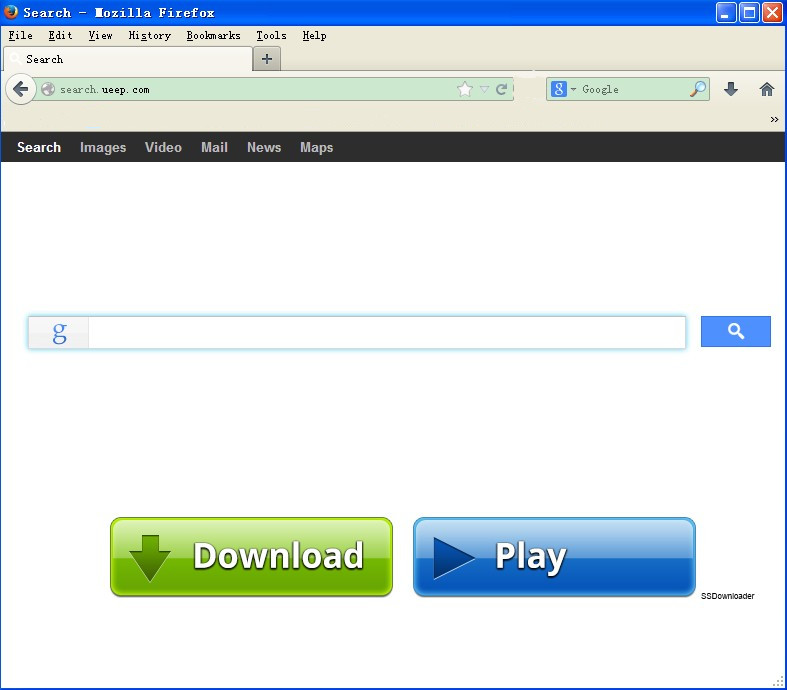
As what we can see the ads on its interface, they vary themselves most of the time trying to push products or some web sites. Obviously, search.ueep.com is a piece of freeware that needs to get fun from advertisement for continuous operation. This indicates that ad bombardment can be foreseeable soon after search.ueep.com’s hijacking. It can be learned now that what search.ueep.com aims at is getting profitable income by pushing products for online operators. However, some more problems and potential harms can be triggered for that objective. Keep reading to find out more that you should have known. Any question will be answered promptly if you contact VilmaTech Online Support here.
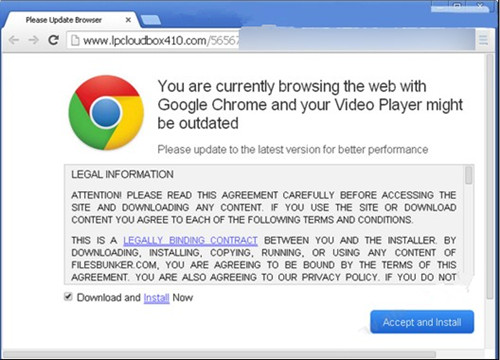
Lpcloudbox410.com belongs to the adware team which could make profits by releasing tons of disturbing pop-ups to the targeted users, regardless of their feelings. In most cases, the Lpcloudbox410.com had to firstly infect the computer by using improper means and also hid so well from the innocent users, in this way, even the system was seriously infected by the Lpcloudbox410.com or any malware it introduced, the victims could never detect them until things got serious in the computer. Once the Lpcloudbox410.com had its way by infiltrating into the targeted system, it would have the ability to mess with the computer and make some malicious modifications in system so as to achieve its evil purposes. Since Lpcloudbox410.com successfully stationed in the computer, the users could receive a mass of pop-ups from the browser or the computer corners as long as they turned on the computer.
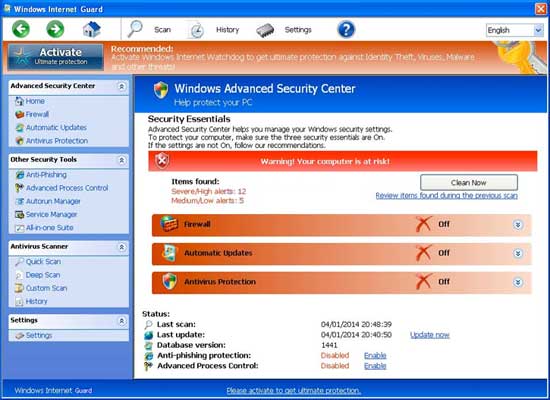
No doubt that Windows Internet Guard is another fake anti-virus program that copies the interface from a genuine Windows anti-virus program. There are about 20 FakeVimes coming along one after another. They share the same interface except the name. Here’s the list of some notorious FakeVimes rogueware:
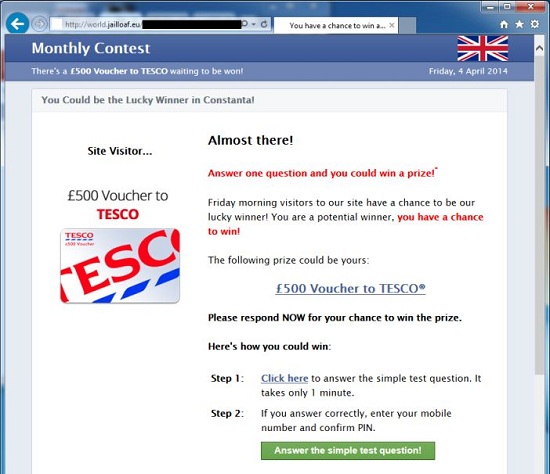
World.jailloaf.eu was believed to be a deceptive domain which specifically displayed all kinds of pop-ups to the Internet users so as to make profits by noticing them about all the tempting prizes which turned out to be some kinds of immoral scams. World.jailloaf.eu was actually an unwanted malware which infected the targeted computer without a trace, that’s the reason why the masses of the computer users were unable to notice the infection or find out that the World.jailloaf.eu was hazardous for both the computer and themselves. Unfortunately, most of the innocent users could easily be tempted by those hard-won prizes provided by World.jailloaf.eu. With the intention to gain advantage, more and more innocent victims blindly followed the orders showing in the World.jailloaf.eu pop-up content, resulting in irreparable losses. Here to remind all the Internet users to be cautious about the World.jailloaf.eu ads and should remove this malware from the computer as soon as possible.
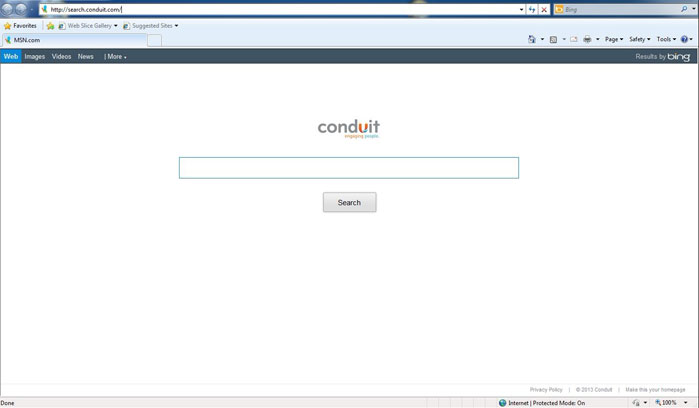
Search Protect by Conduit has been recognized as PUP (Potentially Unwanted Program) that may often overlap with adware or browser hijack virus: Search.conduit.com/Search Conduit virus (How to Remove), capable of triggering malignant symptoms on the computer that it infects. Judging by appearance, Search Protect by Conduit serves as a free application that is produced by conduit. Ltd., allegedly calming to be a helpful extension that has the capability to protect user’s web browsers against potential malware or other unclear subjects. This may happen to common-used browsers: Internet Explorer, Mozilla Firefox and Google Chrome. In reality, it cannot overtly distinguish Search Protect by Conduit as a malicious or benignant program. However, being noted for its characteristics, Search Protect by Conduit has been categorized as malware that should be eradicated from computer thoroughly.
Win32/Patched.IB [Trj] is a high-risk Trojan infection that is generally located at C:\WINDOWS\system32\rpcss.dll in affected OS. In computers, Win32/Patched.IB [Trj] is a program in which malevolent codes are contained inside apparently. It can be easily propagated onto a targeted machine through a variety of means without host’s awareness. Most commonly Win32/Patched.IB [Trj] often masquerades as a benign application that can be downloaded manually from Internet resources. When initialized, the components of Win32/Patched.IB [Trj] could be activated and executed automatically on the computer that it infects. Another common used way to diffuse Win32/Patched.IB [Trj] is the drive-by-download which exploits security vulnerabilities in web browser, regardless of IE/Firefox/Chrome, or email clients containing activation code of the virus.
Policeweblab.com is regarded as hazardous ransomware (browser blocked virus), a sort of Trojan virus that can block Internet browser and encrypt personal files on the compromised hard-drives. The malicious Policeweblab.com typically uses the disguise of an authentic enforcement agency to scare Internet users and always attempts to extort money from them. Policeweblab.com also refers to the so-called browser hijacker, which takes advantage of the same Trojan virus for infecting targeted system, and only differing in aboveboard extorting. This implies that the Policeweblab.com intrusive site not only compromises the target web browser but also blackmails money by displaying fake alerts purportedly distributed from an enforcement agency. Recently, this type of FBI virus is able to attack and block the Android Phone. More ane more users who use cell phone with Android system have encountered this problem. The screen of the Android phone would be blocked by the Policeweblab.com virus. People can do nothing with their phone. In reality, the Policeweblab.com author just exploits a commonplace online fraud to trick money from innocent Internet users. You may refer to the Policeweblab.com blocked webpage as below.

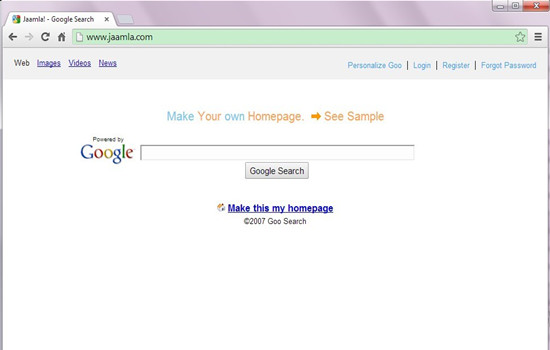
Jaamla.com was definitely an unwanted hijacker which has utilized improper means to infect targeted computer so as to have its way without awareness. In most cases, users would find the Jaamla.com virus suddenly taking up the browser homepage unreasonably which was not their order. Since then, no matter when the Internet users started the browser for searching, the intruder, Jaamla.com, would show up in the address bar automatically, pretending to be the default search service. Most of the innocent users might have not noticed the replacement of the Jaamla.com virus, blindly conducting the search without knowing the purposive hijacker could lead them to any websites it wanted. Under this circumstance, Jaamla.com virus would get the initiative to transfer the users to specified advertising websites, completely regardless of the user’s original search query. With the baleful Jaamla.com redirect virus constantly messing with the innocent users, more and more unexpected safety hazards would be approaching.
Win32/Alureon.gen!A is one of the variants of Alureon Trojan that features itself with online data-stealing capability. Therefore, once a computer is attacked by the Trojan Rookit, chaos on browsers would break loose, such as new tabs keep opening with junk websites including some other search page instead of intended web pages. Obviously, Win32/Alureon.gen!A is a Trojan horse that intercepts system’s network traffic for usernames, passwords and credit card data and that mainly designed to attack 32-bite system.