Trojan Horse PSW.Generic11.CIZG is a computer virus, which has been technically categorized as a high risk multiple component security infection, capable of carrying out destructive actions on the computer that it infects. According to recent security statistics, Trojan Horse PSW.Generic11.CIZG is specifically generated by cyber crooks to affected Windows operating system (OS), including Windows XP, 7, Vista as well as modern versions of Windows 8. Similar as other Trojan infection, Trojan Horse PSW.Generic11.CIZG, in reality, is a non-self-replicating type of malware program containing programmed codes. When executed, this type of Trojan virus would typically insert its malevolent codes in kernel system for the sake of making compulsive modification in Windows registry. The work of MBR (Master Boot Record) would be first influenced due to the changes in Windows. As a result, Trojan Horse PSW.Generic11.CIZG virus could be loaded up automatically on every Windows boot.
The Rootkit.Win32.Zbot.sapu, the hazardous Trojan virus, has been regarded as infamous malware utilized by hijackers over the cyber world – which main goal is to acquire illegal benefits and even steal confidential information from those compromised PCs. The Rootkit.Win32.Zbot.sapu Trojan virus constantly exploits system vulnerabilities dedicated to the confidential information exposure, which means hijackers can access to the infectious computer through backdoor that opened by vulnerabilities and collect confidential information without any distraction. Some of the previous released security malware, just like the perilous malware called Trojan.Zekos.Patched, were focusing on degrading the infectious PC performance and corrupting system, as doing can such Rootkit.Win32.Zbot.sapu Trojan virus makers make the compromised computers totally vulnerable for enticing more worms or ransomware and handle with malicious activities for benefit-making. By definition, the Rootkit.Win32.Zbot.sapu Trojan virus is a nasty tactic taken advantaged by cyber criminals to make money, which has been a commonplace tactic often utilized by hijackers. Also, Rootkit.Win32.Zbot.sapu may potentially re-register the virus DLL attempting to totally corrupt infectious operating system.
The very prominent feature about Trojan.Zekos.Patched is that it attacks rpcss.dll process and service, the one with the responsibility to call subsystem so as to support the proper running of the whole machine. Below is the flow chart of rpcss.dll’s working mechanism:
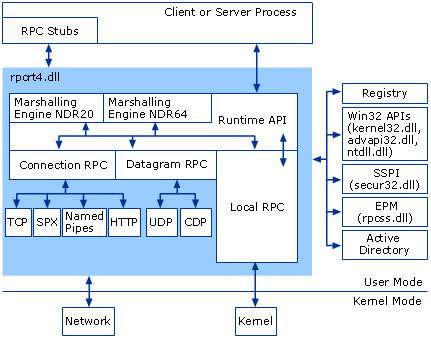
It is now clear that once being attacked by Trojan.Zekos.Patched, both kernel system and browser will be modified randomly to give rise to the mass as follows:
Tab.lightningnewtab.com is not a reputable website that may carry out damaging activities on the computer that it infects. In reality, it cannot absolutely recognize Tab.lightningnewtab.com website as a computer virus on the basis of its attributes. However, a majority of PC users have criticized Tab.lightningnewtab.com as a PUP (Potentially Unwanted Program), regularly overlapping with adware or browser hijack virus, which has the capability to trigger harmful symptoms on the compromised machine. The apparent disruption of this threat is often embodied on user’s web browsers, including Internet Explorer, Mozilla Firefox and Google Chrome. Most commonly Tab.lightningnewtab.com may forcibly alter the search and error page of a definite browser to its assigned URLs, by technically making modification in web browser settings such as default DNS configuration. The web search provider of an affected web browser may also be changed in a forcible fashion to http://tab.lightningnewtab.com.
Torcho.com is regarded as potentially perilous website capable of tampering with default Internet Settings and redirecting victimized users to some hazardous pop-ups including coupons, revenues, pop-under, and more. The infamous hijackers have carefully crafted the Torcho.com redirect site to attack Internet browsers like Internet Explorer, Google Chrome, or Mozilla Firefox, which endowed with abilities to overlap all defaults and stop victimized users from accessing to any desired search. Torcho.com redirect site, the new browser hijacker, indentified as a malicious malware that work confuses on affecting various version of Windows Operating System. Although an anti-virus program installed on your computer to fight against malware, the Torcho.com browser hijacker still can bypass any normal detection and sneakily infiltrate on the targeted computer without any need of user’s permission. The solitary goal of hijackers propagating such Torcho.com malware is in order for boosting malicious traffic and stealing confidential information.
Trojan.Shredboom is a destructive security detection reported by antivirus software programs. It is programmed with advanced rootkit capabilities by malware distributors for the sake of damaging user’s computer without any permission or knowledge. Similar as other typical Trojan virus such as W32.Mezit!inf infection, Trojan.Shredboom has been universally considered as a program containing malevolent codes and files that should be terminated from affected computer timely. As a matter of fact, Trojan.Shredboom does not replicate itself but it can be harmful determined by the nature of Trojan. Most commonly this type of Trojan virus may often infiltrate onto a targeted computer surreptitiously as drive-by-downloads. To be specific, Trojan.Shredboom may be distributed by malicious websites or legitimate websites that have been compromised and then forcibly drop the virus onto a compromised computer. Users may also have the possibility to get infected with Trojan.Shredboom virus when they navigate a malign link embedded in a spam email or download a “free” application from Internet which seems to be useful and standard.
Infostealer.Pandebono was released recently over the worldwide web, a kind of Trojan virus carefully crafted by intruders aimed at returning a serious system crash and sealing confidential information from the compromised computer. Infostealer.Pandebono Trojan virus affects all versions of Windows Operating system and quite a few online computer users are suffering from its corruptive damage now. The initiative of the Infostealer.Pandebono Trojan virus can be formed following those potentially unwanted programs, which refers to the so-called drive-by downloads. Infostealer.Pandebono Trojan virus can infiltrate on the targeted computer without any consent through drive-by download including freeware, shareware, web plugins, add-ons and more. Generally, hijackers or scammers frequently conceal such Infostealer.Pandebono Trojan virus by packaging with some third-party Windows programs. Just need online users’ unsuspectingly download those potentially intrusive program, the Infostealer.Pandebono virus then can initiatively add to the targeted computer without any need of permission, as attacking computers so can hijackers can propagate security malware without any distractions.
Media Buzz 1.1 was an inconspicuous infection that attacked the targeted computer without users’ awareness. Coming with a perfect disguise, the Media Buzz 1.1 adware could avoid almost all the antivirus software installed in user’s computer, getting the opportunity easily to mess with the infected system. Because most of the users could not detect the cunning Media Buzz 1.1 adware in a timely manner, unconsciously being fooled by this unwanted invader. In most cases, the Media Buzz 1.1 adware could active in the system background without consents, under this circumstance, as long as the infected computer was on, Media Buzz 1.1 adware would have the ability to display tons of pop-up ads and hyperlinks in the computer constantly. Once the users mistakenly clicked on those trap links, Media Buzz 1.1 adware would have the initiative to lead the innocent users to any advertising website it wanted, trapping them in those unsafe places so as to make profits from them.
Mystart.vi-view.com currently meddles with Internet user’s regularly browsing routine through making full use of a variety of hack techniques. It has been universally considered as a destructive browser hijack virus produced by cyber criminals to disrupt a definite web browser apparently, regardless of IE/Chrome/Firefox, in order to generate revenue from victims. By default, a browser hijack virus often refers to the modification of a web browser’s setting, and the changes are regularly performed without user’s authorization or awareness. Mystart.vi-view.com, similar as Dm.StartNow.com redirect virus, is one latest browser hijack virus that has the capability to triggering damaging symptoms on the computer that it infects. In reality, it has no big difference between Mystart.vi-view.com and other legitimate website providing search engine services in web interface. However, when Internet users do search in Mystart.vi-view.com search engine, it may take control of affected computer’s Internet connection and redirect users to its appointed suspicious web pages operated by malware distributors.
Mystart.vi-view.com currently meddles with Internet user’s regularly browsing routine through making full use of a variety of hack techniques. It has been universally considered as a destructive browser hijack virus produced by cyber criminals to disrupt a definite web browser apparently, regardless of IE/Chrome/Firefox, in order to generate revenue from victims. By default, a browser hijack virus often refers to the modification of a web browser’s setting, and the changes are regularly performed without user’s authorization or awareness. Mystart.vi-view.com, similar as Dm.StartNow.com redirect virus, is one latest browser hijack virus that has the capability to triggering damaging symptoms on the computer that it infects. In reality, it has no big difference between Mystart.vi-view.com and other legitimate website providing search engine services in web interface. However, when Internet users do search in Mystart.vi-view.com search engine, it may take control of affected computer’s Internet connection and redirect users to its appointed suspicious web pages operated by malware distributors.
