Windows Web Shield is a newly released Rogue-AV or Rogue security software program defined as malware, which is designed specifically to damage or disrupt an affected computer system. It can be recognized as one form of Internet fraud used by malware distributors for illegal purposes. Windows Web Shield, much as the name implies, mainly assaults individuals using Microsoft windows operating system, including Windows XP, Windows 7, Windows Vista and Windows 8. In order to cover up its perniciousness, Windows Web Shield generally takes measures by simulating the basic operating principles and GUI (Graphical User Interface) instruction from a standard antivirus program. However, it cannot be able to enhance a computer’s security but carry out a variety of damaging activities on the computer that it infects. Basically, Windows Web Shield infection can often infiltrate onto a user’s computer without any awareness using advanced social engineering tactics.
Recent revelation about Irapidseek.com and its associated pop-ups have forced a myriad of online computer users into dilemma as the malicious thing have put the issue of confidential information exposure in the spotlight. By definition, the Irapidseek.com is regarded as browser hijacker, also publicly known as redirect virus carefully designed and exploited by cybercrime gangs to fraud money and steal sensitive data from compromised computers. Certainly the makers of the Irapidseek.com browser hijacker can make the targeted computer completely vulnerable and perform illegal commercial activities engaged in benefit-making. There are a lot of victimized online computer users of the Irapidseek.com redirect virus are now underway. They are suffering from a series of troubles distributed by such Irapidseek.com hijacking virus. Once installed, the Irapidseek.com redirect virus is capable of tampering with default Internet settings and altering defaults with an established site and hazardous pop-ups. One main effort at collecting confidential information such as online transaction data, privacy configuration, or banking data stored in hard drives or compromized web browsers such as Internet Explorer, Google Chrome, Mozilla Firefox, Opera, and more.
HEUR:Trojan.OSX.Vsrch.a is categorized as a Trojan horse but with additional capabilities. “HEUR” indicates that the Trojan horse mainly gives rise to browser problems. As what anti-virus program detected, “/users/[user name]/Library/Internet Plug-Ins/ConduitNpapiplugin.plugin/Contents/[OS]/ConduitNPAPIPlugin” is reported as HEUR:Trojan.OSX.Vsrch.a. It is obvious that the web applications produced by conduit search have been taken advantage by the HEUR Trojan horse.
By reading HEUR:Trojan.OSX.Vsrch.a’s payload, victims will get to know:
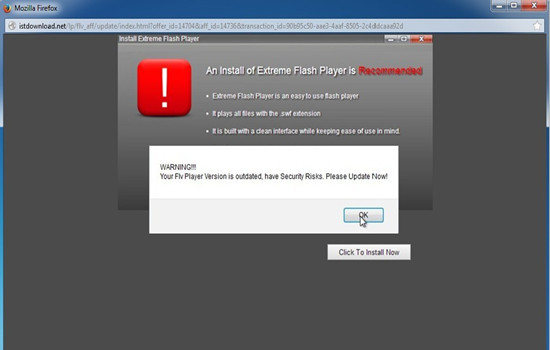
IsDownload.net was considered as an unsolicited web service showing in the targeted computer abruptly, coming with the name of IsDownload in order to make the computer users believe the IsDownload.net was dedicated to provided software download services, so it could gain more trusts from the users and avoid being removed from the system. Because the IsDownload.net installed in the targeted computer by using improper means, in most cases, the users could not notice the infection in the first place and mistakenly considered IsDownload.net was coming with the current search engine. For this case, IsDownload.net would get the chance to carry on its evil deeds in the infected system. Since the unwanted IsDownload.net successfully got installed in the computer, it would suddenly get the right to display tons of unknown software download prompts to the users, getting their attention with the nonstop pop-ups showing in the browser and intending to lure them to permit the download requests unwittingly.
Trojan.Rhubot is the term used for Trojan detection that has been added to Microsoft antimalware signatures. It has been considered as a high risk security infection due to the malignant behaviors it could make on the affected computer. Similar as other Trojan threat such as Trojan.Cidox.C, Trojan.Rhubot is adept at making full use of a variety of social engineering tactics in order to be propagated onto a user’s computer surreptitiously. Specifically, Trojan.Rhubot often disguises itself as an image, screensaver or ZIP archive file attached to an e-mail message, and a browser plug-in or extension containing the activation code of the virus, which seems to be helpful for popular-used web browsers, regardless of Internet Explorer, Mozilla Firefox and Google Chrome. When PC users employ those malevolent resources, Trojan.Rhubot could be dropped and installed on their PCs without any authorization or knowledge. Apart from the basic spreading approach, The malicious payload of Trojan.Rhubot is being delivered to computers with the aid of various exploit kits such as BlackHole, which have the capability to diffuse the infection by taking advantage of all possible found security vulnerabilities.
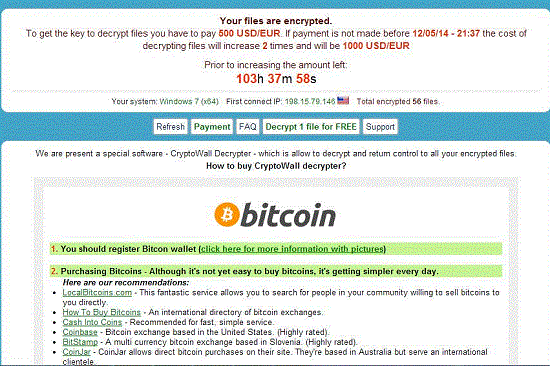
A new piece of Ransomware known as CryptoWall Decrypter is attacking Internet users’ computers as which can gain elevated operating system or Android system privileges to compromise with malicious payloads. CryptoWall Decrypter is recognized as Rasomware, is a fabulously hazardous virus as the form of malicious activities uses encrypted keys. Victimized users would lose capabilities of accessing personal files due to all files on the compromised computers would have been encrypted with using RSA public-key cryptography. CryptoWall Decrypter ransomware, alike the CryptoLocker first surfaced in September 2013, blocks PCs and encrypts files with a malicious payload. Since its initial discovery, the CryptoWall Decrypter ransomware has evolved into a sophisticated perilous computer and Android system infection, which has ability to attack targeted online computers without any need of permission and extort money from those innocent users. Furthermore, the required fine to decrypt files reflected on the CryptoWall Decrypter ransomware page is around 500-1000 USD/EUR. CryptoWall Decrypter virus threatens victimized users that the cost of decrypting files will increase 2 times if payment is not made in time. You can refer to the screenshot of the CryptoWall Decrypter Android virus as following.
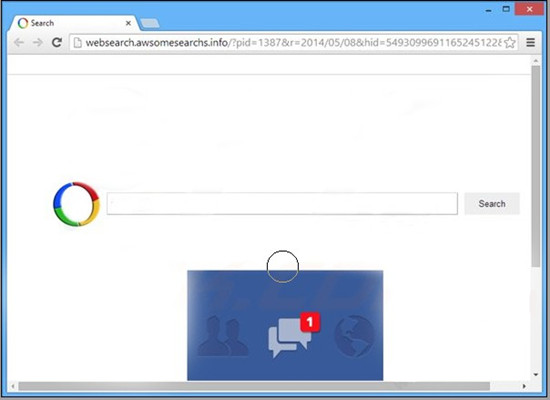
Websearch.awsomesearchs.info belongs to the series of the Websearch Redirect viruses. Cybercriminals created the Websearch.awsomesearchs.info hijacker to achieve their evil purpose of getting exorbitant profits from the masses of innocent users. For this reason, the tricky Websearch.awsomesearchs.info redirect virus would be widely released on the Internet, infecting the targeted computer with various means. In most cases, the Internet users could not detect the Websearch.awsomesearchs.info infection in a timely manner because the cunning hijacker was decorated with the similar interface of Google Chrome, successfully confusing the users and avoiding their suspicions. Under this circumstance, the Websearch.awsomesearchs.info would have the ability to station on the browser without being detected by the users or the installed antivirus software. In this way, the default browser homepage would be replaced into the Websearch.awsomesearchs.info without permission. Whenever the browser was launched, users would have to use the Websearch.awsomesearchs.info as the search service without knowing the original one was hijacked.
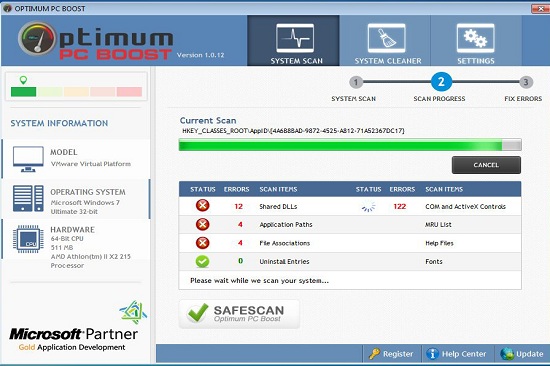
Optimum PC Boost is not a reputable program, which has been considered as a fake antimalware application or rogue security software, capable of triggering destructive activities on affected computer. More recently, Optimum PC Boost primarily attacks individuals using Windows operating system (OS), especially the one which is short of appropriate security protection. Basically, Optimum PC Boost always attempts to pretend to be helpful application by simulating the approved GUI (Graphical User Interface) from standard antimalware software. It claims to be a tool that can be used to enhance a user’s computer’s security and safeguard it against any type of malware infections. However, the counterfactual situation is, Optimum PC Boost may often sneak into a user’s computer without any authorization or knowledge. Users may often get infected with this type of rogue virus when they visit compromised web pages or by navigating to a malign link embedded in a spam email. In this way, malware distributors will make full use of BlackHole server’s landing page leveraging obfuscated JavaScript to determine all possible exploits on the computer that it infects, and then secretly drop and install the components of Optimum PC Boost in Windows.
Actually mysearchresults.com is a browser hijacker; to be more specific, it is a traffic exchanging site for better product promotions. In other word, mysearchresults.com intercepts as much traffic as possible from one computer to help with higher exposure and rank in search results by simply sticking to a machine.
While mysearchresults.com has been made clear that by itself, it is not dangerous to machine or information security; however, people should still pay attention to the potential dangers brought along with it.
Getting pop-ups and deals from the Ultra Notifier could drive the Internet users excited. As nonstop special offers constantly showed in the targeted computer, the purposive and unbeneficial Ultra Notifier adware would always find a way to draw the innocent users’ attention and mislead them with improper means. As long as the users could not help carrying on clicking on those trap advertising links, Ultra Notifier could successfully transfer the innocent victims to any website it wanted. For this case, as more and more innocent users were tempted by all kind of pop-up ads and led to those unfamiliar sites, Ultra Notifier could seize the chance to make a profit from them. Just because the users could not see through the cunning tricks played by the malicious Ultra Notifier and coveted small advantages, so whenever the innocent users saw those pop-up ads and deals, they could not resist the temptations and walked into the traps without knowing.