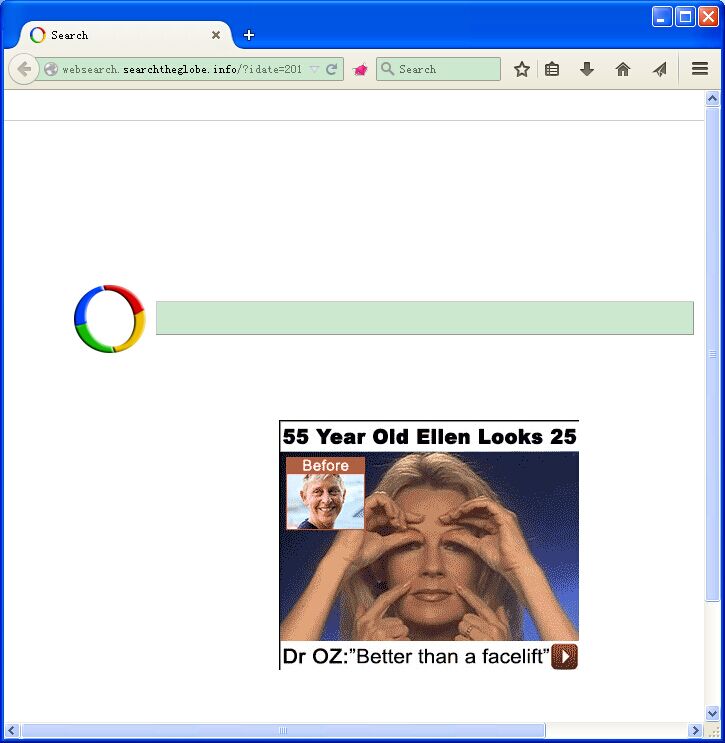
The newly updated malware called CryptoFortress has been attacking increasingly online users’ computers and attempting to pop-up threatening warnings for tricking money. Because this CryptoFortress virus is undoubtedly malicious among the most ransomware, it tends to carry out incredible damage on the infectious machine. It encrypts all important files on the targeted machine with specific techniques and persuades victims to get all files back by purchasing the established decryption software. Similar to the version of the TorrentLocker hazardous ransomware, CryptoFortress virus can compromise the victimized computer and acquire operating system privileges for further attacks. Once Internet users become attacked, CryptoFortress virus may pop-up decryption site to inform victimized users the computer has been infectious, and they have to pay the decryption software for recovering all files. The decryption website may guide victims how to purchase the decryption software, victimized users just need click one by one. Just refer to the CryptoFortress virus decryption interface as following.
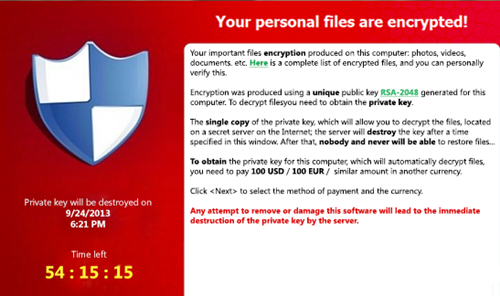
TeslaCrypt is a new type of ransomware that severely affects users’ PCs while encrypting personal files with state of the art hack technology. One of the main disrupting skills TeslaCrypt adopts is leading Windows screen locker that usually appears to users in the form of a bogus notification on the monitor, forcibly limiting every regular PC routine for PC users. However, the precondition of the attacking activities by TeslaCrypt ransomware cannot be short of the rock-ribbed personal files encryption on a targeted machine. This may refer to people’s photos, videos, documents, etc. According to the announcement by TeslaCrypt scam, users can view the complete list of encrypted files through clicking “Show encrypted files” on the screen alert. The encryption algorithm used by TeslaCrypt ransomware is the Advanced Encryption Standard (AES), which has generated a unique public key for a targeted computer that can be used to decrypt all personal files stored on affected system, regardless of Windows 7, Windows XP, Windows Vista or Windows 8 in recent. To get the private key for decryption, TeslaCrypt threat generally demands victims to pay a sum of money about $500 USD in Bitcoins or $1000 USD in PayPal My Cash Cards.
Gamegogle.com is a malicious browser hijacker using classic tricks to get installed into the targeted computer without awareness. Gamegogle.com shows up suddenly in the browser, forcibly blocking the original browser homepage and replacing it with gamegogle.com. As the name implies, Gamegogle.com browser hijacker pretends to provide the most fun and exciting games for the computer users which turn out to be traps for them to get victimized. In most cases, Gamegogle.com could hide in the system background as some needful applications for the system performance so the users won’t shut it down in the first place. Under this circumstance, Gamegogle.com will have the opportunity to release tons of pop-up ads and links in the computer to dizzy the innocent users, luring them to click on those malicious links and led to specified sites for purposes of making more money from them.

Worm:Win32/Nuqel.BD is one form of hazardous computer infection that has interfered with lots of PC users’ regular system operation since the day it was programmed. It features state of the art hack technology that is updated by cyber criminals who strive to implement disruption a targeted PC for illegal purposes, such as data theft and money extortion. Having some similar properties like another newly-released Trojan.Win32.Agent.aldog, Worm:Win32/Nuqel.BD can often sneak into a user’s computer, regardless of the version of Windows operation system in use, without any permission or authorization. Internet users may get infected with Worm:Win32/Nuqel.BD threat when they download some distrusted freeware or shareware from Internet or open spam emails that carry malicious attachments.
Search.Protectedio.com has been pretended to be a beneficial search service for the computer users to have a protected environment while they are doing the searching. However, Search.Protectedio.com is actually a browser hijacker coming with an evil propose to victimize the innocent users and redirect them for those malevolent cybercriminals. In most cases, users could not notice the difference between regular safe search engine like Google Chrome, Firefox or Internet Explorer and the bad ones like Search.Protectedio.com, blindly using the browser hijacker for searching. Search.Protectedio.com could easily get the initiative to transfer the innocent victims to any dangerous website it wanted. Once the users get hooked by those unsafe sites recommended by Search.Protectedio.com redirect virus, things will get even worse. As most of the search results provided by Search.Protectedio.com browser hijacker are online shopping sites with tons of promotions, downloads, coupons, services, ads, links, etc. Search.Protectedio.com will lead the users to walk into traps that set up by the criminals.

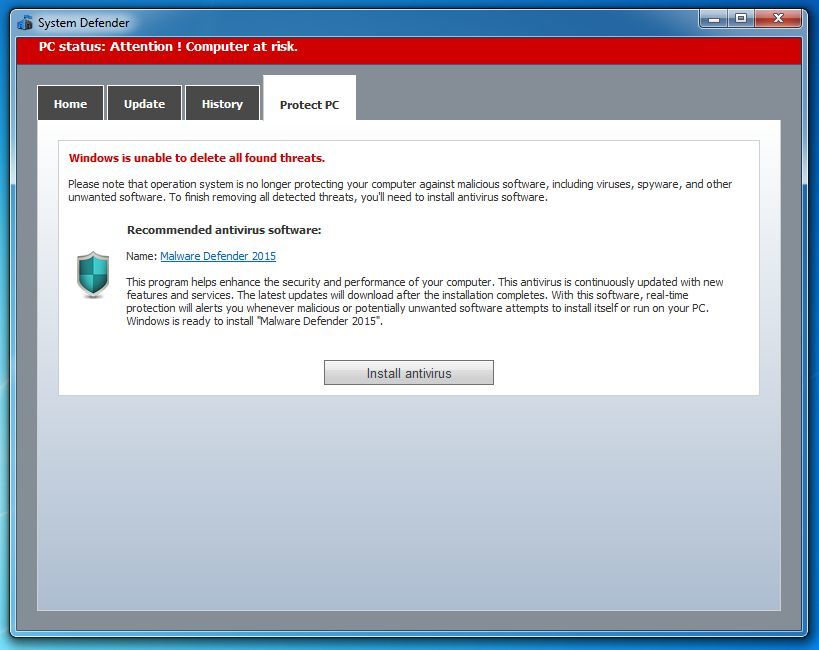
As virus gets wild, many anti-virus programs are created successively to help people surf safely and generate revenue at the mean time. Virus makers smell this chance to confuse the market by making rogueware like Malware Defender 2015.
To allure virus-tortured end users into purchasing the fraudulent anti-virus program, Malware Defender 2015 carries more tasks for easy money, according to the observation by VilmaTech Online Support, including:
Trojan.Win32.Agent.aldog appears to computer users as one form of invasive malware that is specifically programmed by cyber criminals for illicit purpose. It mainly affects Windows 32 bytes compatible PCs, especially those are lack of high security protection. Internet users often cannot notice the existence of Trojan.Win32.Agent.aldog only if abnormal symptoms are activated. This specific Trojan virus is endowed with up to the minute hack technology, capable of sneaking into a user’s computer without asking for any approval. Trojan.Win32.Agent.aldog may be delivered via bogus JAVA updates, compromised websites (eg. some peer-to-peer web pages), unknown Internet downloads, spam emails carrying activation code of the virus, etc. When installed and executed, Trojan.Win32.Agent.aldog would take advantages of its pre-generated codes to affect and modify default Windows system configuration, such as the MBR, one part of system that takes control of startup items.
Istart123.com has been categorized by computer security company as browser hijacker that usually changes default browser settings without consent and suddenly shows up at homepage.
Browser hijacker was originally created to drive traffic arbitrarily as the online business started to rage. Large amount of traffic could help gain high RIO and promote business. As the Internet develops, more functions of browser hijacker, especially the illicit ones, are discovered:

FessLeak Ransomware is a dangerous malware created by cybercriminals who have planed for a very long time to victimize targeted computer users and take away their money illegally. FessLeak Ransomware is a classic type of computer infection coming without awareness. When this malware successfully invaded into a targeted computer it will forcibly lock up the computer, showing the users with a terrible notification as a threat to tell them their important files were encrypted. FessLeak Ransomware also asked for a $100 ransom for unlocking the computer and decrypting the files. In fact, all this drama is fake and bogus, it is just a lame excuse for evil cybercriminals to take money from the innocent users. FessLeak Ransomware is a horrible infection causing system locked-up situation to freak the users out so they will compromise and pay the money as FessLeak Ransomware required.
Websearch.searchtheglobe.info is categorized as browser hijacker that directs people to undesirable websites. According to the close observation by VilmaTech Computer Security, some typical symptoms and problems are now listed for reference and early detection: