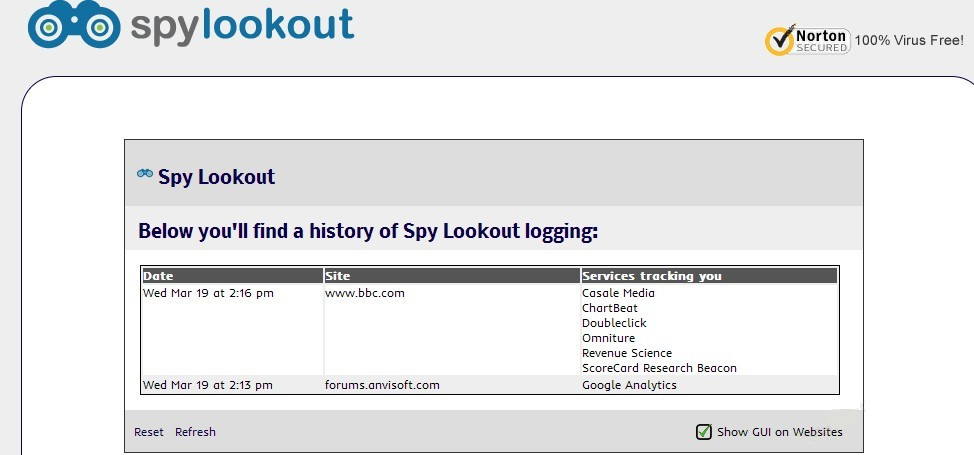
Spy Lookout adware was a self-dramatizing web service which promised the users to spy on malicious pop-ups so as to be on guard against unexpected attacks. For this reason, when the users suddenly found the Spy Lookout adware installed in the computer system, they could not realize that was not good. Most of the innocent users thought it was good to have a free safeguard looking out for the Internet environment. In this case, Spy Lookout adware would easily get the opportunity to display all kinds of unwanted pop-up ads, banners and sponsored links instead, completely fooling the innocent users. As the Spy Lookout adware has already gained the trust from the users so they did not reject the ads and blindly clicked on those unknown ads links and went for a visit without scruples, falling for the traps without knowing.
HEUR.Trojan.Win32.Generic has been reported by numerous security utilities as a specific Trojan infection that can invade the targeted computer without PC user’s agreement. Similar as other Trojan threat, HEUR.Trojan.Win32.Generic is often being delivered by certain software shared on peer-to-peer networks. Users may also have the possibility to get infected with this malady while navigating to an image, screensaver or archive file attached to an e-mail message. In this way, hackers will leverage obfuscated JavaScript connected to their controllers so as to determine all possible exploits on affected machine for further destruction. Upon its installation, this type of Trojan infection will immediately drop its malevolent codes and files in system for the purpose of making modifications to the Windows registry.
Win32/VB.CP is compatible with all sorts of Windows Operating systems such as Windows 7, Windows XP, Windows 8 and more, is a new version of the notorious Trojan virus which enables targeted Internet users’ computers to work in a dangerous situation, belongs to the family of malware threats frequently used by hijackers to compromise the Internet users’ computers and steal confidential data from them. Win32/VB.CP Trojan virus engages in attempting to steal confidential information from the infected system by self generating configuration downloads and using Trojan-building toolkit. Once the targeted machine compromised, the Win32/VB.CP Trojan virus opens a very possible access allowing hijackers completely take control of the infected system and implement maliciously stealing activities what they desires. Win64.Patched.B.Gen Trojan virus similar to Win32/VB.CP.
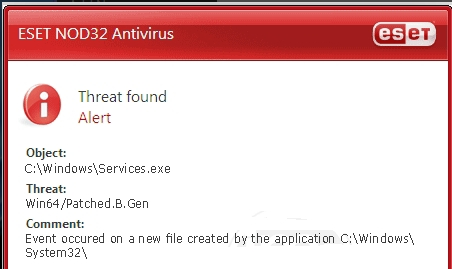
Win64.Patched.B.Gen carries on plaguing PC users and making money thereby in the wake of Win64:Patched-A [Trj]. According to the files and folders (C./Windows/system/user32, c:\Windows\System32\services.exe and C:\WINDOWS\system32\winntddu.dll) flagged by installed anti-virus programs, it can be told clearly that Win64.Patched.B.Gen affects system files. Thus problems listed below emerge to surface:
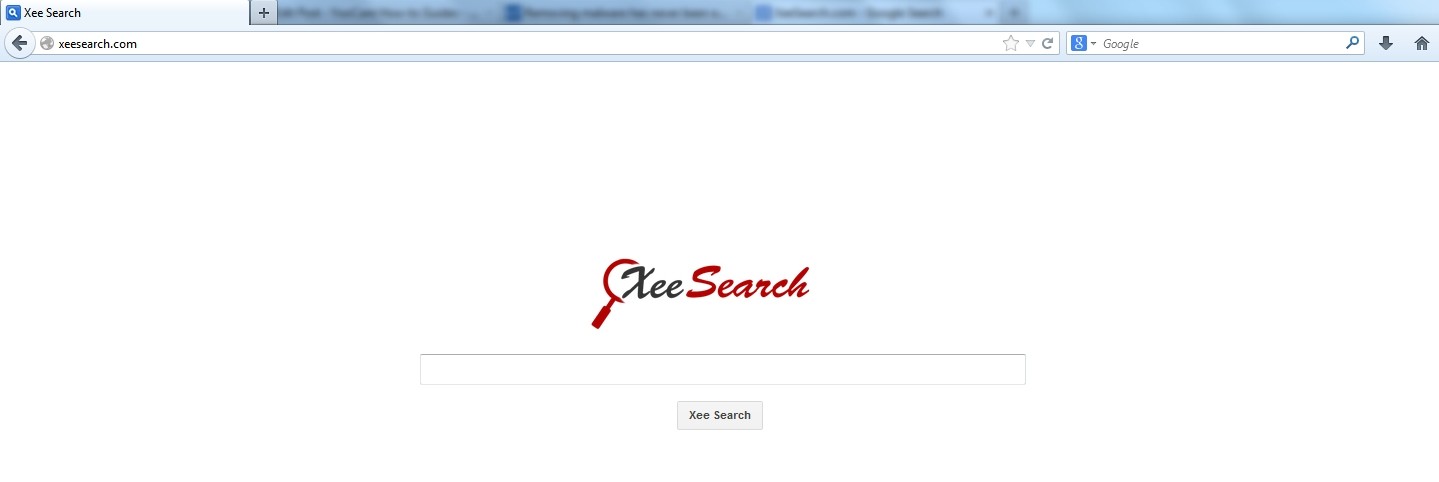
XeeSearch.com is a distrustful website categorized as a browser hijack virus, which might be used by cyber crooks to boost website traffic and benefit from pay-per-click technique. For the purpose of increasing its illusion, XeeSearch.com browser hijack virus provides a bogus search engine called “Xee Search” that seems to be similar as standard ones such as Yahoo, Google or Bing. However, by modifying default JavaScript, this infection may redirect search queries to various deceptive domains operated by malware distributors while using search engines. By default, one emblematic symptom of XeeSearch.com redirect virus should be the modification in a web browser’s settings, regardless of IE/Chrome/Firefox. The changes triggered by XeeSearch.com infection often happen surreptitiously without user’s authorization or knowledge. In consequence, this browser hijack virus may be able to replace the existing home page, start-up page or error page to its malicious URL based on XeeSearch.com.
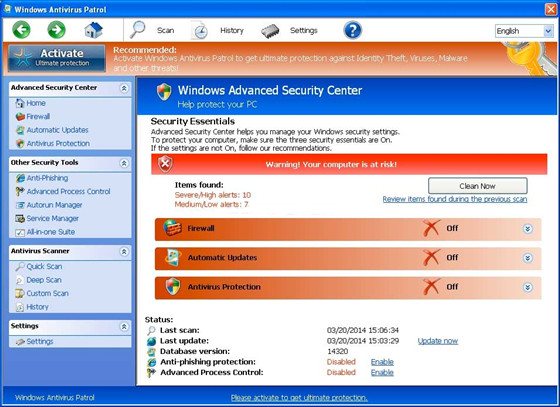
Windows Antivirus Patrol appears to be a useful anti-virus program but the real truth is not. The true nature of the Windows Antivirus Patrol is perilous, classified as rogue security program, a sort of computer infection referring to the so-called Rogueware or FakeVimes that focuses on attacking online users’ computers. Windows Antivirus Patrol fake anti-virus program engages in tricking money by displaying fake scan results, fake security warnings, and bogus errors. And it informs victimized users their computers have a lot of malware threats such as worms, Trojan virus or ransomware, thus compelling victimized users to buy the certain full version of the Windows Antivirus Patrol fake program. Besides that, the Windows Antivirus Patrol rogue antivirus disables all programs installed on targeted machine and makes victimized users lost abilities to take control their computers. Windows Antivirus Patrol rogue antivirus executes a bogus scanner on the infected machine, and deceitfully inform users their computers are in high-risk of malware attacks. And then the fake program recommends targeted users download a non-existent licensed version of Windows Antivirus Patrol. Refer to the screenshot of the Windows Antivirus Patrol rogue anti-virus program
Glomatron was an unwanted web service which often recommended itself by displaying strange pop-ups on the targeted computer, drawing user’s attention and intending to get the installation permission by cheating. Sometimes, Glomatron could also get installed in the computer without authorization, just being bundled with other software and downloaded together with them. Once the Glomatron adware successfully had its way and got the ticket of invading into the computer system, innocent users would surprisingly find a mass of hyperlinks and pop-ups displaying in the computer and the browser voluntarily. Purposive Glomatron adware could lead the innocent users walking into traps, even the nonstop pop-ups were kind of annoying, the users were still easily tempted by those advertising contents, willingly clicking on those Glomatron ads links so as to learn more about it. In this case, the innocent users could naturally become the victims who would be in danger of being victimized by cyber scams.
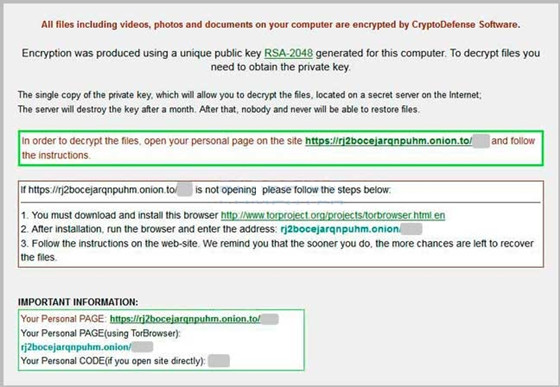
The end of February 2014 turned out perilous CryptoDefense Ransomware epidemic in cyber world. Work focuses on attacking Internet users’ computers and encrypting all data files in order for extorting a $500 USD ransom in Bitcoins from targeted computer users. Quite a few Internet users are attacked by such CryptoDefense Ransomware and until now have always left those victimized users with no way out, other than paying the extortion demand to decrypt their files. Now let’s have a look at what actually happens to the victimized machine and Android phone that attacked by CryptoDefense ransomware and how to decrypt files and remove it completely. Read on, please.
![Remove Win64:Dropper-Gen[Drp]](https://blog.vilmatech.com/wp-content/uploads/2014/03/win64-dropper-gen.png)
PUP.Optional.FindBestDeal.A technically refers to a PUP (or potentially unwanted program) that may be undesirable for users. According to recent security statistics, numerous Microsoft security utilities have detected PUP.Optional.FindBestDeal.A as a specific detection, capable of generating damaging activities on a victim’s computer. By default, it cannot absolutely judge if a PUP is malevolent or positive for user’s computer, as it may have the possibility that users consented to download it. Nonetheless, PUP.Optional.FindBestDeal.A is considered as a destructive threat for users on the basis of its apparent attributes. For instance, this type of PUP can often invade a targeted computer using found system vulnerabilities to bypass user’s authorization or knowledge. It may arrive as other malware’s payload, which has the capability to surreptitiously drop and install the components of PUP.Optional.FindBestDeal.A in PC. To spread its codes widely, PUP.Optional.FindBestDeal.A is often downloaded in conjunction with a program that the user wants.