The process BcHelper.exe usually is attributed by Blabbers Communications LTD, attached to the Browser Companion Helper. Once you have mistakenly deleted some its relevant program files or system registry entries, your computer may always pop-up such bcHelper.exe error to alert you. Many computer users may suppose bcHelper.exe is a virus like Trojan virus/spyware/malware, and the truth is that it is not. But, if you always leave the bcHelper.exe error unchecked, it will result in a lot of troubles on your computer as time goes by. Even more the virus makers can utilize such bcHelper.exe error to exploit increasingly malicious traits to filtrate on your computer. To definitely fix the bcHelper.exe error problem and avoid any future troubles, you may follow the below tips.
Information Security and Control Act message is a counterfeit one that attaches Garda (Irish police) logo in the corner of the screen and an email address with the name resembles the genuine one to make it look official. Such fake message raged in 2012 and has cheated wide range of PC users and Android phone users into submitting a fine of 100 Euro to release it by sealing the whole screen. Legal as Information Security and Control Act virus Android lock looks like, it is a form a virus, which is identified as ransomware, supported by Trojan. With the help of typical technique of a Trojan, Information Security and Control Act virus manages to display the counterfeit page with corresponding language, governmental departments according to the detected IP address and the language of the target system. In other word, Information Security and Control Act virus Android malware is capable of extracting personal information of victims.
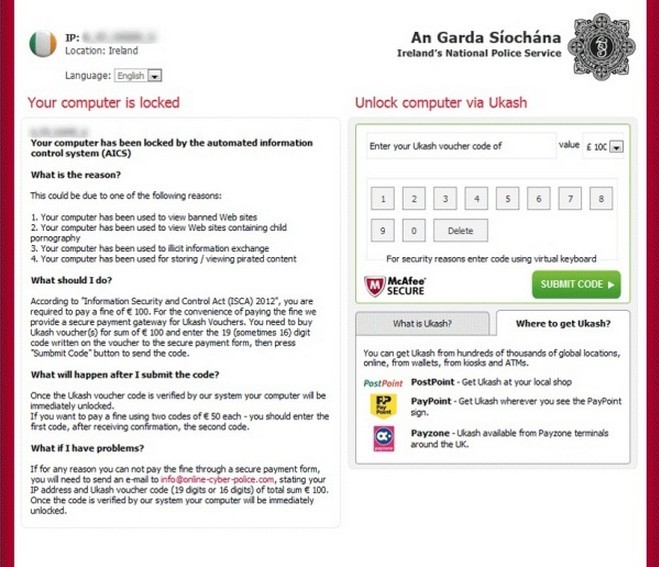
(The most widely seen version of Information Security and Control Act virus)
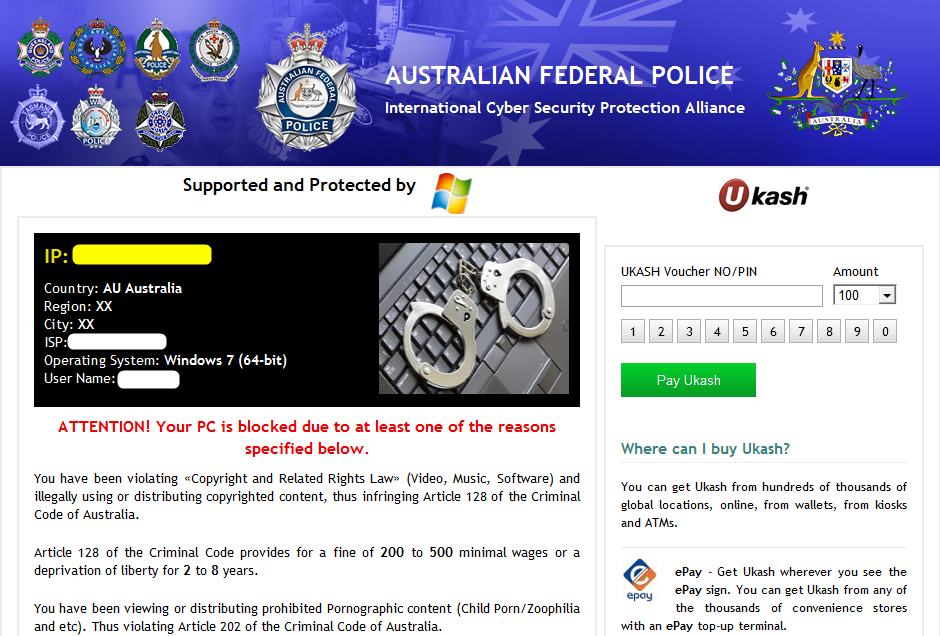
What a weird sense could be if receive a warning information from the computer or Android phone, telling you that “Your PC is Blocked”. Does this strange message ring any bells for you? Yes, that is the exact fake message delivered by the recently appeared Australian Federal Police virus. The idiomatic trick of this shameless ransomware is pretending to be coming from the federal police so that to increase its own authority and reliability which can be persuasive and mandatory for the vast number of the Internet users. Being all dressed up with the official police logo and the national flag design, the cunning Australian Federal Police virus forcibly locked the user’s computer screen, accusing them of breaking the “Copyright and Relayed Rights Law” in a formal tone, and requesting for a 100 dollar fine within 72 hours, otherwise, will be seriously punished by law. That’s definitely a terrible treaten, users should take the time to remove this Australian Federal Police Android Phone Virus as soon as possible.
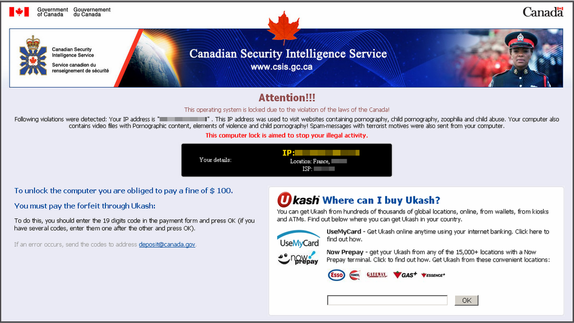
CSIS Ukash Virus Android virus is malicious ransomware, purportedly attributed from Canadian Security Intelligence Service, but in fact it is created by cybercriminals to lock user computers in order for blackmailing unwary users’ to pay a fine of 100 or 200 Dollars. The scam CSIS Ukash virus Android malware disguises high-authority enforcement agency in Canada to send out full screen warning on user computer that locks. It then accuses of those victims have been violating copy-right and related laws like distributing copyrighted media, child pornography, and using unlicensed software. The key point displayed on the CSIS Ukash virus locked screen is that those victims have to pay a fine in time to unlock the infected computers or Android phones. Otherwise, there a criminal case will against them and they have to be in jail for years. Many computer users are scared and at nail-biting what to do just when they see such alert warnings. Suppose that victimized computers or Android malware can be unlocked once they pay the demanding fine in the form of Ukash or PaySafeCard code. Unfortunately, the fact is that CSIS Ukash virus still locks their computers. Therefore, don’t be taken in, cybercriminals usually use the common trick to get computer users and Android phone users been trapped in.
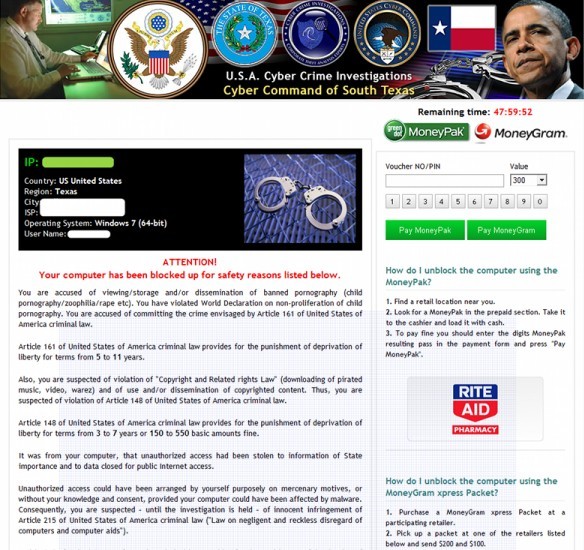
U.S.A. Cyber Crime Investigations virus Android malware is classified as ransomware that was originated from Eastern Europe. As it is known to all that Cyber Crime Investigations virus used to affect Canadians. But here comes a newly found lock down virus that targets PC and Android phone users in Unites States specifically.
Search.conduit.com, also known as Search Conduit virus and Conduit engaging people virus, has been recognized as a notorious browser hijack virus that mainly attacks Windows operating system. As a hack tool created by cyber criminals, Search.conduit.com can be used by hackers to boost website traffic on your various browsers (eg. Internet Explorer, Mozilla Firefox and Google Chrome) and benefit from the pay-per-click technique. Being covered with a bogus search engine, Search.conduit.com virus pretends to be a legitimate and practical website, offering the similar search service like Yahoo, Google or Bing. Instead, Search.conduit.com is nothing but a harmful redirect virus that we need to eradicate. Overwhelming majority of PC users cannot pick up the precise time when the Search Conduit virus is installed on target machine.
The birth of ZeroAccess virus can be traced back to the year of 2009 when the first ZeroAccess was found in the Internet world amid the epidemic of MBR rootkit and TDL2 rootkit. TDL2 rootkit was the most advanced kernel-mode rootkit until an uncharted rootkit was accidentally found by security researchers. The uncharted rootkit, which is later known as ZeroAccess, was capable of disabling most of the security utilities that managed to scan specific folders back then. The rootkit created a new kernel device object named __max+> to help itself become notorious in the Internet security world. After studies on ZeroAccess virus, it had been found that the rootkit would put its codes into two spare data streams win32k.sys:1 and win32k.sys:2. To escape detection, ZeroAccess would disable any security utility that attempted to scan the two streams. Besides, it would create some counterfeit directories by adopting NTFS technique in a bid to take users as well as security utilities to the phony rootkit device. From then on, ZeroAccess virus began its ceaseless development to change the infection way, making itself more progressive and aggressive.
Babylon Toolbar is an extension of Babylon’s translation software, which has been widely indentified as a notorious browser hijack virus. Babylon software is a computer dictionary and multi-task translator, developed by an Israeli public company – Babylon Ltd. It is used for translation and conversion of currencies, measurements and time, and for obtaining other contextual information. Ignore the allowable functions, Babylon program has been complained by numerous PC users about its related add-on, Babylon Toolbar. Traced back to 2010, Microsoft antivirus products identified Babylon Toolbar as a nasty Adware: Win32/Babylon infection before, which made damage on various browsers seriously. Till now, Babylon Toolbar problem is still a headache for large amounts of PC users.
In some cases, Babylon Toolbar can be installed at the time PC users attempt to install Babylon’s translation program, it may offer an option for users to allow or reject. But, Babylon Toolbar can be lurked into one machine through other approaches without any awareness of owner. For example, the toolbar may come bundled as an add-on with other free software downloads as well as the P2P torrent clients or some shareware/freeware websites; Babylon Toolbar may be activated via clicking on unknown attachments in Email; it can be spread by the usage of mobile HDD (mobile hard disk drive). Meanwhile, it is possible to get Babylon Toolbar through visiting malicious web sites or the legitimate sites that have been attacked by Babylon virus. Thus, PC users should keep cautious while utilize any unreliable resources.

Websearch.relevantsearch.info is notorious as a browser hijacker by redirecting user to some specified websites which are corrupted by virus and definitely dangerous. After successfully getting into user’s system and modifying their default settings, Websearch.relevantsearch.info turns in a practical search engine, every time when user wants to do some queries, it will show up by default, with intent to induce more and more users to fall for the trap.
Websearch.relevantsearch.info virus is a typical online attack. In most cases, users got infected with it by downloading freeware or software from unsafe sites. Websearch.relevantsearch.info virus can be packed with those malicious programs, loading into the innocent computer system along with them. With it installed in the compromised computer, the most obvious feature is that user’s current homepage will be replaced to some malicious pages with no awareness. And some new toolbars or favorites will be installed in the browser as well, providing user many strange unwanted links. If keep going, it might find it weird that some safe sites have been blocked which can no longer be accessed anyway. Meanwhile, endless ads will appear on the computer screen automatically and constantly, which is so annoying and seriously affect the internet users’ activities. Hackers can easily control the browser with the help of Websearch.relevantsearch.info virus, modifying system settings and virus daemon without user’s permission, the purpose is to make the compromised computer system become increasingly weak. Afterwards, network security will be seriously threaten.
A plenty of computer users have discovered recently, that Websearch.searchrocket.info redirect brings corruptive damages, and so it is regular, malicious openings. Within the first past of this month, a series of variants of Websearch.xx.info browser hijackers are achieving successively release to attack user computers. Just like the previous redirect virus “Web.longfintuna.net redirect” invades into target computer without any consent. Websearch.searchrocket.info redirect virus screenshot, you can see as below.