Win32/Alureon.gen!A is one of the variants of Alureon Trojan that features itself with online data-stealing capability. Therefore, once a computer is attacked by the Trojan Rookit, chaos on browsers would break loose, such as new tabs keep opening with junk websites including some other search page instead of intended web pages. Obviously, Win32/Alureon.gen!A is a Trojan horse that intercepts system’s network traffic for usernames, passwords and credit card data and that mainly designed to attack 32-bite system.
As a generic Trojan horse and a tool to help cyber criminals collect confidential information, backdoor program is injected into Win32/Alureon.gen!A for the convenience of inspection, improvement and access in future. As a consequence, additional infections could be brought in by Win32/Alureon.gen!A if there are other resources that are needed by other siblings; extra affections could happen if the backdoor program is captured; unsolicited access could be realized to directly control the infected machine. It is clear now that Win32/Alureon.gen!A threatens not only information security but also computer health and that it should be removed as soon as possible. Below is the instruction to show how. Should you run into any difficulty in the middle of the process, you are welcome to contact VilmaTech Online Support and get expert help for quick fix.
A – run full scan and note down the path of Win32/Alureon.gen!A.
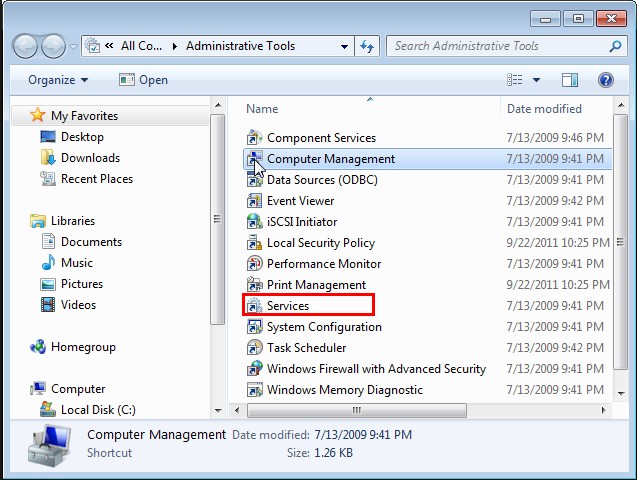
B – use Task Manager and System Information to locate and end the services as well as processes related to Win32/Alureon.gen!A.
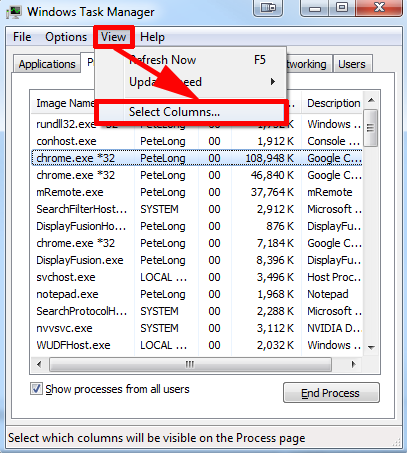
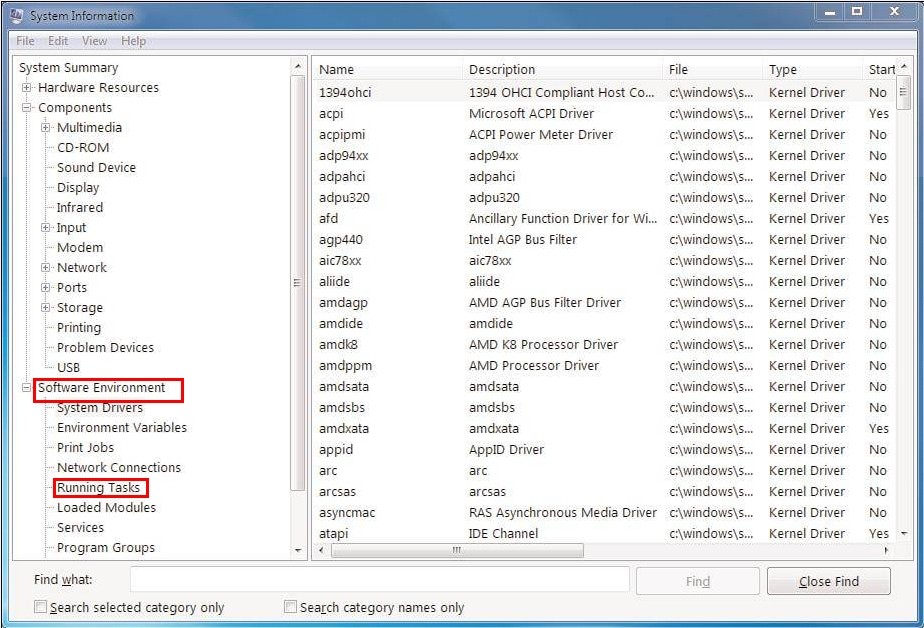
C – end the above detected service in Service function.
Windows7/vista/XP
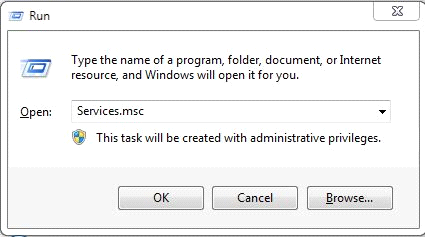
Windows 8
D – access Database to find the guilty services and remove all the affiliate values.

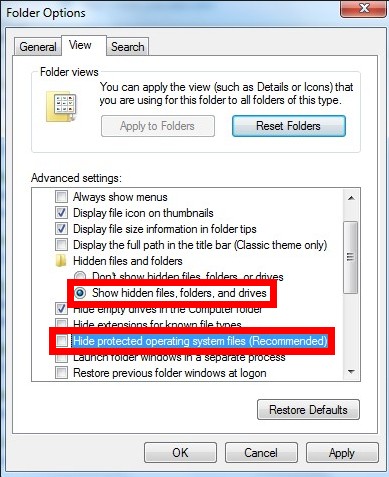
E – show hidden files and folders to remove the items generated by Win32/Alureon.gen!A from local disk.
Windows 7/XP/Vista
Windows 8
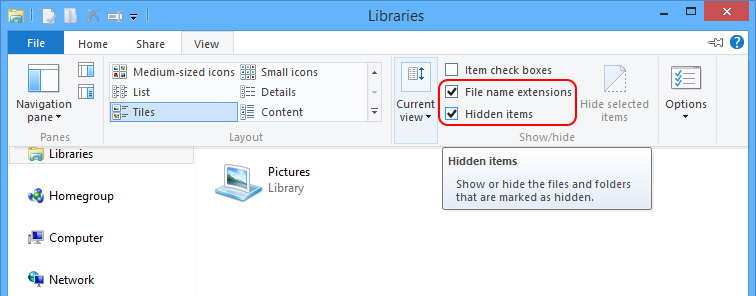
Remove the following given files/folders to remove Win32/Alureon.gen!A.
- Files named after Win32/Alureon.gen!A and some files named with random letters and numbers under C:\windows\winstart.bat, C:\windows\wininit.ini and C:\windows\Autoexec.bat.
- Items generated on the date when Win32/Alureon.gen!A was firstly found under C:\Windows and C:\Windows\System32.
(tip: Some path values have been replaced with environment variables as the exact location may vary with different configurations.
Being a Trojan horse, Win32/Alureon.gen!A has the capability of attacking vulnerability/loophole/backdoor bug. Therefore, conflict among installed applications, being redirected to some junk sites randomly or attacked by virus could finally result in Win32/Alureon.gen!A affection. As a matter of fact, Win32/Alureon.gen!A could bundle with rogeware which is what we call fake anti-virus programs. In sum, one should pay extra attention when surfing on the Internet and downloading/installing third-party programs.
Many practices have proven the fact that anti-virus programs and other security utilities are not able to remove Win32/Alureon.gen!A automatically. Though they said that Win32/Alureon.gen!A had been quarantined and cleaned, the Trojan horse kept triggering many more troubles and virus. One should be informed that the Trojan horse manages to numerate drivers concerning security service and overwrite data to prevent from automatic removal; inject vicious codes into background process such as explorer.exe to confuse security programs and manipulate searches without being picked up. Only manual remove method could reach complete removal and stop Win32/Alureon.gen!A from coming back. However, certain level of computer skills and knowledge is needed to differentiate the genuine items and the ones faked by the Trojan horse. Should there be any help request, please do feel free to get specialized technical help from VilmaTech Online Support.
Due to the random modifications by Win32/Alureon.gen!A and the backdoor program with the capability of introducing in additional items, many fragments can be found in the infected computer to hog CPU. Therefore, it is recommended to carry out defragment after the whole manual removal for a perfectly functioning machine. Here’s the video to show how.