TrojanDropper:O97M/Poshkod.gen!A has been recognized as hazardous malware called Trojan virus And it always attempts to attack online users’ computers in order for making money. By definition, the TrojanDropperO97MPoshkod.gen!A virus is supposed as a money maker, exploited by hijackers for confidential information-stealing. The perilous virus called TrojanDropperO97MPoshkod.gen!A includes a myriad of malicious codes aimed at exploiting system vulnerabilities to compromise your site and entice in more attacks such as worms, ransomware, spyware, or rogueware. The TrojanDropperO97MPoshkod.gen!A virus and built-in malicious rootkits can assure hijackers can collect confidential information from the infectious web browser and hard drives. In a word, the solitary goal of hijackers attacks users’ computers through such TrojanDropperO97MPoshkod.gen!A virus is to steal money and acquire malicious benefits by put confidential information participated in illegal commercial activities. The TrojanDropperO97MPoshkod.gen!A virus disable all programs on the infectious computer in order for stopping victim from taking measures to rescue their computers. How tricky the TrojanDropperO97MPoshkod.gen!A virus is.
Gnp.ciopt.net has been issued over the cyber world and draws increasingly Internet users’ attentions due to it can attack their computers and steal confidential information. The Gnp.ciopt.net redirect is regarded as hazardous security malware refers to the so-called browser hijacker, which aim concentrates on compromising PCs and acquiring malicious benefits by performing fraud tactics and collecting sensitive information. The Gnp.ciopt.net redirect affects a computer commonly through drive-by downloads. Especially when online users are downloading those potentially unwanted programs (bundled with Gnp.ciopt.net infection), at the same time, the Gnp.ciopt.net redirect virus can fast infiltrate on their computers without any consent The Gnp.ciopt.net redirect is designed to allow quick access to third-[arty programs, using tokens from an authorization server, could be added to users’ computers just via those intrusive drive-by downloads. And done with that, the Gnp.ciopt.net redirect virus can bypass any anti-virus detection.

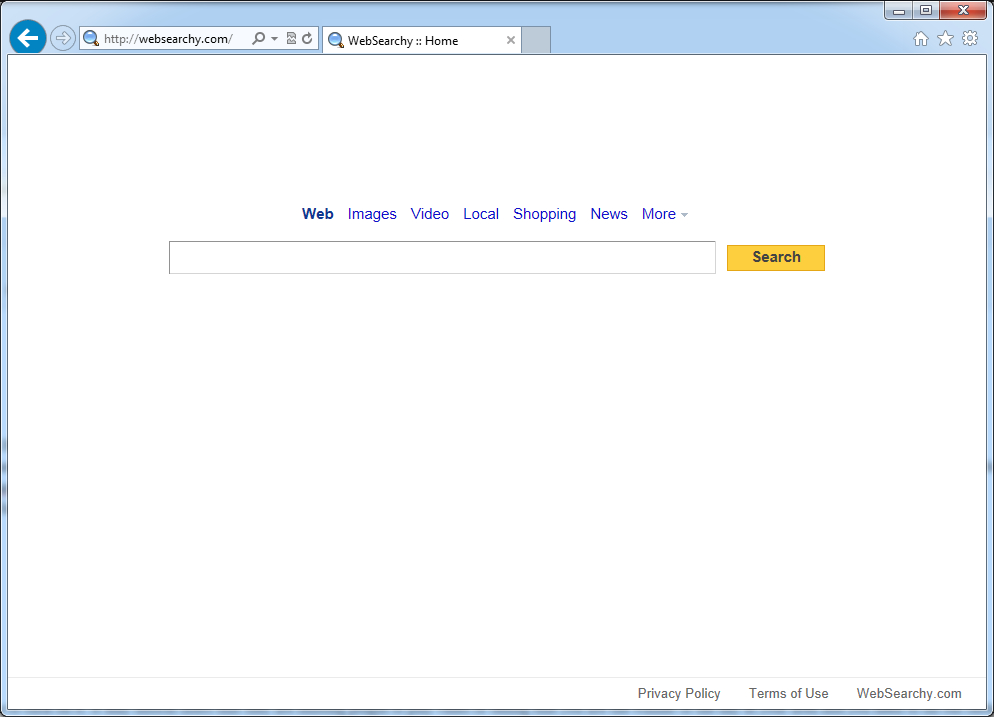
WebSearchy.com, a suspicious domain, has been identified as a PC security threat that belongs to the category of browser hijack virus. It seems to be a genuine website offering search engine serves for Internet users by intuitively distinguishing its interface. However, the counterfactual situation is, WebSearchy.com does nothing beneficial for users but may trigger a variety of destructive actions on the computer that it infects. Basically, WebSearchy.com browser hijack virus has a Trojan horse component or attribute, which will mislead users into installing it onto computer. It may be disguised as a browser plug-in or extension, typically toolbar that can be downloaded and installed in user’s web browser, despite of Internet Explorer, Mozilla Firefox and Google Chrome. Similar as other Page Jacking threat, WebSearchy.com virus may be able to propagate onto user’s computers surreptitiously by attaching its components to an email message, displaying as an image, screensaver or archive file. Users may also get infected with WebSearchy.com infection when they download certain software shared on peer-to-peer networks, carrying the malevolent codes of the virus.
Problem 1:
When searching the Internet, random pop up concerning a random tool bar or the like pay-per-click advertising websites appears; clicking the “X” will close out the popup but not stop the detection of Trojan:js/medfos.b.
Problem 2:
Going over to MBAM (Microsoft BitLocker Administration and Monitoring) and remove some detections will not stop Trojan:js/medfos.b, the quarantine won’t either.
Problem 3:
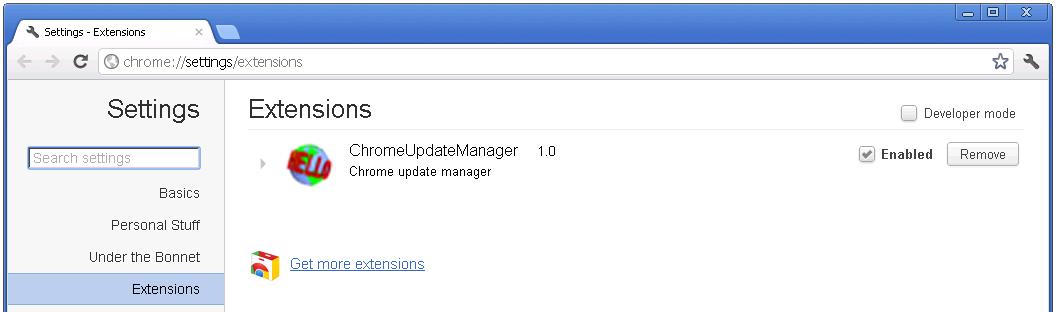
An extension called “ChromeUpdateManager 1.0” will be installed onto the installed browsers (IE, Firefox, Chrome, Opera) without permission to redirect search queries.
What makes PC users concerned is that alert about Trojan:js/medfos.b will pop up every five minutes no matter what has been taken against it. With that, the overall PC performance is degraded a lot to result in freezes sometimes and unstable CPU usage. The problems caused by Trojan:js/medfos.B should not be the very reason for PC users to remove it in a hurry, it is should be the dangers the Trojan horse brings.
W64.Viknok.B!inf virus unveiled damages that corrupt compromised system, disable all crucial programs, and allow hijackers accessing in to steal confidential information. The main goal of hijackers carefully designing such Trojan virus is to acquire malicious profits. To completely compromise the victimized machine, the W64.Viknok.B!inf Trojan virus must play with in their efforts to destroy system. The detestable thing is the W64.Viknok.B!inf virus can infiltrate on the targeted Internet users’ computers without any consent and tamper system files without malicious activities. W64.Viknok.B!inf virus usually breaks into one computer through driver-by download. This implies that W64.Viknok.B!inf virus can be bundled with freeware, shareware, or other web plugins. Just when Internet users are downloading those potentially unwanted downloads, the W64.Viknok.B!inf virus hidden within them then will fast slip into system without need of user’ permission. Besides that, fishing site, spam emails, intrusive pop-ups and more are the commonplace fraud tactics frequently exploited by hijackers to propagate security malware, as doing so the W64.Viknok.B!inf virus can install on the targeted machine without any distraction.

According to its name, it is obvious that storage.conduit.com (www.storage.conduit.com) has relation with search.conduit.com. Most PC users consider storage.conduit.com malicious as it:
Storage.conduit.com by itself is not malicious at all. It is no more than a browser hijacker to intercept traffic with which it manages to help promote other products of its creator’s. As a matter of fact, there are many browser hijacker utilized by online operators to perform Internet marketing, for example, Babylon.com, key-find.com, search.yac.mx and istart.webssearches.com (read more), etc..
There are basically two techniques to build a web application (including a web site and adware), they are BHO and JS respectively. Generally speaking, the two are commonly seen in Internet world and it is easy to apply into practice. However, some skillful operators see something special out of them.
JS:Downloader-ZY [Trj] is one type of malware that can be subdivided as a Trojan infection carrying malevolent codes. PC users have criticized JS:Downloader-ZY [Trj] a lot because it has the capability to trigger damaging activities on the computer that it infects. As a matter of fact, JS:Downloader-ZY [Trj] virus is a hack tool utilized by cyber criminals for illegal subjects. Most commonly this type of Trojan threat can always sneak into a targeted computer without user’s permission or knowledge. The common spreading approach JS:Downloader-ZY [Trj] adopts is exploit kits, such as BlackHole, which are capable of infiltrating user’s computer using found security vulnerabilities. Apart from the basic method, the infection is also skilled in making full use of social engineering tactics in order to propagate its harmful components.
A new version malware on Trojan-PSW.Win32.Dybalom.L is infecting increasingly users’ computers over the cyber world – so much that some Windows Operating Systems are compromised by it as the Trojan-PSW.Win32.Dybalom.L virus is carefully crafted and compatible with any OS. Is the Trojan-PSW.Win32.Dybalom.L virus as bad as Rootkit.Win32.Zbot.sapu virus? Definitely yes. Trojan-PSW.Win32.Dybalom.L virus is regarded as perilous Trojan virus, carefully crafted by cybercriminals aimed at tacking online computer users and stealing money even confidential data there. Trojan-PSW.Win32.Dybalom.L Trojan virus is a seriously corruptive virus within any sort of operating system including Mac OS, has ability to make the victimized computer totally vulnerable for more malware enticing in by constantly exploiting vulnerabilities. Trojan-PSW.Win32.Dybalom.L virus’s vulnerability could be exploited just by requests to un-patched servers, which allows hijackers to intercept secure communications and steal sensitive information. Trojan-PSW.Win32.Dybalom.L virus, affects the targeted computer without any consent due to it can conceal existence by being bundled with third-party programs such as freeware, shareware, web plugins, and add-ons, which refers to the so-called potentially unwanted programs ( driver-by download).
Mostshinstar.com was up to no good for the Internet users. Once it got installed in the targeted computer and took control of the browser, users would receive tons of pop-up ads and links from Mostshinstar.com showing in the browser autonomously, constantly bothering their online activities and work. Mostshinstar.com displayed all kinds of pop-ups to the computer users, intending to draw their attention and encourage them to click on those pop-ups and links, so they would be naturally led to specified websites. Most of the pop-ups provided by Mostshinstar.com were pointing at some advertising sites similar to some kind of online shopping sites. Innocent users could easily be confused by Mostshinstar.com with all the tempting commercial advertising information showing in front of them, so when they blindly browsed those unknown and unsafe sites recommended by Mostshinstar.com, they could be trapped with various deceptive offers from those fraud sites, eventually leading to huge losses.