Boot.Cidex is a type of Boot Sector virus, which is regularly propagated by mobile HDD (mobile hard disk drive) /removable devices such as USB memory stick or floppy disk. By default, Boot Sector serves as a gathering place to store hard disk, floppy disk, optical disc or other data storage device for the sake of controlling the operating system’s boot loader. Master boot sector comes out as the first sector of hard disk which has is responsible for split control table and coding of the operating system. Those surplus 16 or more system sectors apart from Master boot sector are commonly unused. Hard disk drive can be maximally divided into four storage partitions and extended partition of disk operating system can be subdivided into multiple logical drives.
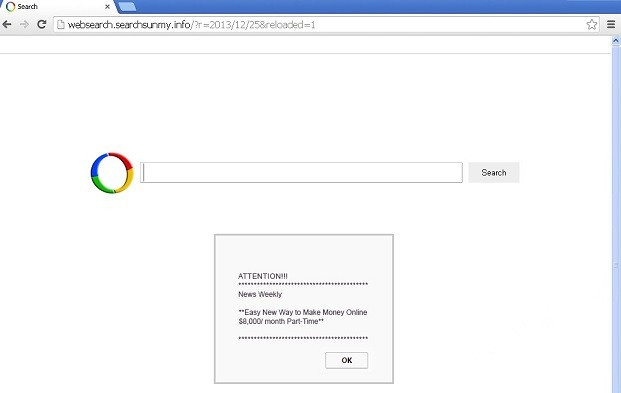
Websearch.searchsunmy.info has now confirmed to be a tricky browser hijacker modifying the default settings without permission. Once infected the targeted computer, it would hijack user’s favorite homepage and change to Websearch.searchsunmy.info. When the users open the browser for a searching, this cunning hijacker would successfully fool the innocent users to use it as the original search service. Under this circumstance, the purposive hijacker would have the authority to redirect the users to any website it wanted, totally blocking the regular search results and hiding so well from the ignorant users. In this way, forcing the users to browse the specific sites, Websearch.searchsunmy.info would pretend to be a beneficial service and make a profit by itself.
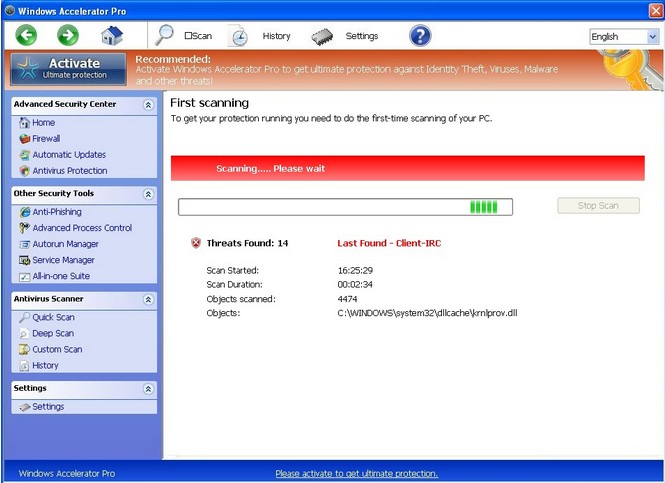
The Rogue.FakeVimes family keeps producing new fake anti-virus programs recently with same interface yet different names. Among its variants, Windows Premium Shield and Windows Efficiency Console are the two most notorious known by VilmaTech Research Lab. By comparison, features including anti-phishing, advanced process control, autorun manager, service manager and all-in-one suite are still maintained on Windows Accelerator Pro.
It should come to your knowledge that system.exe is one of Windows components. Yet more system.exe issues are coming forward since virus, especially elusive Trojan, manage to generate running progress with the same name so as to confuse the computer for the evasion from being detected. Considering the same name system.exe regular process and system.exe vicious progress share, VilmaTech Research Lab offers the most workable way to make differentiation between them by simply accessing Task manager. Navigate to Process tab to find items named system.exe with more than zero CPU usage. If any, you are affected by system.exe virus and possibly hidden Trojan that hasn’t been yet detected.
PC Optimizer Pro claims to be an omnipotent system utility, which serves as an integrated system optimization or registry tool primarily concentrating in cleaning redundant windows registry files and fixing system errors to prevent from PC crash. On the basics of its properties, PC Optimizer Pro is promoted to optimize windows’ performance through technically removing unnecessary files and compact wasted space. It also can be utilized by users to remove detected spyware and erase navigation tracks to ensure user’s privacy. Nonetheless, according to users’ feedback, the PC Optimizer Pro application has been identified as a detrimental anti-spyware program or unwanted program which required to be uninstalled from PC due to its abnormal symptoms.

Responding to a mass of security threats propagations and continuously compromises of web browsers, fraudster encompassed hijacker and cybercriminal syndicates concentrate on designing cyber threats at large. Just like the Updatesoftnow.com, is referred to the so-called browser hijacker, work centralizes in modifying online users’ web browsers’ settings, replacing the existent or default homepage, error page, and search engine with its own. The commonplace is the scammers frequently utilizes Updatesoftnow.com browser hijacker virus for obtaining benefit from pay-per-click techniques and increasing its advertising revenue. Furthermore, the hijacking Updatesoftnow.com uses unethical tricks to entice online users into being trapped.
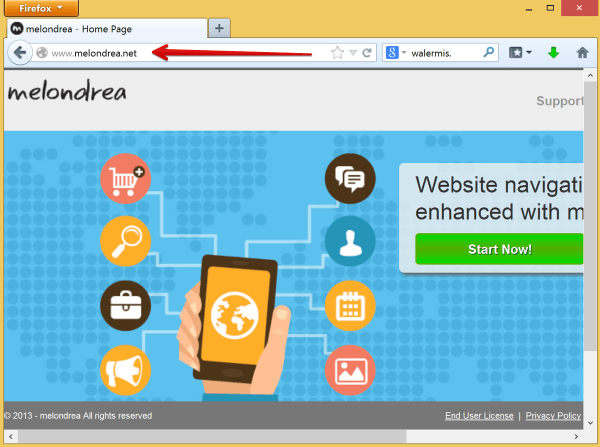
Melondrea was verified as a deceitful adware infecting user’s computer in improper ways. Once it successfully stationed into the browser, it would modify the default settings and replace the original homepage, misleading users to its purposive site melondrea.net. In this way, this cunning adware would have the opportunity to transfer the ignorant users to various advertisements sites and achieve its desire. Most of the advertisers would take advantage of Melondrea adware so that to promote sales and make profits. In the case of mutual benefits, the premeditated adware would draw users to browse specific websites and coax them to purchase the goods, the more the better.
Futurro Antivirus is categorized as the so-called fake program (rogueware), which work concentrates on advertising itself as high reputable security software and entices online computerusers into buying its “licensed” version, so by this way it can obtain money from them. In reality, Futurro Antivirus just exploits a tactic that frauds money by using the disguise of security tool and catching the pretense of helping user rid of detected malware. Actually, the Futurro Antivirus has nothing to do with genuine reputable anti-virus program. The solitary goal for fraudsters designing such fake virus is to fool those unwary computer users and pilfer money from them. The mainly unethical measure is to mislead victimized computer users into thinking they have serious PC problems and pay for the full version of Futurro Antivirus is necessary.
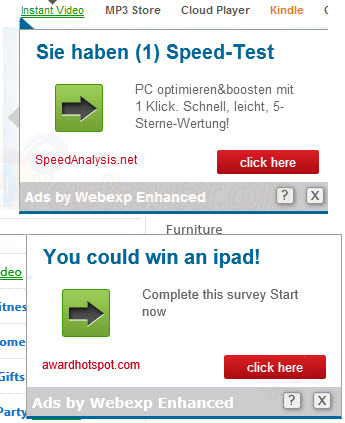
Webexp Enhanced is a purposive adware with the main mission to display all kinds of tempting pop-up ads in the targeted computer, drawing the innocent users to click on the ads links and leading them to various advertisements sites it specified. In this case, the ill-disposed adware would have the chance to make exorbitant profits once the targeted users make a deal on the websites, purchasing the goods recommended by Webexp Enhanced. Because most of the pop-ups were so attractive and incredible, letting the masses of the users could not resist the temptation and want to click on it to satisfy their curiosity. However, what they did not know is that more and more safety trouble were approaching.
Its name suggests its origin is Rovnix, a type of Trojan that is mainly responsible for opening backdoor and weakening target machine to drop down additional associated Trojan. Such TrojanDropper has random variants such as TrojanDropper:Win32/Rovnix.A, TrojanDropper:Win32/Rovnix.I, etc., while win32/Rovnix.gen!B is the most intrusive dropper so far. The following list is hereby to allow quick knowledge about its damages being learned: