The end of February 2014 turned out perilous CryptoDefense Ransomware epidemic in cyber world. Work focuses on attacking Internet users’ computers and encrypting all data files in order for extorting a $500 USD ransom in Bitcoins from targeted computer users. Quite a few Internet users are attacked by such CryptoDefense Ransomware and until now have always left those victimized users with no way out, other than paying the extortion demand to decrypt their files. Now let’s have a look at what actually happens to the victimized machine and Android phone that attacked by CryptoDefense ransomware and how to decrypt files and remove it completely. Read on, please.
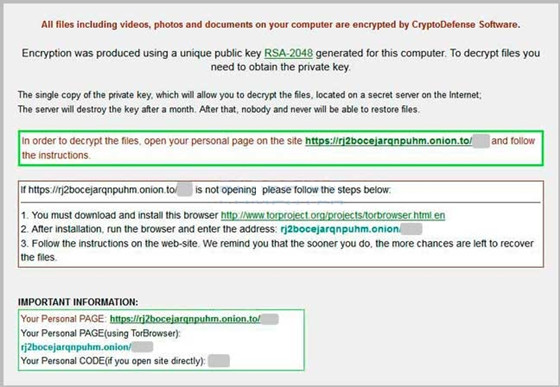
CryptoDefense is categorized as malicious ransomware, refers to the so called CryptoLocker virus that encrypts user files and won’t allow for restoring them unless the required fine reflected on the blocked page is paid. This sort of CryptoDefense ransomware can bring our serious consequence fro the infected PCs, which would outperform the common ransomware that blocks Windows only. CryptoDefense ransomware is in form of encrypting user files including video, photos, and documents on infected computer. And then declares victimized users can get their files come back by purchasing a non-existent private key. Furthermore, unlike the kind of ransomware which always disguises legitimate enforcement agencies, the CryptoDefense software comes on the infected PC immediately in no way conceals its true nature of extorting money.
As seen on the ransomware screen, the CryptoDefense software claims that users have to obtain private key for restoring those encrypted files. CryptoDefense software encrypts your personal files using asymmetric encryption so that you can get the encrypted files come back by using private key. To obtain the certain private key, victimized users have to pay the extortion fee of a $500 USD ransom in Bitcoins within 4 days. Once expired, victimized users will have to pay double to $1,000 USD. Furthermore, the CryptoDefense ransomware threatens users won’t have any key to restore their files any more if they don’t purchase the established decryptor within one month. And the required process is to install software from the malicious site: rj2bocejarqnpuhm,onion.to/. By installing software on the victimized computer, the CryptoDefense ransomware will entice in more malware and import in notorious adware in order for illegal profit-making.
The crucial thing is that although you have paid the required fine in Bitcoins in time, all encrypted files will probably be decrypted temporarily. This implies that the kind of CryptoDefense ransomware won’t be removed completely by paying a required fine. Instead, the CryptoDefense ransomware still in your computer can encrypt all files again soon. Therefore, don’t be taken in by such malicious virus. You’d better remove CryptoDefense as quick as possible. Otherwise, you have to suffer from serious damage between system corruption and personal files. Refer to the virus similar to the CryptoDefense ransomware.
Note: How to Remove CryptoDefense ransomware? You can consult more information by Live Chat with VilmaTech 24/7 Online Experts immediately.
CryptoDefense attacks Internet users without any consent, frequently infiltrated on target computer by drive-by downloads including spam emails, freeware, shareware or web plugins. By this way, the CryptoDefense ransomware can entice in user computer without any need of permission just while a download is ongoing. Once CryptoDefense ransomware compromised computer, it creates a random-named files to the root of AppData or LocalAppData path.
Beside that, it also designed malicious registry entries to ensure its activation every time Windows reboots and conceal its existence in infected system. Infected system resources then may be constantly consumed to slow down. Additionally, CryptoDefense ransomware will show number of threatening warnings, fake error message, and encrypted files.
CryptoDefense ransomware can scan all drives on the infected computer and acquire personal files for encryption. All files such as *.doc, *.docx, *.docm, *.xls, *.xlsx, *.xlsm, *.xlsb, *.ppt, *.pptx, *.rtf, *.psd, *.pdf, *.jpg, etc will be encrypted. Done with that, the hijackers can take advantage of it to extort money from the innocent victimized users.
The biggest difference is the payment should be in Bitcoin that has experienced some turbulent times in recent weeks as attackers concentrate on attempting to siphon off fine by it. Thousands of investor has been the targets of the CryptoDefense ransomware especially those investors. Because hijackers can encrypt their confidential files for extort money. And quite a few people among those investors have lost their deposits.
Want to counter the effect of this CryptoDefense Ransomware? Bring your infected computer to safe mode with networking while you restart Windows or actually hitting F8 key for getting there. Read on the next part.
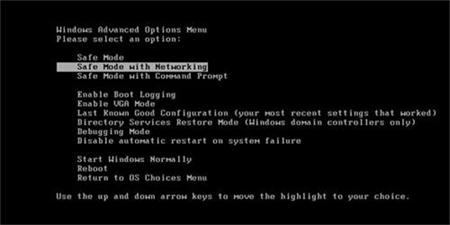
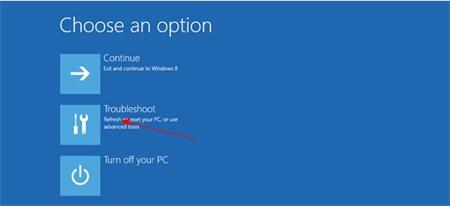
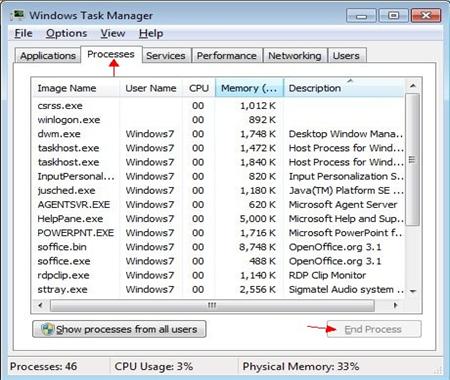
Delete CryptoDefense Ransomware files from Local disk. But you need show hidden files first.
Delete the CryptoDefense Ransomware registry entries.
1. Press Windows+ R key to reveal out Run box. Type regedit in Run window and click Ok.
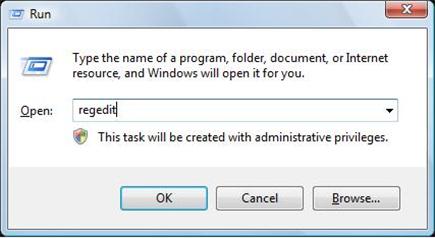
2. In the Registry Editor window, you need navigate to the below path. You then need to find out “Shell” and right click on it. Click on Modify.
3. The default value data is Explorer.exe If you see something else written in this window, remove it and type in Explorer.exe.
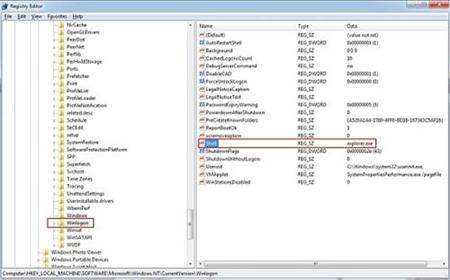
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\
4. Besides that, you still need delete CryptoDefense Ransomware registry entries, you can refer to the below registry entries.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\[random].exe
HKEY_LOCAL_MACHINE\SOFTWARE\ CryptoDefense virus
HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableRegistryTools’ = 0
HKEY_LOCAL_MACHINE \SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system ‘EnableLUA’ = 0
You need reboot the infectious computer with regular mode to active the CryptoDefense Ransomware removal.
Note: Still have troubles with completely removing such aggressive CryptoDefense virus files and registry entries? You may Live Chat with VilmaTech 24/7 Online Experts to get further help.
In case of any mistaken operation, you’d better backup files first, refer to the below video.
1. To restore from a restore point you will first have to navigate to the Systems Protection tab by typing “System Restore” in the Windows 8 Search bar.
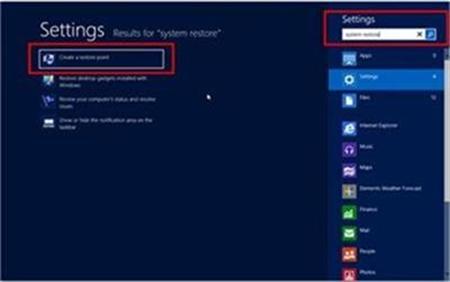
2. Open up the control panel and select “System and Security.”
3. Then select “Advanced System Settings.”
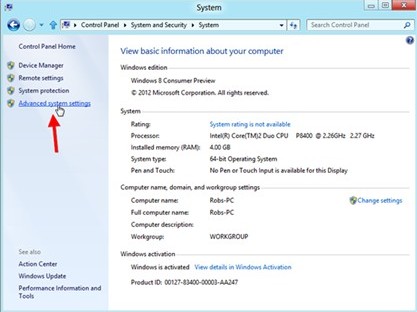
4. In the next window, click on the “System Protection Tab.”
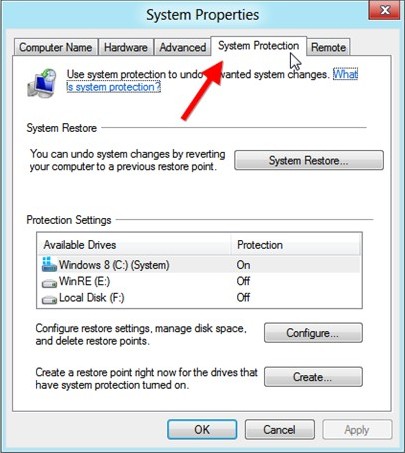
5. In the same window, click on System Restore button.
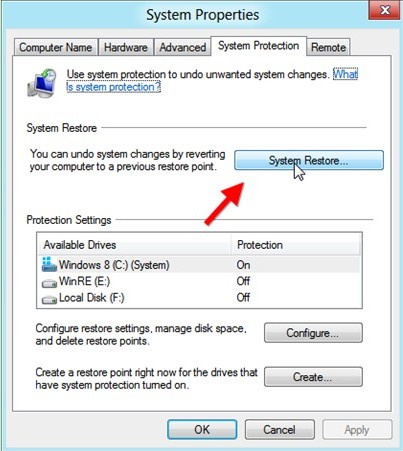
6. Next it will show you System Restore Wizard.
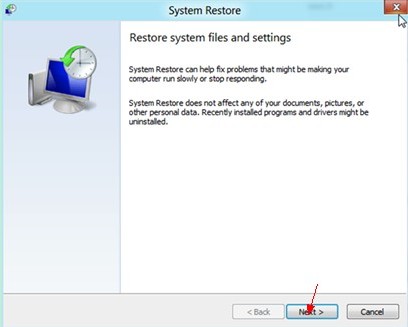
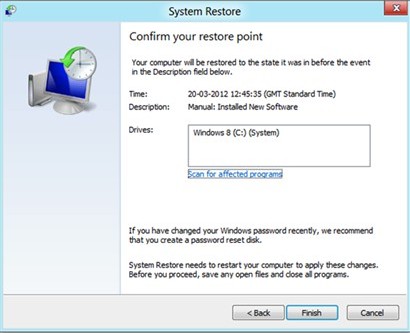
7. In the next window asks that restore point is better to take, click on it and click Next button again.
8. Later after that you’ll find the following window asking you to confirm your choice. Click on Finish button and Windows will automatically complete the restore for you.
CryptoDefense ransomware is newly designed CryptoLocker ransomware that encrypt your files and showing a warning upon desktop for extortion. This deceitful ransomware can attacks all sorts of Windows PC including Windows 7, Windows 8, Windows XP and more. If Internet user’s computer is attacked by CryptoDefense software and files are encrypted it means that your are in high-risk of data loss. CryptoDefense ransomware requires a fee to get all encrypted files restore, which is a commonplace online fraud trick for scammers to make money. CryptoDefense ransomware takes full uses of this tricky fraud to fool targeted Internet users or Android phone users and cheat sufficient amount of money such as the minimum extortion fee of a $500 USD. As by now you know that the solitary goal for CryptoDefense ransomware is to fraud money. You hardly get all your encrypted files restored though the scammers have received the fine. CryptoDefense ransomware makers hardly have a conscience, so that don’t get been trapped. The best way is to remove the ransomware completely from the infectious PC or Android system in case of more decryptions happening. Still need professional help? You can live chat with VilmaTech 24/7 Online Experts