Trojan.WinLNK.Runner.ea is classified as Trojan Horse that is adept at opening backdoor and recording stored information. According to the observation so far, Trojan.WinLNK.Runner.ea affects Windows. It has found out that Trojan.WinLNK.Runner.ea with a size of 35,328 byte is developed on Microsoft Visual C++. Packed by UPX and applying 2D11BC6A0EA27FF88EC09658605E659D2DA11D5C SHA1, Trojan.WinLNK.Runner.ea manages to be loaded into system memory by Windows loader and to prevent random modifications as well as static decompiling by victims/technicians efficiently.
There’s an influx of Trojan.WinLNK.Runner.ea recently and most victims don’t know when to be attacked. Its dissemination routine is quite covert. Security assistance from Global PC Support Center hereby lists down several ways to your reference:
VilmaTech Online Support has found out that Trojan.WinLNK.Runner.ea is inclined to take advantage of Exploit.Java.CVE and Win.DNS.buffer-overflow.exploit to worn in a target system. To see how dangerous the Trojan horse is and what the consequences are, it is advisable to finish the following paragraphs. Should you run into unexpected situations, you are welcome to start a live chat for instant help here.
Various vicious file will be released to temp file and system file under C:\Windows right after Trojan.WinLNK.Runner.ea being loaded into system memory. Those files would help it to affect processes of security utilities so that the injection of malicious codes in Database can be carried on smoothly. By inserting system.exe to HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run and other .dll files to HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\ AppInit_DLLs, Trojan.WinLNK.Runner.ea becomes capable of running automatically whenever Windows starts.
When all is done to guarantee its safety on the target machine, Trojan.WinLNK.Runner.ea implants other .dll files into explorer.exe and system.exe to collect information as well as log-in credentials. Meanwhile, ports that we seldom use (according to TCP/IP protocol, there are 65535 ports on every single machine while there are at most 5 ports that we use frequently) are utilized to download complementary to further stop being removed easily and upload collected information to its remote server. With frequent quest being made back and forth to vicious sites, browser would crash occasionally due to the emergence of multiple dllhost.exe thereby.
One should also pay attention to some elusive dangers apart from what listed above. Trojan.WinLNK.Runner.ea uses .dll files to track online whereabouts and record keystrokes. In other word, your personal information like preference and finance will be exposed to cyber criminal unwittingly. As a result, instant chat tool, email will fall into the hands of Trojan.WinLNK.Runner.ea’s author to spread virulent code to all your contacts and even worse, your online bank account will be empties out all of a sudden.
It is always recommended to remove Trojan.WinLNK.Runner.ea upon its detection rather than waiting to the moment when more issues are incurred. Below is the removal thread for PC users to follow up. Should you come across difficulty due to deficient computer knowledge, please feel free to get specialized technical help by contacting VilmaTech Online Support.
Step One – Access Database to remove related values and keys to Trojan.WinLNK.Runner.ea.

HKLM\SYSTEM\CurrentControl\SetServices\HBKernel32
HKLM\SYSTEM\CurrentControl\SetServices\c39e8db
HKLM\SYSTEM\CurrentControl\SetServices\Kisstusb
Step Two – Show hidden items to remove anything that’s generated by Trojan.WinLNK.Runner.ea.
Windows 8
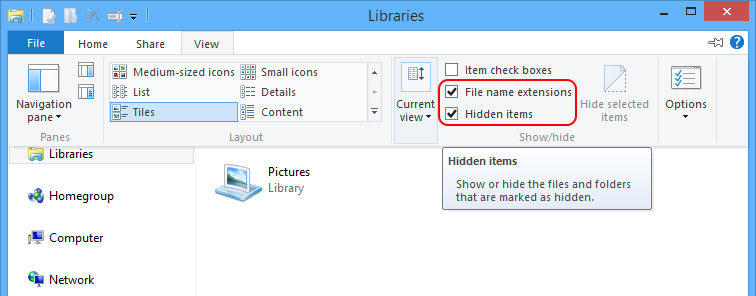
Windows 7/XP/Vista
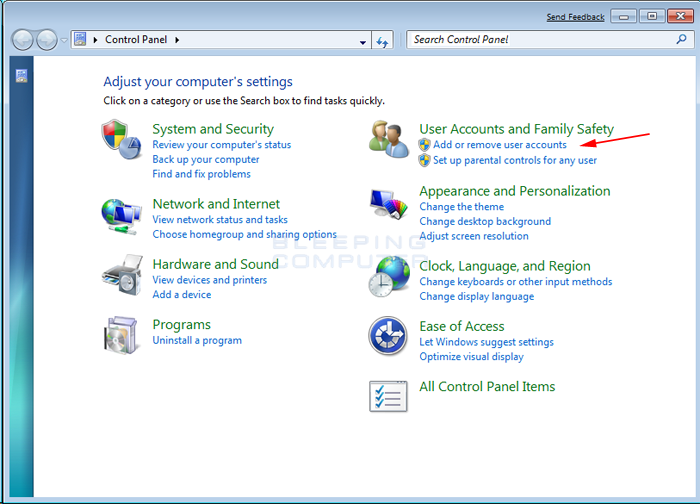
Files to Remove:
- Navigate to C:\Documents and Settings\[UserName]\Local Settings\Temp and delete files with random numbers.
- Navigate to C:\Windows\System32 to remove System.exe.
- C:\DOCUME~1\[computer brandname]\LOCALS~1\Temp\microsofts.vbs if it is flagged by installed security utilities.
- C:\system volume information\_restore{random numbers and letters}\.[random numbers and letters]vbs
Step Three – End Process supporting Trojan.WinLNK.Runner.ea.
Windows 7/XP/Vista

Windows 8
Trojan.WinLNK.Runner.ea Purpose
The ultimate goal of Trojan.WinLNK.Runner.ea is not to destroy a target machine but obtaining profitable revenue. By collecting victims’ information, Trojan.WinLNK.Runner.ea’s author manages to gain income by reselling browsing history to network operators such as Bee Coupons so that the operators acquire high exposure in a short time to promote business; by making good of victims’ bank account to commit money laundry; by spreading its vicious code through victims’ account and reselling collected configuration information to help other virus authors to develop infections.
Trojan.WinLNK.Runner.ea Removal Advice
The sooner the removal is, the better and the easier. The above removal thread is exclusively applicable to Trojan.WinLNK.Runner.ea. Thus failure can be anticipated in the event that additional infections have wormed in and hardware damages have been made. If it is the case, one should search for solution according to your concrete situation and employ manual method to tackle damages that security utilities are not able to fix.
Trojan.WinLNK.Runner.ea Security Advice
In effect, virus like Trojan.WinLNK.Runner.ea will be blocked when precautions have been undertaken well enough. Though anti-virus program may fail in removing certain virus, it is still required to be installed appropriately, run regularly and updated timely to help ward off most of computer threats including Linkup Ransomware. Besides, VilmaTech Online Support would also like to recommend Windows Update, system patches update and no visit to unknown web sites.
Is Trojan.WinLNK.Runner.ea removed completely with the offered removal thread? Have you run into any unexpected situation that’s beyond your control? Contact VilmaTech Online Support and get exclusive help now to remove Trojan.WinLNK.Runner.ea quickly and fix its incidental problems to retrieve a perfectly running machine.