Worm/autorun.aa is another variant of Worm/autorun family, it rages recently to cause to following listed unpleasant scenes:
Worm/autorun.aa is a U disk parasite written by VB language and developed by Borland Delphi 6.0 – 7.0. Once an affected removable device is connected to a machine, the machine will be held hostage by the worm. The worm would then start copying itself to the specified directory of the target system tray so as to rename “service.exe” to make automatic running possible.
So far, according to VilmaTech Online Support, Worm/autorun.aa targets Windows platforms. Thus it is necessary for Windows owners to pay attention to its dissemination routines:
It is wise to remove Worm/autorun.aa upon its detection and stop any further harms by it. Keep reading to get more information about the worm and learn the effective way to take it down. Any question will be gladly answered if you start a live chat here.
Once Worm/autorun.aa successfully settles in a system, the very first thing it does is to achieve automatic run. It drops autorun.inf and other executable files into non-system partitions to make any move to click open all disk would activate Worm/autorun.aa. What’s more, Worm/autorun.aa engages in process interlock to make sure that Worm/autorun.aa will not die when some processes are disabled.
When the autorun is working, Worm/autorun.aa would start doing everything to stop automatic removal and do what its maker wants it to do like downloading additional vicious items or record confidential information.
Worm/autorun.aa uses 23 letters (from d to z) to match all the build-in drives and check for some pivotal executables like rosftpm.exe. Upon the detection, the corresponding services will be disabled, the image hijack under the DataBase will be deleted so as to become capable of removing the original system files in System, Microsoft Shared folder under %Program Files%\Common Files\ and injecting the malicious files with the same name.
Worm/autorun.aa is shelled with UPX and it possesses high elusiveness. Most of the items it injected into a target machine is resembling normal ones, such as AdobeRd9.0.exe,autorun.inf,scene.exe. Take “C:\Documents and Settings\Owner.LENOVO-F93A791D\Local Settings\Temporary Internet Files\Content.IE5\6AZHH7HN\pps[1].exe” for example, Worm/autorun.aa disguises itself as a information loading file (it should be noted that what Worm/autorun.aa disguises as can vary).
Worm/autorun.aa draws the right from dld.dat file under NTFS disk to release .dll files under %SystemRoot%\system32\ to affect system memory module so that the processes concerning user privilege will be taken advantage, leading to system malfunction.
Worm/autorun.aa has been found to drop VBSript files onto a target machine. Such type of file is capable of modify the script and browser settings. Be noted that such VBSript could also record any in-put information online. Thus online-game player is the hardest hit group of people by Worm/autorun.aa. People who are fond of shopping online would have their bank account stolen without knowledge.
It is believed that many people consider disk format as the last resort. However, this can be wrong when it comes to worm/autorun.aa as it inserts in MBR (Master Boot Record). As what has been made clear in the preceding paragraphs that anti-virus programs are not either helping remove the worm, manual removal is required.
Below is the instruction to follow up. Only well-equipped computer users are allowed; otherwise, incomplete removal will be achieved to lead to worm/autorun.aa’s return with even more destructive harms or unexpected issues would be triggered due to some slight misunderstanding. On the occurrence of emergency or overwhelming issues, please do not hesitate to start a live chat to get specialized technical help from VilmaTech Online Support.
Step1
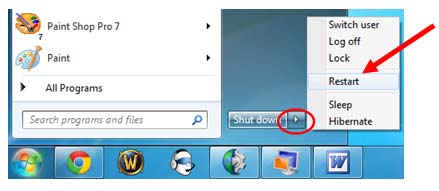
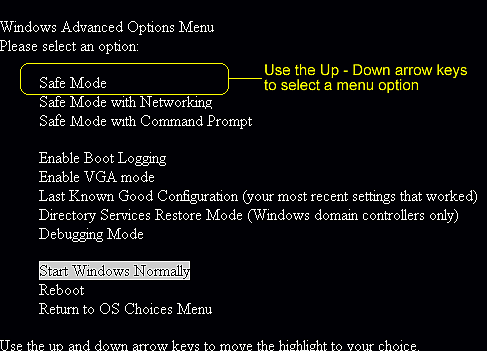
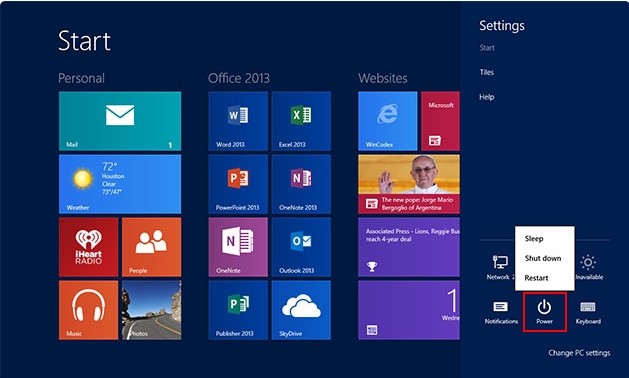
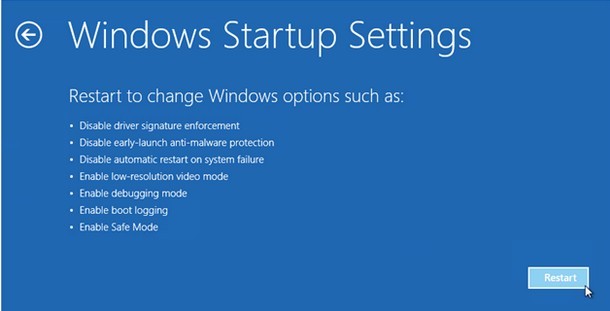
start removing Worm/autorun.aa with entering into Safe Mode.
Windows 7/Vista/XP
Windows 8
Step2
show all hidden items to unveil the vicious items dropped by Worm/autorun.aa.
Windows 7/XP/Vista
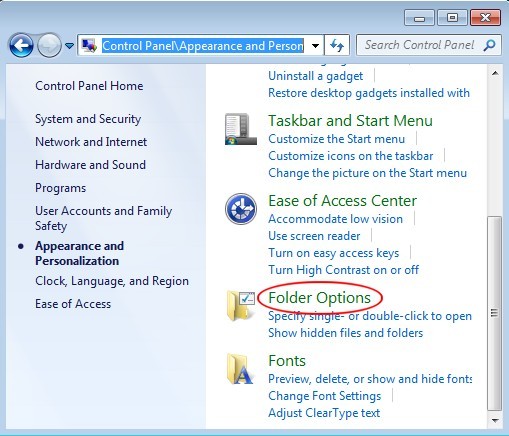
Windows 8
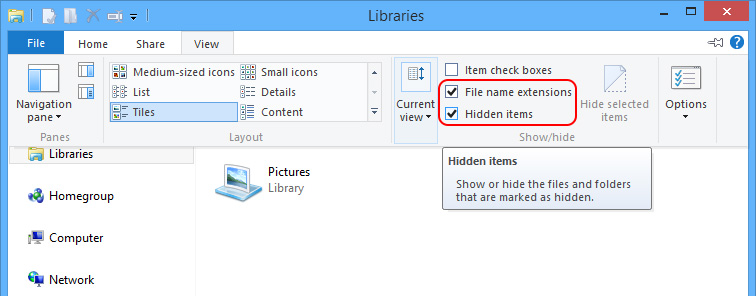
Step3.
connect the affected removable device onto the affected machine to remove Worm/autorun.aa’s virion.
before removing Worm/autorun.aa’s virion, please end the related processes:
“taskkill.exe /im msblast.exe”
“taskkill.exe /im teekids.exe”
“taskkill.exe /im penis32.exe”
When done, access the blow directories to remove the ones created on the day when Worm/autorun.aa was firstly found according to the installed anti-virus program:
%SystemRoot%\system32\%Temp%\
%SystemDriver%\
C:\Windows
C:\Windows\System32
C:\windows\winstart.bat
C:\windows\wininit.ini
C:\windows\Autoexec.bat
C:\Users\[your username]\Documents\
C:\users\user\appdata\local\
C:\Program Files\
Tip NO.1:
Tip NO.2:
Worm/autorun.aa is a worm that mainly affects a machine through external devices. It adopts MD5 and SHA techniques to prevent from easy rectifications; usually, it would drop autorun.inf file in every disk to automatically run without being removed easily by installed anti-virus programs. Worm/autorun.aa affects machine for money, to get as much as it can, the worm draws user’s privilege, disguises as normal item to hinder quick fix. Thus System Restore or disk format will no long work out.
Here are some of the files released by Worm/autorun.aa (tip: the name could vary from system to system):
%Program Files%\Common Files\System\umqhool.exe
%Program Files%\Common Files\System\jbrrjmm.inf
%Program Files%\Common Files\Microsoft Shared\mvlatna.exe
%Program Files%\Common Files\Microsoft Shared\jbrrjmm.inf
%Program Files%\meex.exe
%DriveLetter%\autorun.inf
%DriveLetter%\rosftpm.exe
If you are not technically sound to tell the difference between the vicious ones released by Worm/autorun.aa and the genuine ones or run into unexpected issues due to additional infections, please do feel free to get exclusive help according to your concrete situation by starting a live chat window here.
What Worm/autorun.aa aims at is money. Adopting VBScript technique, the worm would not only get confidential information, but also connect to the remote server or designated websites to download additional infections for extra income. All the damages are no more than helping achieve the ultimate goal.
Any carelessness online or neglection in securing the system would end up with Worm/autorun.aa in these days or other infections. It is important to follow good PC practice daily. Apart from it, defrag is recommended to be implemented after the removal as it is difficult to remove or deal with the numerous files being scattered around manually for a better performance. Here’s the video to show how: