Win 8 Protection 2014 seems to be an authentic program that is specifically designed to safeguard computer against potential threats with alleged real-time protection. However, one must realize the fact that Win 8 Protection 2014 has no association with standard antivirus and has been widely recognized as one form of latest rogue security software (alias. fake antivirus program). It is a hazardous computer infected released by malware distributors who strive to benefit from victims. Similar as its family member like Win 7 Protection 2014, XP Protection 2014 and Vista Protection 2014, Win 8 Protection 2014 generally makes use of bogus pop-up security warning notifications to mislead users into believing that their machines have been assaulted by numerous intractable security issues. An effective solution must be adopted to take care of the computer under attack. Naturally, Win 8 Protection 2014 will encourage victims to activate their copies right away so as to enjoy the ultimate protection with the its fake licensed version.
Win 8 Protection 2014, much as the name shows, is a particular computer infection targeting individuals using Win 8 compatible PCs, regardless of 32-64 bytes. The infection can always sneak into a user’s computer through various dishonest ways. Usually, Win 8 Protection 2014 may be propagated through affected websites such as peer-to-peer file sharing websites, spam email attachments & links or unknown free applications shared on networks. When installed and initialized, Win 8 Protection 2014 creates its malignant registry files and code to significantly make modification in system configuration, including the Master Boot Record (MBR) – one kernel part of system controlling the operating system’s bootloader as well as the storage device’s partition table. As a result, Win 8 Protection 2014 can be loaded up on every windows boot and implement its damaging activities automatically.
Note: If you meet any trouble while removing Win 8 Protection 2014 fake antivirus from your computer, please be free to contact VilmaTech Certified 24/7 online expert here who will be glad to help you out of trouble.
Apart from the basic symptom of fake Windows warnings, Win 8 Protection 2014 may lead to additional problems on the computer that it infects. Commonly, taking root in the compromised machine, Win 8 Protection 2014 may decrease the whole performance of system through occupying high memory space, and potentially, result in high CPU utilization without too many running processes in task manager. Besides, Win 8 Protection 2014 may perform a full scan of affected computer in an effort to figure out all possible security vulnerabilities. In this case, the targeted machine may encounter a number of other forms of malware such as Trojan, browser hijack virus, worm and more. For the further results, Win 8 Protection 2014 may steal victim’s confidential data directly including Facebook/Twitter account and passwords, personal identify information and online banking data. Certainly, Win 8 Protection 2014 should be eliminated from Windows as long as being informed of its existence.
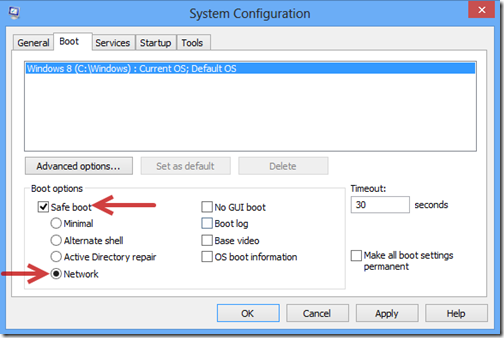
1. Log in Safe Mode with Networking.
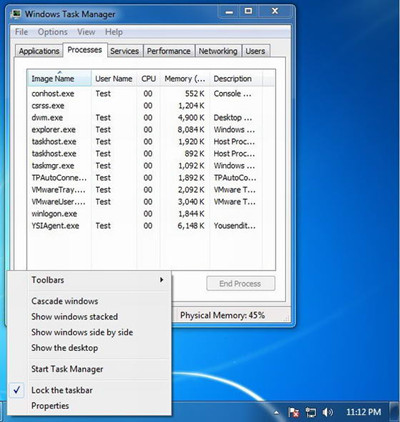
2. Get rid of all the files and registry entries of Win 8 Protection 2014 fake antivirus.
%system%\[random characters].dll
%Documents and Settings%\[User name]\Desktop\[random name].exe
C:\Users\Stuart\AppData\Local\Temp\[random names].exe
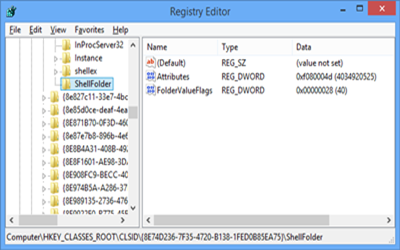
HKEY_CLASSES_ROOT\CLSID\[random numbers]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\”Shell” = “[SET OF RANDOM CHARACTERS].exe”
Win 8 Protection 2014 is one form of malignant program that pretends to be a standard antivirus, capable of protect user’s computer from existing or potential PC risks. The infection specializes in the attack on computers using Windows 8 operating system. Often, Win 8 Protection 2014 can always sneak into a user’s computer without asking for any approval. Once being installed, abnormal symptoms will be triggered without any doubts. As a typical hack tool operated by cyber criminals, Win 8 Protection 2014 generally uses fake automated scanners to allegedly have a check on targeted machine, and then misleads users to purchase its full licensed version for the sake of simulated removal of malware. Besides, the computer virus may also result in additional harm on affected machine such as sluggish performance of system, extra malware, data loss and even computer crash. It is obvious that computer users should remove Win 8 Protection 2014 virus once harmful symptoms appear.
Attention: Manual removal of Win 8 Protection 2014 is a high-risk task, as it is related to kernel system configuration and registry. If you cannot deal with the operation alone, you are welcome to ask help from VilmaTech Certified 24/7 online expert here .