The Paltip.com we talk about herein is specifically referring to api.paltip.com rather than the recommendation and sharing tool. It can be clear in telling that it is not virus as anti-virus programs are not detecting it when it is redirecting PC users. PC users should be informed that all security utilities detect virus based on virulent attribute code which is one of the basic element that a virus possesses.
Without the code, it is not virus. So what is paltip.com and should PC users be worried? To get more information, please keep reading. If one has emergency that needs expert help, please do feel free to contact VilmaTech Online Support by starting a live chat window.
Just like Gil.mapjava.net (read more), paltip.com is categorized as PUP that is created to intercept traffic by force so as to, on one hand, making itself to rank high in search engines and on the other hand, direct traffic to other sites owned by operators that paltip.com has cooperative ties with for profitable commission.
Not being a virus, how paltip.com manages to perform non-computer-friendly behaviors such as stick to a computer? BHO and JavaScript techniques were originally created to help save CPU by preloading web applications into system configuration to ensure automatic start and to help with quick access to the frequently visited sites by remembering browsing histories. Some ambitious online operators with rich computer knowledge then figured out some other uses out of the two techniques:
Api.paltip.com is not technically a virus though, concerns should be thrown to the PUP (potentially unwanted program). As surveys show, an online operator owns several PUP/ promotional tools. When one of the tools suffers from resistance, other tools will be put to the market in succession to keep intercepting traffic. Besides, it is easy to make a PUP. Therefore, the applications like paltip.com are not strictly programmed. Bug can be readily found and exploited by virus injected onto the Internet.
What’s worse, a backdoor program has been found by VilmaTech Research Lab to be attached to api.paltip.com for the access of the information on which sites are frequently visited. With such information, the operator behind paltip.com would be able to know where to put api.paltip.com and perform traffic interception on another computer by force. Such backdoor program can be taken advantage once bugs on api.paltip.com have been captured to allow unsolicited access from unknown third-party.
Whereupon. BHO technique would allow more infections, JS technique would help to record log-in credentials and backdoor program would alleviate infiltration and direct control. It is always recommended to remove api.paltip.com as soon as possible before additional infections worming in to complex the whole situation. Below is the manual removal method to follow up since anti-virus programs don’t remove it. Any help request will be gladly answered if one starts a live chat window here.
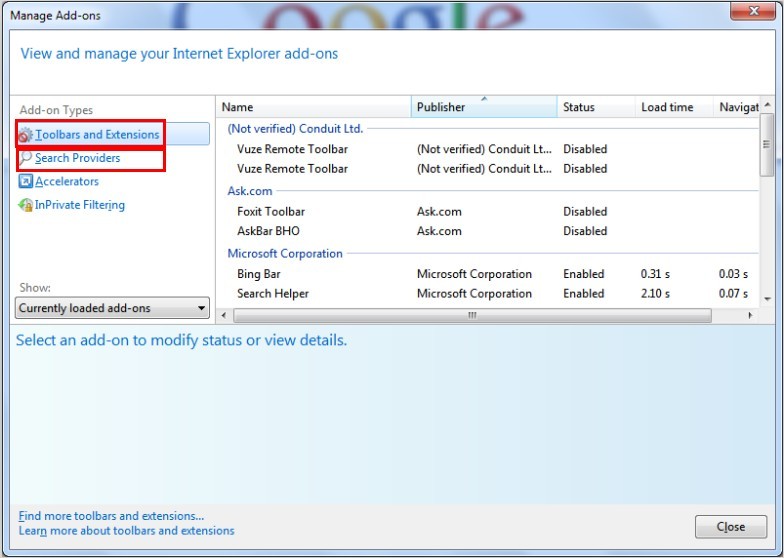
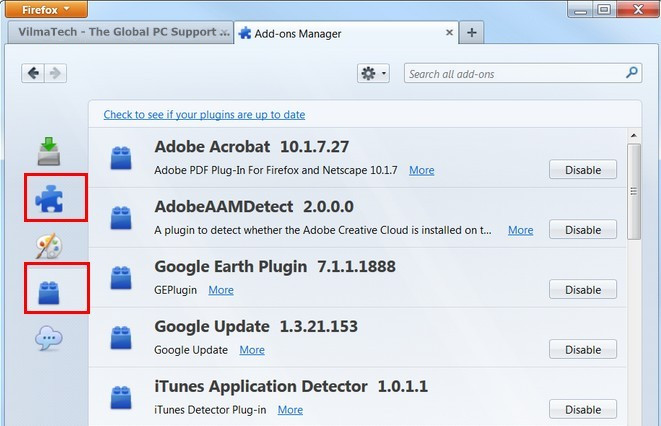
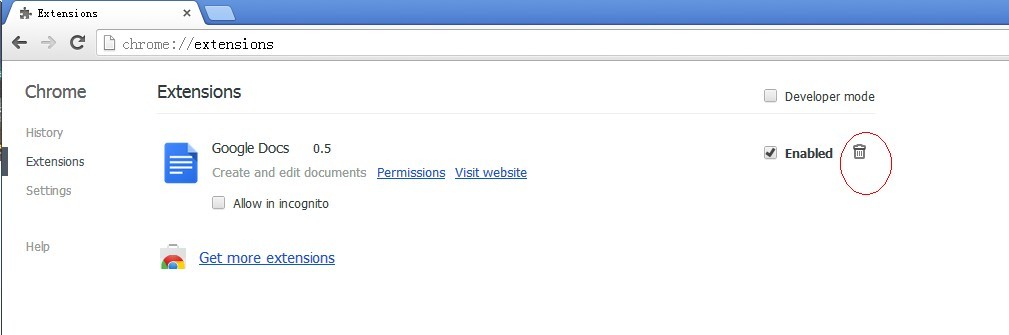
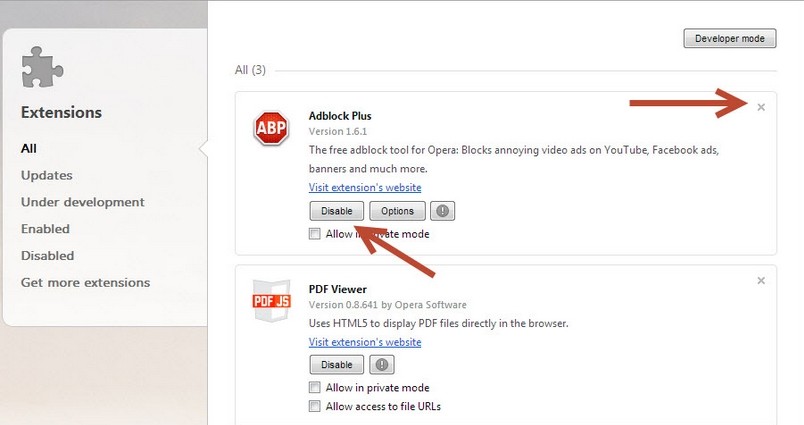
A – Remove the extensions installed on the day when paltip.com/ api.paltip.com firstly appeared.
Internet Explorer
Firefox
Chrome
Opera
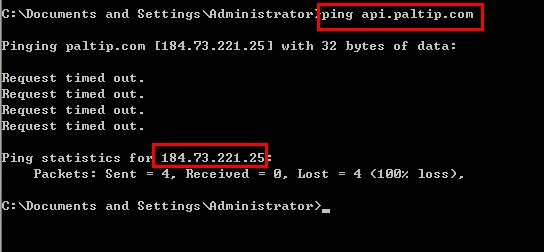
B – Ping api.paltip.com to get its IP address and modify Hosts file to block it.
(tip: the IP address for paltip.com could vary due to different system configuration)
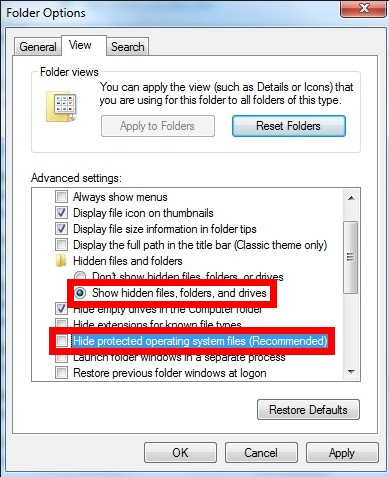
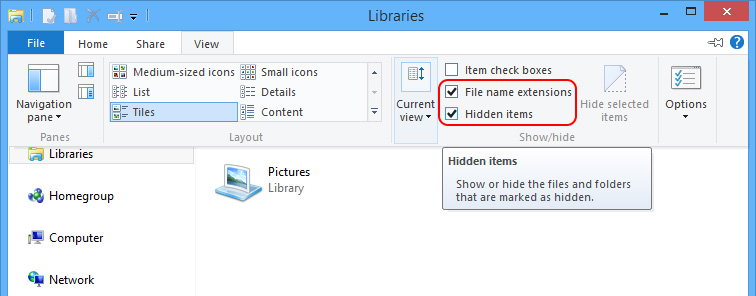
C – Unveil all hidden items to search for and remove the items related to paltip.com/ api.paltip.com.
1. show hidden files and folders.
Windows 7/XP/Vista
Windows 8
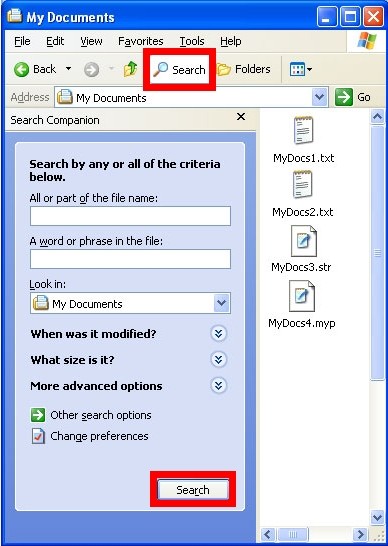
2. search for the documents associated with api.paltip.com.
Api.paltip.com is now commonly called by victims as paltip.com. It is not a virus even though it causes some unpleasant scenes. For this reason, all security utilities will not remove or even detect paltip.com when it is causing troubles. Therefore manual removal method is recommended to deal with the PUP. The necessity of removing paltip.com has been made clear in the preceding paragraphs. Hopefully that this article has been carefully read to know the dangers paltip.com can post.
Though paltip.com is not a virus at all, it is recommended to remove all of its evidence on the computer such as its data files. By doing so, one is able to exterminate the fear of conflict among programs and files in the future when trying to install another program; also the computer resource will be then reasonably utilized and allocated. In the event that additional infections have wormed into the target machine, it is advisable to perform a thorough removal to safeguard your precious machine. If you don’t know how to remove a specific infection that takes advantage of paltip.com, please visit virus reservoir to get the solution accordingly; as alternative, get professional help by live chatting with security assistance from VilmaTech Online Support.
Creating a restore point when all safety loopholes are exterminated is an effective precaution to be again attacked by infections in the age of virus expansion. But be noted that system restore is not necessarily removing all infections, it can’t eradicate most of the Trojan horse when the resort points are affected. However, system restore could relieve the mechanical issues in order to carry quick fix. Here’s the video to show how to create a restore point.