CryptoTorLocker2015, much as the name implies, is one type of newly released ransom virus that is adept at screen locker technique. The main attacking algorithm CryptoTorLocker2015 utilizes is the industry-leading XOR encryption which is capable of forcibly encrypting the personal files on a user’s computer, including the sensitive photos, videos, documents, etc. CryptoTorLocker2015 ransomware generally appears to victims in a form of a bogus notification on the monitor, trying to mislead users into believing that the machine is under locker and encryption due to impertinent activities. In order for the encryption to be decrypted, CryptoTorLocker2015 threatens users to pay 100 USD/100 EUR/0.5 Bitcoins to its appointed anonymous address where would offer the unique public key RSA-2048 for the targeted machine.

However, similar as another Caribarena ransom virus, CryptoTorLocker2015 scam is nothing but a type of malware utilized by Internet fraudsters who strive to perform data kidnapping and money extortion. In reality, CryptoTorLocker2015 can often sneak into a user’s computer through a variety of dishonest way. When installed & executed, it makes full use of the XOR algorithm and mastered technology result in disruptions on default system configurations. CryptoTorLocker2015 scam would modify MBR settings compulsively so that to be run automatically on every Windows boot. To generate further traffic on the computer that it affects, CryptoTorLocker2015 virus also adds items related to “CryptoTorLocker2015” to the end of each filename in system. In the directories, victims may also notice one particular file called “HOW TO DECRYPT FILES.txt” by the ramsomware. Suppose the CryptoTorLocker2015 cannot be eradicated from a machine, it may lead to worse results on user’s computer as well as privacy.
Note: CryptoTorLocker2015 is a hazardous ransomware endowed with leading hack technology that cannot be handled with common removal method. Your antivirus may be blocked or disabled as long as the machine boots up. In this case, you may consider the helpful manual removal to get rid of CryptoTorLocker2015 step by step. If you are not familiar with the operation, you are welcome to ask help from VilmaTech Certified 24/7 online expert here, who will be glad to help you out of trouble.
Major computer users may wonder the approaches that CryptoTorLocker2015 scam infiltrates into their machines. More currently, CryptoTorLocker2015 primarily attacks Windows compatible PCs; especially those contain obvious system vulnerabilities. CryptoTorLocker2015 infection may often make use of an exploit kit such as Blackhole, which is able to explore the vulnerabilities in system for the sake of installing and executing the virus on the machine without asking for any approval. CryptoTorLocker2015 may also arrive as part of another malware’s payload such as the rootkit based Trojan, worm, fake antivirus application and more. On the other hand, this harmful ransom virus may be distributed by compromised website like P2P (peer-to-peer) file sharing web pages. PC users should be cautious while clicking on spam email to avoid the infection by the tricky CryptoTorLocker2015 ransomware.
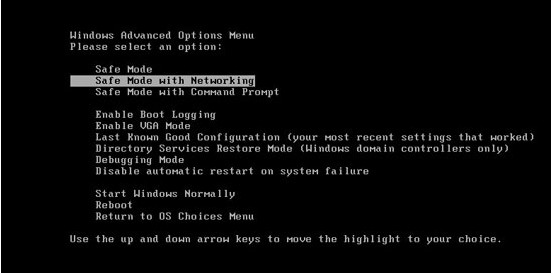
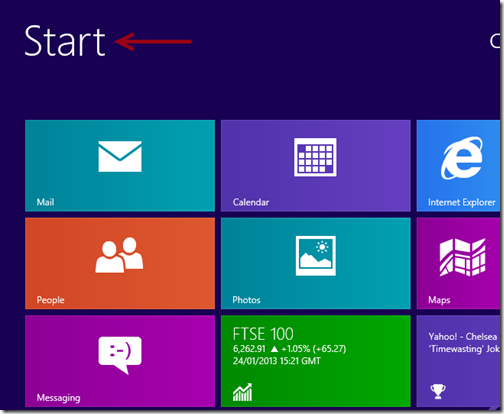
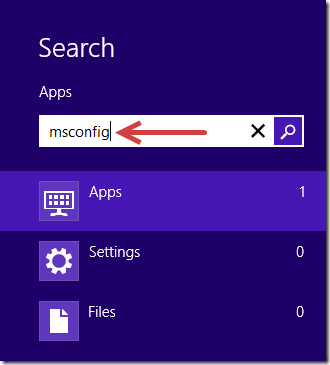
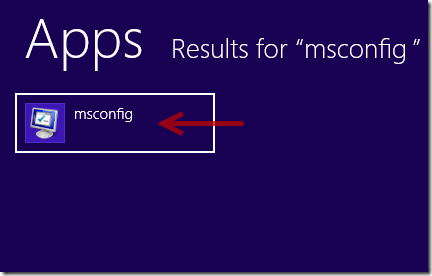
1. Log in Safe Mode with Networking.
The regular mode of your computer may be blocked and encrypted by CryptoTorLocker2015 ransomware completely, so you are required to enter your system in Safe Mode with Networking where you can perform manual operation smoothly. Here is the step by steop guide:
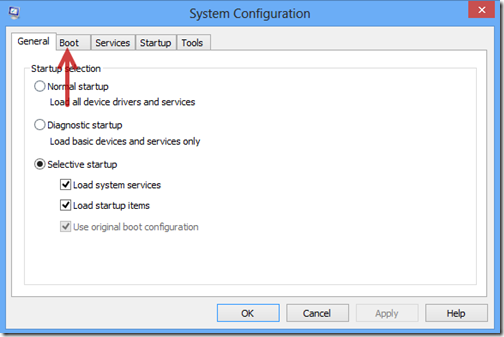
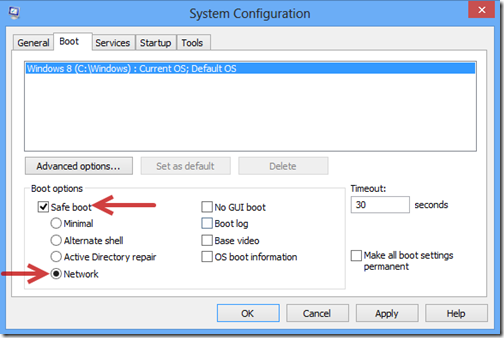
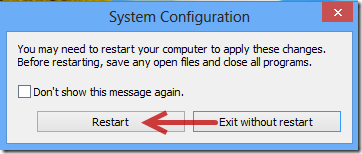
2. Remove files and registry files related to CryptoTorLocker2015 infection.
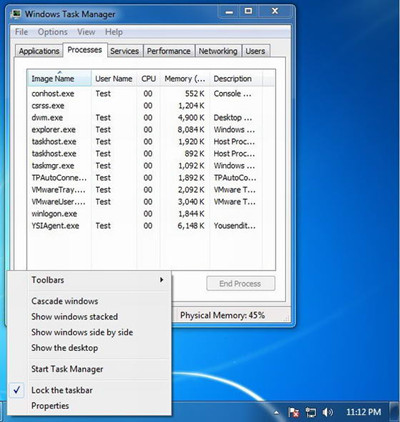
%Temp%\random
%appdata%\random
%StartupFolder%\random.lnk
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\run\random
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableRegedit” = “”.exe.dll
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Settings\{random.exe}
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun=””
CryptoTorLocker2015 is a dangerous ransom virus that is designed by cyber criminals to disrupt a user’s computer for illegal purposes. Till now, the version of CryptoTorLocker2015 virus mainly attacks individuals using Windows operating system, such as Windows XP, Windows 7, Windows 8 and Windows Vista. When installed, CryptoTorLocker2015 infection usually modifies system settings in order to run on the affected machine and encrypt the user’s personal files forcibly. It tries to threaten users into paying concoctive fee to release their computers. Internet users should notice that CryptoTorLocker2015 virus is only a threat operated by fraudsters who want to gain from victims. Even through the payment is delivered; your computer won’t get rid of the infection instead. Without any doubts, victims should try their best to clean up all the files and entries of the CryptoTorLocker2015 ransomware once being noticed its existence.
Note: Manual removal requires certain expertise during the operation. No single mist ale allowed. If you cannot deal with the process alone, please be free to contact VilmaTech Certified 24/7 online expert here for real-time support.