MalSign.Generic.A8A is categorized as perilous malware, which created with abilities to compromise web browsers on targeted computer and take malicious actions to trick money or steal confidential data. MalSign.Generic.A8A malware is currently public enemy over alleged corrupting victimized operating system and confidential information-stealing. The malware had attacked thousands of users’ computers around the world and implicitly stolen sensitive information such as log-in credentials, banking data, privacy regulation and more from them. The solitary goal for hijackers creating such MalSign.Generic.A8A malware is to acquire benefit. Whilst MalSign.Generic.A8A virus is just similar to the Uptodatecontent.net virus, can make a lot of damages to acquire a complete controlling on the infectious computer. The MalSign.Generic.A8A malware must constantly exploit system vulnerabilities to the infectious machine and make it totally vulnerable for more malware enticing in. As doing so can hijackers can handle with malicious activities on the infectious machine without any distraction.
JS/Blacole.OU is an invasive JavaScript Trojan infection that can be connected to remote hackers using a distant Comman-and -Control (C&C) server. It is usually added into genuine websites that have been compromised by malware distributors. For the purpose of corrupting a compromised website, JS/Blacole.OU infection will inject its malevolent codes into it. Suppose that an Internet users may be unwillingly rerouted to the hijacked web page, this type of Trojan infection will sneak into victim’s computer without any authorization or knowledge. Meanwhile, the malicious payload of JS/Blacole.OU is being popularly delivered by a security exploit kit such as BlackHole, which is known as one of the most prevalent web threat, capable of excavating all possible system security vulnerabilities. Apart from those spread approaches, JS/Blacole.OU virus is also believed to emanate from downloads or updates of certain applications, some examples of which are pirated or illegally acquired software applications.
Any infiltration would incur some weird scenarios on a target machine since only vicious modification can guarantee that a virus would not be removed by build-in security utilities and services and that a continuous theft. However, some of the scenarios can be covert without arousing victims’ attention. Below is the list of the symptoms of Exploit:JS/Neclu.M affection, which would help you detect Exploit:JS/Neclu.M and take actions against the Trojan horse before more troubles are incurred thereby under the circumstance that it disables anti-virus programs:
Uptodatecontent.net seems to be a legitimate website primarily providing free online videos which reveal proven ways to win any confrontation in few seconds against large more skilled opponents. However, Uptodatecontent.net has been considered as a malevolent malware that may be linked to browser hijack virus or adware infection. According to the feedback of Internet users, this form of malware can always permeate into a targeted machine secretly with the aid of its progressive hack techniques. Upon its installation, Uptodatecontent.net hijack virus may immediately implant its accessory codes into system so as to make modification in web browser configuration. When succeed, the infection may take control of a computer’s Internet connection, hijack user’s web browsers, regardless of IE/Chrome/Firefox, to various suspicious domains operated by cyber criminals who attempt to benefit from victim. Meanwhile, Uptodatecontent.net may hijack user’s documents as well, by technically creating hyperlink words with a “double line” which is pointed to ads or links related to other websites.
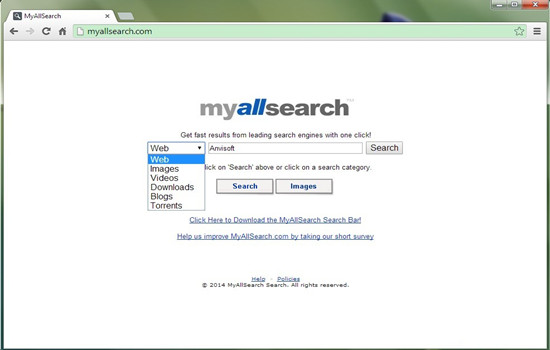
123srv.com is regarded as hazardous browser hijacker, which work focuses on secretly using the vulnerability in opening backdoor on the compromised computer and then allowing hijackers accessing in, while leaving hundreds of Internet users at high-risk of confidential information pilferage. 123srv.com browser hijacker is increasingly epidemic around the cyber world due to it has been on vulnerable all sorts of Internet browser such Internet Explorer, Google Chrome, Mozilla Firefox, Opera and more. And most social sites also become the vulnerable. The 123srv.com browser hijacker can steal much more sensitive information once the backdoor opened and hijackers accessed in. The 123srv.com intrusive browser hijacker equally tampers with targeted Internet settings and alters defaults such as default homepage, search engine, startups and new tabs with certain URL or any other malicious thing that uses it. Hijackers keep releasing such 123srv.com browser hijackers just aims at benefit-making, you may refer to the similar MyAllSearch.com browser hijacker removal here.
A newly discovered hazardous virus publicly known as POSHCODER ransomware has been increasingly epidemic in cyber world due to its notorious property of encrypting all files ended with .txt, .doc, .xls on the compromised computer. All encrypted files are in forms of .psd illustrator files. POSHCODER ransomware is regarded as one of the most commonly used online fraud exploited by hijackers and cybercriminals to trick victimized users’ money, which has abilities to present an immediate and serious danger to any vulnerable computer. The POSHCODER ransomware, allows hijackers to lock users out from accessing to their personal files on the victimized machine and steal sensitive information such as log-in credentials, personal data, and decryption keys. The POSHCODER ransomware extorts money from the targeted Internet computer users by encrypting their personal files, which can perform an incredible damage from the compromised computer. If all your files are encrypted with the form of .psd, your computer is attacked with the POSHCODER ransomware.
Win32:VBCrypt-CSL[Trj] currently becomes a headache for individuals by forcibly triggering damaging activities on the computer that it infects. By default, Win32:VBCrypt-CSL[Trj is an invasive multiple component rookit infection that has been universally detected by Avast antivirus as well as other security utilities. However, by means of its progressive rookit capabilities, Win32:VBCrypt-CSL[Trj] can easily evade the full detection and removal operated by antivirus software or other virus remover. Similar as other Trojan virus such as HEUR:Exploit.SWF.Agent.id (Removal Tips), Win32:VBCrypt-CSL[Trj] can regularly circulate via a variety of dishonest ways such as compromised websites, malevolent application downloads, or other spam email carrying malicious attachments. Apart from those common spreading routes, the harmful payload of Win32:VBCrypt-CSL[Trj] is being popularly delivered by making use of a exploit kit such as BlackHole, which has the capability to dig and utilize found security vulnerabilities so as to drop and install the components of the virus surreptitiously on compromised machine.
MyAllSearch.com has been reported to be a malevolent hijacker which could brazenly lead the innocent users to any unsafe websites and cause them irreparable losses. In most cases, many computer users had no idea about how the MyAllSearch.com got installed in the computer system and apparently most of them could not detect the infection by themselves in the first place. Once the MyAllSearch.com redirect virus had its way to infect the targeted computer, it would replace the original homepage into myallsearch.com without authorization, in the mean time, this cunning hijackers also made some modifications in the browser and the system maliciously so as to avoid being detected by the users and also the installed antivirus in the computer, striving for more time to achieve its evil purposes. In this case, the default search service would become the MyAllSearch.com. As long as the users have not found the changes happening in the browser, they would used this malicious redirect virus for searching, blindly being redirected to unsafe sites without awareness.
HEUR:Exploit.SWF.Agent.id currently assaults individuals using Windows operating system (OS), especially those are short of appropriate security protection. It is considered as an emblematic Trojan infection designed by cyber criminals, which often acts as Backdoor. As a matter of fact, HEUR:Exploit.SWF.Agent.id, in computing is a non-self-replicating type of malware program which specializes in make destruction on affected machine with the aid of its in-built malevolent codes. To get common knowledge about HEUR:Exploit.SWF.Agent.id, it can regularly infiltrate a targeted computer through a variety of tricks. The malicious payload is being delivered to a computer by means of the infamous BlackHole exploit kit, which has the capability to excavate the security vulnerabilities in OS. Apart from the approach, malware distributors may spread the backdoor Trojan by making use of SEO poisoning techniques, which refer to the infected URLs related to recent hot events or news.
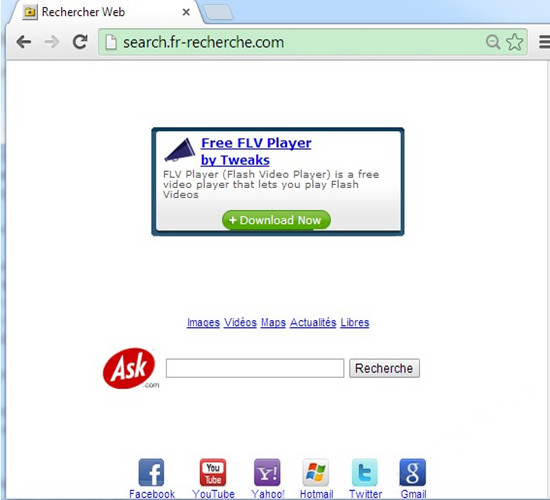
Search.fr-recherche.com was considered as a new found redirect virus however which has widely spread on the Internet already, making plenty of targeted computers as the victims to achieve its evil purpose. Once the Search.fr-recherche.com hijacker successfully got into the computer system unimpededly, the browser would suddenly be taken over. Under this circumstance, there would be some unexpected changes happening. Such as the original homepage, probably user’s favorite, would be forcibly replaced into the search.fr-recherche.com, and a mass of unfamiliar add-ons, browser extensions or additional components would be added in the browser without authorization. In this case, as all the unwanted add-ons running in the background, the Search.fr-recherche.com would not only affect the browser performance by decelerating the loading speed, it could also confuse the innocent users whenever they launch the browser. With the confusing interface looks just like Google Chrome, Search.fr-recherche.com has fooled almost all the users for a long time.