Trojan.Viknok!inf is a computer virus, which is specifically produced by cyber criminals who attempt to trigger damaging activities on the affected operating system and then steal valuable information off PC user. By default, Trojan.Viknok!inf is a program carrying malevolent codes that cannot fulfill the process of self-replication. It mainly carries out destructive actions on the computer that it infects by technically implanting its programmed codes and files in Windows Registry. Very often Trojan.Viknok!inf virus can generally infiltrate a targeted computer without host’s awareness and authorization. When executed, this type of infection may decrease the overall PC performance and significantly slow down the PC via occupying large amounts of system resources. For the purpose of filching victim’s confidential data, Trojan.Viknok!inf virus may always display cookies and keyloggers on the compromised machine. This may include online banking credentials, personal identification information or other important data. At the same time, Trojan.Viknok!inf may often acts as a backdoor which has the capability to permit remote hackers to access affected Windows freely. It is common that a backdoor can be often used to initiate DDOS attacks and even drop and install additional PC malware on targeted machine. There is no doubt that Trojan.Viknok!inf should be terminated from computer as long as being informed of its presence.
An infamous malwarecalled Bk-coretag.js (tags.bkrtx.com) has been released by cyber criminals over the worldwide web, which work concentrates on tricking money and confidential information-stealing. A big proportion of victimized users attacked by such Bk-coretag.js (tags.bkrtx.com) pop-ups lost abilities to govern the Internet browser such as Internet Explorer, Google Chrome, Mozilla Firefox, Opera and more. Bk-coretag.js (tags.bkrtx.com) malware is just similar to the Key-Find.com browser hijacker, which can compromise the infectious computer and tamper with all default Internet settings. Default search engine, startup, new tab and search results must be overlapped with Bk-coretag.js (tags.bkrtx.com) malicious sites or its associated perilous pop-ups. This implies that victimized users of the Bk-coretag.js (tags.bkrtx.com) malicious pop-up can’t search any will things on the infected computer. In stead, Bk-coretag.js (tags.bkrtx.com) pop-ups will perform abundance damage to give rise to a total system failure. As doing so can hijackers completely take over the victimized computer can steal confidential data without any distraction.
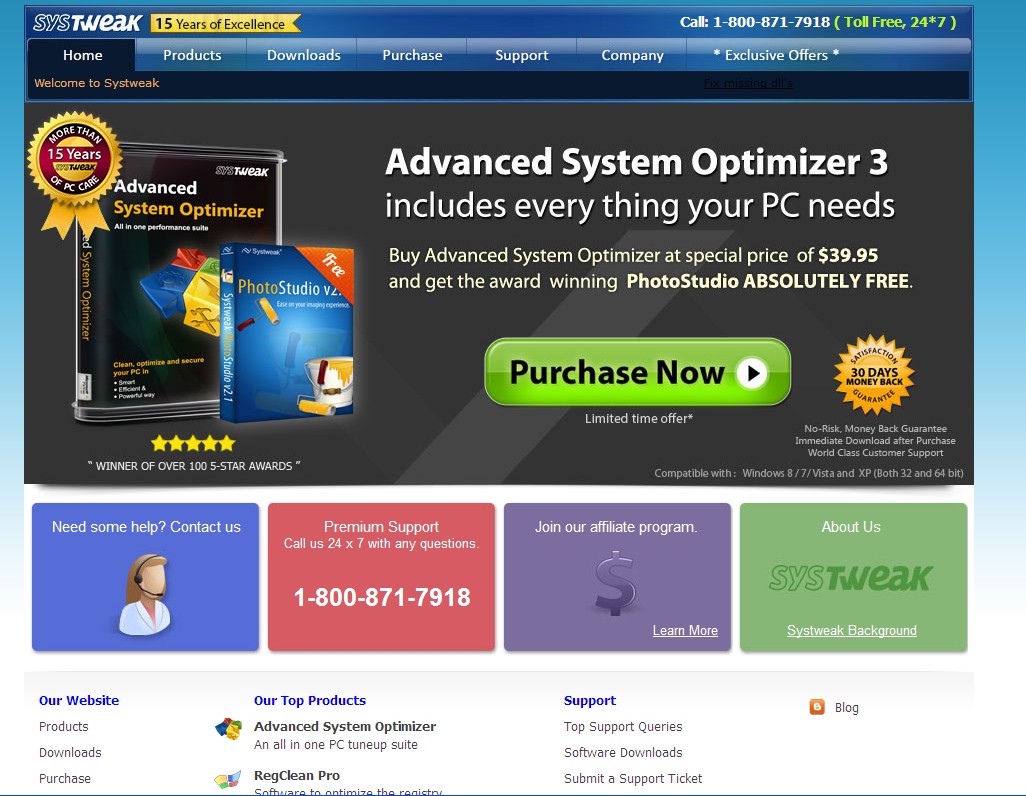
It is quite normal to see some specific web site promoting products. Today we have Systweak.com web page to promote a computer-friendly products – Advanced System Optimizer, RegClean Pro, Advanced driver updater, Advanced system protector and disk speedup. However, reports from most of PC users said that systweak.com would also come in as a piece of adware to randomly popup on people’s computer and ruin surfing experience. What’s more, systweak.com pops up to inform that about the bad performance of a target machine; which can not be the case for the time being, but it will make you believe that your machine is having problems as follows:
An upswing in BitCrypt ransomware activity keeps indiscriminately plaguing online computer users in greater numbers around the world. And quite a few of Internet users are suffering from incredible damage made by the ransomware. BitCrypt is regarded perilous ransomware, utilized by scammers aimed at threatening to format, encrypt and wipe all documents on the compromised computer. All files and data, pictures, and application development on the infectious computer have been encrypted to a series of inaccessible files in form of ekstra ekstension, ex: blabla.jpg.bitcrypt , blabla.xls.bitcrypt . etc. Like all other ransomware such as “Your personal files are encrypted” ransoware or CryptoLocker virus is meant to be an encipher of all files located on the victimized computer and Android phone. BitCrypt Ransomware also uses similar tactic to encrypt all files on the compromised computer and Android system.
Weather It Up was a tricky infection which was disguised as an useful web service and hypocritically provided the real-time weather forecast to please the Internet users so as to avoid being removed in the first place. Most of the users were interested in this kind of practical applications so when they found the Weather It Up was installed in the computer, they would rather keep it. However, what they didn’t know about the Weather It Up was the weather forecast program was actually an unwanted adware, which could take advantage of this occasion to notice the users about the weather and also displayed tons of pop-up ads to the users. Most of the advertising information provided by Weather It Up adware were related to tempting sales links with striking manners, with the main intention to draw the innocent users’ attention.
Trojan:Win32/Chenf.A is a high-risk security infection that is programmed with progressive hack techniques to disrupt a targeted computer significantly. Basically, Trojan:Win32/Chenf.A infection can always infiltrate onto a user’s computer without user’s authorization or knowledge, as the malicious payload is being delivered to computers with the aid of infamous BlackHole exploit kit, which is capable of inserting the virus into system by technically making use of found security vulnerabilities. Apart from the common trick, Trojan:Win32/Chenf.A virus is adept at take advantage of various social engineering tactics such as corrupted advertisements, phishing emails carrying links or attachments, or bogus security alters and update notification to get inside victim’s system. In reality, Trojan:Win32/Chenf.A is a non-self-replicating type of malware program that generally triggers abnormal symptoms on affected computer using its incidental codes and files. Upon its installation, Trojan:Win32/Chenf.A infection will typically make modification in default system configuration such as MBR (Master Boot Record) in order to be loaded up automatically on every Windows boot.
Before answering the question, one should be well informed that malware includes virus, ransomware, worms and the like. But AllCheapPrice is none of this; instead, it is a pop-up adware that thirst for traffic and sales promotion. As what we can see from its name and content, we know that AllCheapPrice is an advertising platform, similar to coupon sites, trying to offer some discounts. However, some undesirable scenes are triggered along with its appearance:
Though AllCheapPrice is not malware, harassed by it can be potentially dangerous, which is why dysfunctions occur and quick fix is always required. Keep reading to find out what the potential dangers are and the way to remove it completely from a computer. Any question will be gladly answered by VilmaTech Online Support if one starts live chat window here.
Key-Find.com is not a reputable website that has been universally recognized as a browser hijack virus, which has the capability to trigger website traffic as well as other damaging activities on the computer that it infects. It seems that Key-Find.com is committed to multiple search services specifically designed for the majority of Internet users. However, by making use of hack strategy such as DLL plug-in, BHO (Browser Helper Object) or WinsockLSP, Key-Find.com virus can always tamper Internet user’s browser significantly, including Internet Explorer, Mozilla Firefox and Google Chrome. Basically, Key-Find.com virus may insert its malicious codes and files in system for the purpose of making modification in web browser configuration such as DNS and web search provider. In this way, the existing homepage, start-up page or error page could be directly modified to various suspicious domain operated by cyber criminals. Furthermore, when users do search in its provided search engine or even legitimate one (eg. Yahoo,Google or Bing), Key-Find.com virus may redirect default search queries forcibly and hijack to its appointed search materials which have no association with the original ones.

VBS/Dinihou.G.2, like all other security malware is meant to be a quite perilous attack, which carefully crafted by intruders and released over the cyber world in order for stealing confidential data from the compromised computer. VBS/Dinihou.G.2, also publicly known as safa7_22.vbs virus, focuses on attacking computers above those that don’t employ strong security measures in machine or vulnerable. However, VBS/Dinihou.G.2 has ability to infiltrate on targeted computer though an advanced anti-virus program have installed on machine to fight against attacks. How tricky the VBS/Dinihou.G.2 virus is. The bad news is spammers have also started spreading such VBS/Dinihou.G.2 virus around the world and thousands of Internet users have become its victims. With malware being at the core of confidential information-stealing, propagating such BS/Dinihou.G.2 virus becomes hijackers’ main trick to acquire malicious profits. In this VBS/Dinihou.G.2 malware, spam campaigns and drive-by downloads have been the epidemic ways spammers or hijackers exploit to send security threats.
Getting infected with Arcadefrontier.com could be unimpressive for most of the computer users, and when they finally detected this unwanted adware infection, the computer and the browser were already filled up with tons of annoying pop-ups. In most cases, once the users surfed on the Internet, Arcadefrontier.com would seize the chance to displayed nonstop pop-ups, intending to draw the users’ attention and luring them to click on those purposive links, banners or button. Arcadefrontier.com could be considered as a promotion platform, mainly providing all the commercial advertising information so as to make money from the users. Have to say that most of the pop-ups of Arcadefrontier.com could be deceptive and harmful for the innocent users. Once the users were not vigilant enough and easily be tempted by all the traps set by by this malicious adware, they would be naturally led to unsafe websites like fraud sites, resulting irreparable losses.
