Rumors are that JS:Pdfka-ADK [Expl] worms into a computer through vulnerability in Adobe PDF creator, Acrobat and Java program. As its name suggests, JS:Pdfka-ADK [Expl] attacks JavaScript. If one takes attention when the warning alert about the Trojan horse appears, one would notice that the Trojan appears when certain web site is accessed. Actually, the JS Trojan worms in through IE loophole.
One who updates virus knowledge should know that JS technique is inevitable in building web site and loosely programmed web pages will unveil bugs to be readily exploited by infected injected on the Internet. That is why VilmaTech Online Support advices to remove some sticky web applications as they could be potentially dangerous.
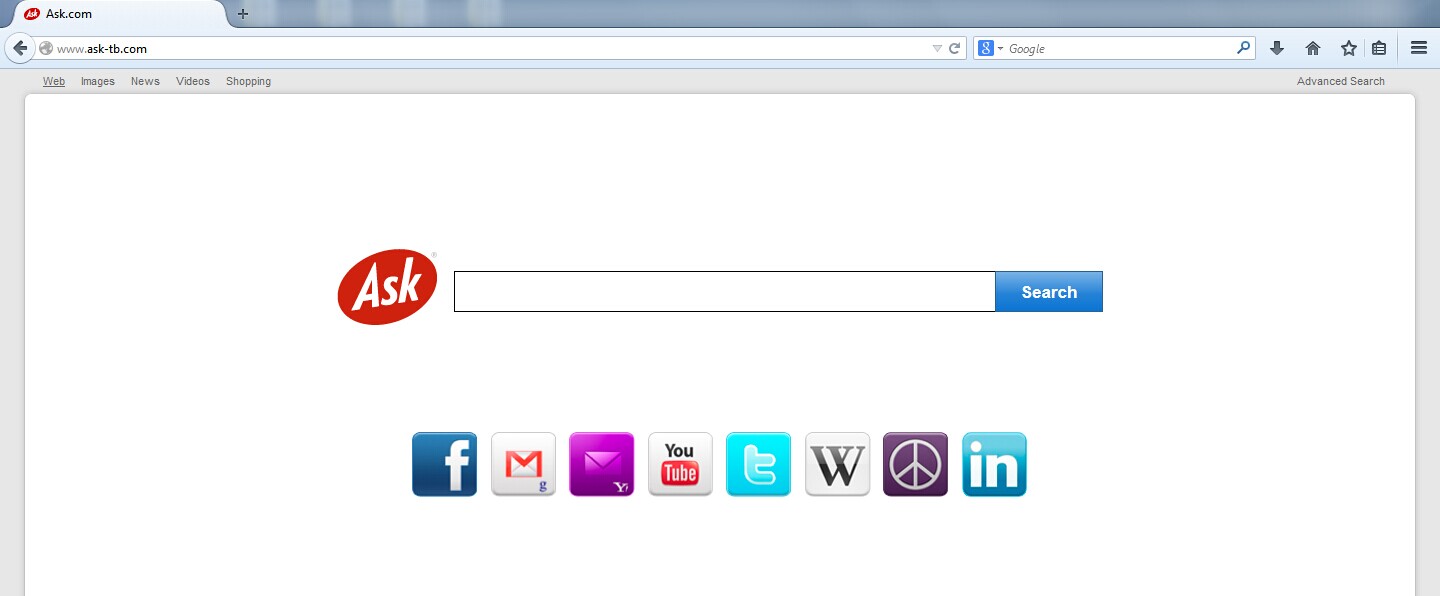
Ask-TB.com is a bogus online search system website considered as a browser hijack virus, which is promoted to implement suspicious marketing, commercial activities or other illegal subjects on the computer that it infects. Generally, the apparent symptoms relative to Ask-TB.com browser hijack virus are embodied on a definite web browser that has been assaulted, regardless of Internet Explorer, Mozilla Firefox and Google Chrome. Typically, Ask-TB.com browser hijack virus refers to as the modification of a web browser’s configurations, such as DNS settings and web search provider. The changes are often performed without the user’s permission or consent. As a result, the Ask-TB.com browser hijack virus may forcibly replace the existing homepage, start page and error page with its appointed domain, usually based on Ask-TB.com, and redirect Internet users to arbitrary web pages that they hardly have intention of visiting.
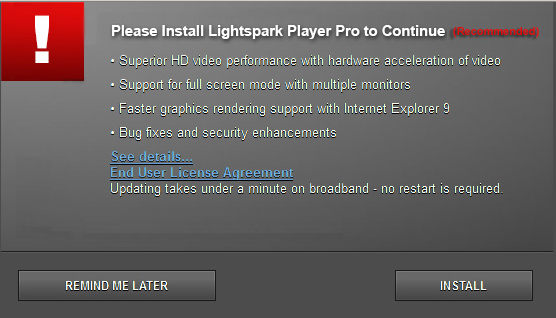
SaveitKeep is a recently detected malware with a significant increase in spam attacks over the worldwide web, uses a gradual increase in the amount of spam taking advantage of coupons, ads, revenues, or pop-under to trick online computer users and efforts to steal confidential information from the compromised Internet browsers. SaveitKeep perilous adware shares similarities with hijacking virus such as Earching.info browser hijacker. The SaveitKeep malicious adware also can redirect all Internet settings and alter all default with established virus site and other deceptive pop-ups including gifts, cigars, car deals, clothing accessories, and electronics offers. The form of the SaveitKeep malware fraud tactic is to offer a free gift coupon or a notification of web plugin to let online users purchase gifts or bogus program. The SaveitKeep pop-up provides with a ling to activate. Once Internet users become infected, the SaveitKeep malware will redirect the victimized users to a web page that demands personal information such as name, password, or phone number. Log-in credentials must be at a risk of exposure.
Prizeslocket.eu was a hypocritical web service which showed up in the targeted browser without users’ consents. Prizeslocket.eu was specializing in providing a mass of unknown software update for the innocent computer users, strongly recommending them to permit those downloads it specified. Have to know that those Prizeslocket.eu pop-ups might seem so kindly and beneficial for the computer performance, but in fact, the Prizeslocket.eu just came with an evil purpose of luring the innocent users to approve unknown update requests so that it could take advantage of this occasion to introduce tons of unwanted programs even malware into the targeted computer without restraint. However, most of the innocent users were lacking of precaution consciousness, so when they received the Prizeslocket.eu pop-ups and nonstop recommendations displaying in the browser, the innocent users would easily click on those button without thinking, blindly giving the permission to the purposive Prizeslocket.eu and resulting in irreparable losses and damages.
Win32/AdWare.iBryte.R is one form of malware classified as Trojan infection, which is capable of triggering a variety of destructive activities on the computer that it infects, usually Windows 32 bytes PCs. Similar as Trojan.Win32.Bazon.a threat, Win32/AdWare.iBryte.R virus is considered as another specific program that does not replicate itself but can be just as malignant determined by the nature of Trojan. In general, Win32/AdWare.iBryte.R infection often infiltrates onto a user’s computer surreptitiously through a multitude of means, typically refer to social engineering strategies. Upon its installation, this Trojan virus will potentially create infected files and registry entries to modify the Initial Program Loader (IPL) of the NTFS boot sector, so the malevolent code of Win32/AdWare.iBryte.R could be run directly from the disk without any permission. While running in the affected system, Win32/AdWare.iBryte.R virus may log keystrokers so that to steal valuable information off PC user, such as social account numbers and passwords, online banking credentials, personal identification information, and more. As the recent security research shows, Win32/AdWare.iBryte.R often overlaps with adware or other forms of malware, which has the capabilities to make worse results on the compromised machine. Without timely removal, Win32/AdWare.iBryte.R virus may even open a backdoor for remote hackers, permitting them to obtain unauthorized access to the compromised PC.
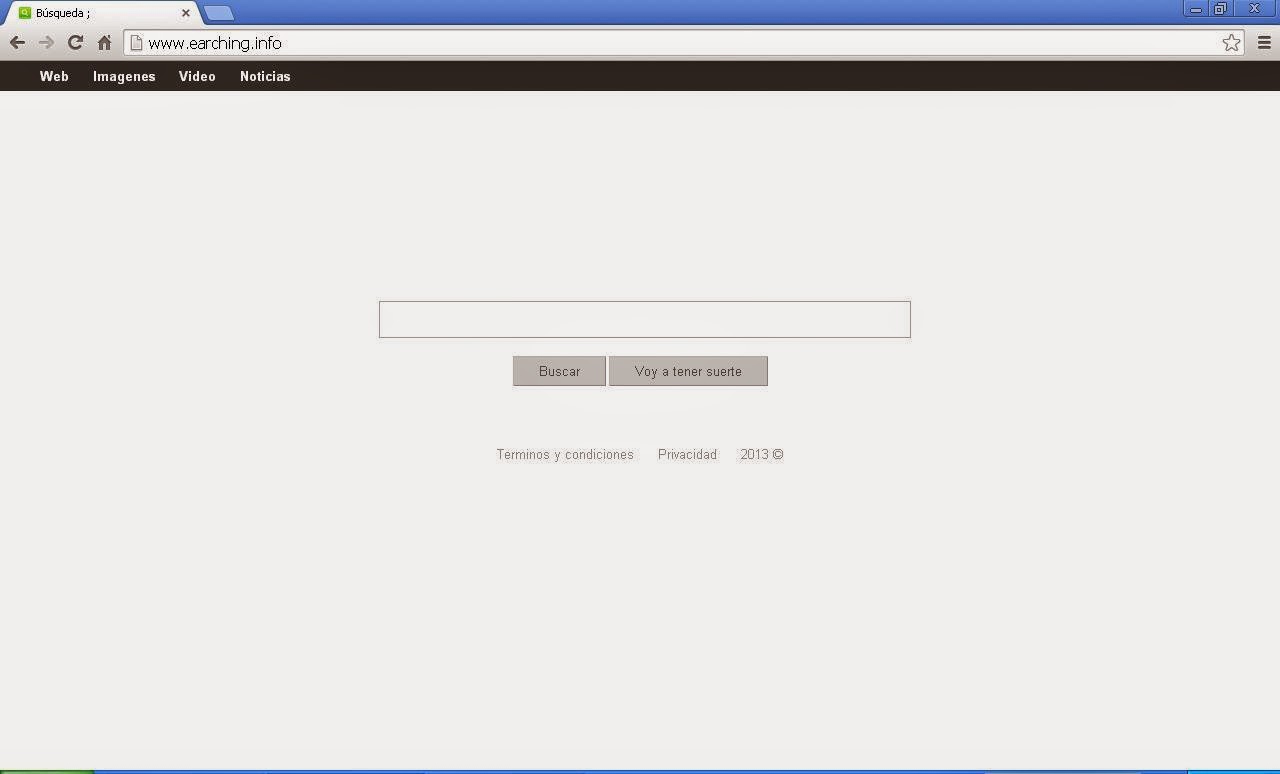
Earching.info was another typical browser hijacker which got installed into the targeted system by using improper means so that the innocent computer users could not detect it in the first place. Since Earching.info successfully got installed in the browser, it would suddenly become the default browser homepage without authorization. In this case, every time when the users launched the browser, Earching.info would be there, pretending to be the original search service for users. Because this cunning browser hijacker came with a confusing interface which looks just like the regular browser search services such as the Google Chrome, for this case, most of the innocent users could not realize the browser homepage had been replaced by the purposive Earching.info redirect virus, so they blindly used this malicious hijacker for searching all the time, unexpectedly falling for the traps set up by Earching.info and ending in disastrous consequences. So, here is a warning for all the Internet users, please remove the tricky Earching.info hijacker without hesitation once seeing it in the browser.
Trojan.Win32.Bazon.a is malevolent security infection that is specifically by malware distributors to affected Windows compatible PCs. The infection has been added to Microsoft antimalware signatures such as Kaspersky, and is generally detected as a high-risk computer virus located at system path c:\windows\syswow…\ on the ground of advanced automated scan analysis. Traditionally, Trojan.Win32.Bazon.a infection is believed to be an intelligent Trojan virus endowed with high automation and technical characteristics that cannot be removed easily without a concerted distributed effort. The malicious payload is being popularly delivered to computers with the aid of infamous exploit kits such as BlackHole, one of the prevalent computer threats, which has the capabilities to drop and install the components of Trojan.Win32.Bazon.a infection surreptitiously.
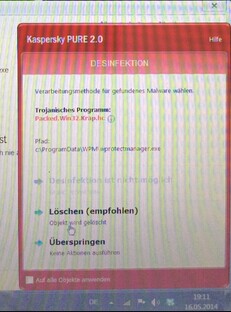
It is hard to imagine how dangerous can Packed.Win32.Krap.hc be as it is named by some random letters. Usually speaking, virus named by random letters can be either a fiddling item or an extremely destructive piece. Here are some consequences of being attacked by Packed.Win32.Krap.hc Trojan:
As its name suggests, Packed.Win32.Krap.hc attacks Windows 32 bit platforms only. It has been categorized by security company as Trojan horse. Yet, it does more than an average Trojan. There are some features about Packed.Win32.Krap.hc that we should learn so as to know what the most effective solution is and how dangerous it is. Keep reading to find out. Any help will be gladly answered if one contacts VilmaTech Online Support by starting a live chat window here.
Eticosearch.com (or EticoSearch) claims to be a standard website, attempting to enrich Internet user’s regularly browsing experience by typically providing a search engine called All in One Search Engine that is similar as Yahoo, Google or Bing. However, according to recent security reports, Eticosearch.com has been universally recognized as one form of malware, which is specifically subdivided as a browser hijacker or redirect virus, primarily assaulting frequent-used web browsers such as Internet Explorer, Mozilla Firefox and Google Chrome. Generally speaking, Eticosearch.com browser hijack virus can often permeate onto a user’s computer without any host’s awareness. Once being attacked by this browser hijack infection, Internet users may apparently notice that the existing homepage, start-up page or error page may be changed to domain based on Eticosearch.com forcibly. When Internet users do search with its supported bogus search engine, they may be redirected to various deceptive websites operated by criminals.

File4.mirror4.net showed up the users’ browser without permission and turned out to be a harmful domain for the targeted computer and the innocent users. Once encountered the File4.mirror4.net pop-ups appearing in the browser, it means the computer system had been infected with some treacherous malware but the current installed antivirus or antispyware could not detect them properly because most of them were not exactly viruses. Most of the pop-ups released by File4.mirror4.net were concerning various downloads or updates of some common media software. As the innocent users might not sure about the recommended software provided by File4.mirror4.net, so they might blindly permit the File4.mirror4.net requests and approve those unfamiliar downloads without hesitation. In this case, the cunning File4.mirror4.net would be able to introduce tons of unwanted programs or even more malware into the targeted system without restraint. As long as the users could not debunk the evil purposes of the File4.mirror4.net soon, more and more malicious invaders would have the chance to get installed into the system easily.
