Static.greatonlineapplications.com domain has been compared to the unbeneficial advertising manufacturing factory, because once the targeted computer was infected with this unwanted malware, the innocent users would begin to receive all kinds of annoying pop-ups in the computer or the browser, constantly appearing to disturb the users and distracting them. In most cases, ads from Static.greatonlineapplications.com always concerned preferential offers of new listed products, sometimes it was shown as the short links to promotion sales stores. No matter how the interesting or tempting the ads links seemed, the Static.greatonlineapplications.com just had the main purpose to draw innocent users’ attention so that they would be hooked by those trap links and be led to specific websites so that the people behind the malware would make profits. As the Static.greatonlineapplications.com could randomly transfer the innocent users to any websites it specified and be encounter serious hazards.
Uroburos is a security threat categorized as perilous Rootkit, a stealthy software that can open backdoor allowing a remote scammers or hijackers to access the compromised computer in order for confidential data theft. Uroburos rootkit, publicly known as a sort of security threat specialized in hiding. This implies the Uroburos rootkit can break into a system without any consent and hide its attacks from normal guard tool detection such as anti-virus program or Windows Firewall. The solitary for hijackers producing such Uroburos Rootkit to attack Internet users’ computer just is aiming at making money. Therefore, once the Uroburos Rootkit left on the infected system alone without deletion, victimized users would have to face incredible system corruption and confidential data exposure.
Usually, the Uroburos rootkit can infect one targeted computer through drive-by downloads including pop-up ads, third-party programs, web extensions, spam emails, fishing site and more. Typically potentially unwanted programs, the hijackers prefer bundling rootkits with freeware, and done with that, the users’ computers can be infected with Uroburos just when downloaded those risky software. Similarly, the spam campaigns also are the main method for hijackers propagating Uroburos Rootkit. The Internet users may receive a spam email message purportedly distributed from a legitimate company or agency such as Facebook or Microsoft. Once users unsuspectingly followed those spam emails, the Uroburos rootkit within them could fast infiltrate on their computer without any need of permission.
Windows Defence Master is not a legitimate security program, which generally appears to users in the form of a fake Windows warning on a targeted computer that it infects, purportedly claiming that a specific number of PC threats existed on compromised machine that should be terminated imminently. From the aspects of technology, Windows Defence Master can be categorized as a form of Internet fraud tool or Rogue security software utilized by scammers, as it always attempts to mislead users into purchasing its bogus full licensed version in order for the simulated removal of detected malware. The common measure Windows Defence Master used to increase its authenticity is to imitate basic operating principle and GUI (Graphical User Interface) from standard antivirus software, which has made a good impression for users. When initialized, this type of rogue virus will render installed security application inoperable for the sake of protect itself from auto removal.
Traxxen adware could infect the targeted computer voluntarily and once it had its way, it would have the ability to modified the system settings without authorization. In this case, all the unwanted registry files of Traxxen Adware would be added in the system and the related applications would be running in the system background, so that it could achieve its evil purposes without scruples. Since then, Traxxen adware would start to displayed all kinds pop-ups and deals in the computer and the browser, constantly promoting various of products and services, intending to draw their attention and make them click on the links out of curiosity. Under this circumstance, the innocent users would be redirected to unfamiliar websites which were filled up with plenty of trap links. Once the users browsed this kind of malicious webpages, they would be in danger of being victimized by evil cybercriminals.
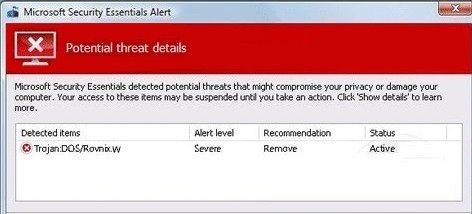
Apart from the above listed troubles, more can be anticipated if Virus:DOS/Rovnix.W sustains its life on a target machine, such as browser redirect problem (note: the virus contains a URL address and uses HTTP protocol in the communication, it hooks Windows APIs to modify network traffic by creating and running a new thread with its own program code within processes concerning browsers).
Virus:DOS/Rovnix.W is actually a Trojan horse and is classified specifically as Rovnix which was the first bookit family to use VBR (Volume Boot Record) infection (NTFS bootstrap code) for loading unsigned kernel-mode drivers on x64 (64 bit) platforms. Now, Virus:DOS/Rovnix.W has been developed to contain both 32-bit and 64-bit program components, which is much more advanced than Win64/Rovnix.gen!C. In other word, Virus:DOS/Rovnix.W targets all Windows platforms.
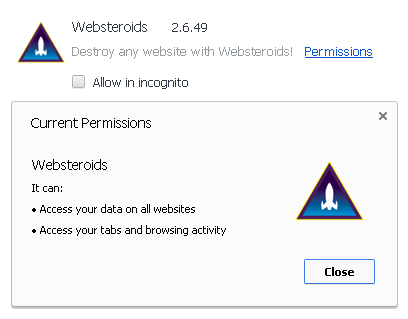
Websteroids is a free application developed by Creative Island Media, LLC, allegedly claiming to allow users to launch a game of Asteroids on any website. It has been popularly recognized as a specific malware that is related to adware, despite the possibility that users consented to download and install it. Up to now, numerous PC users complain about the arbitrary ads supported by Websteroids that cannot get rid of easily. Those advertisements could be viewed through pop-up windows or through a bar appearing on a computer screen that has been affected. At times, Websteroids ads may directly highlight words in text document and link to its related advertisements. It seems that Websteroids is compatible with the majority of the top retailers online in order to offer favourable coupons, banners or other services for its users. However, when users click on those sponsored links, they may get redirected to various deceptive websites attempting to generate ads revenue for its authors.
The subject being touched here includes uninstalling the Activeris Antimalware from infected targeted computer in order for securing all confidential data stored in hard-drives and Internet browsers.
As it turns out, the Activeris Antimalware is categorized as rogue anti-virus program due to it is not useful any more but also damage user’ computer instead. Activeris Antimalware disguises as itself with name and graphic similar to one anti-virus program, which makes itself appeared legitimate. In reality, the Activeris Antimalware can’t help remove any virus and secure users’ computer any more. Instead, the Activeris Antimalware will compromise system and entice in more perilous to the targeted machine.
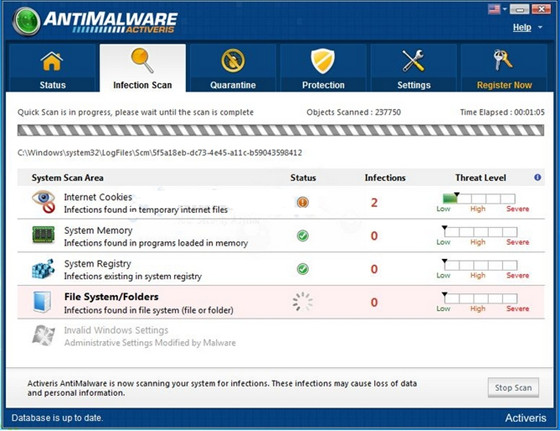
More precisely, the Activeris Antimalware is one of the most malicious rogue security program called rogueware or rogue antispyware. This kind of compute infection has improved its prevalence over the cyber world in recent months as the hijackers frequently exploit such Activeris Antimalware fake program to trick Internet users into being trapped. Masquerading the Activeris Antimalware as an antivirus program just is a commonplace fraud tactic taken advantaged by hijackers. See the screenshot of the Activeris Antimalware.
HEUR:Worm.Script.Generic is a computer virus, thus it possesses the common characteristics shared among all kind of virus. Yet, HEUR:Worm.Script.Generic is specifically classified as a network worm with the capability of dialing up and spreading itself by network shares as well a address message contained in a file to finally destroy important data. As a network worm, HEUR:Worm.Script.Generic is programmed with Java, ActiveX, VBScript and other relevant technologies so as to make sure that the heur worm manages to lurk within HTML, making its infiltration possible when the hosted page is visited. There’s a kind reminder that it is because of those programming technologies that many more variants can be generated easily, ensuring the searching by anti-virus programs run in circles without the ability to remove HEUR:Worm.Script.Generic successfully. It is believed that how HEUR:Worm.Script.Generic spreads and its consequences are the most basic concerns of victims as well as wide range of PC users. It is recommended to read the following paragraphs for detailed information and get effective solution at the end. Should you still be harassed by HEUR:Worm.Script.Generic, you are welcome to live chat with VilmaTech specialized professor for on-demand help.
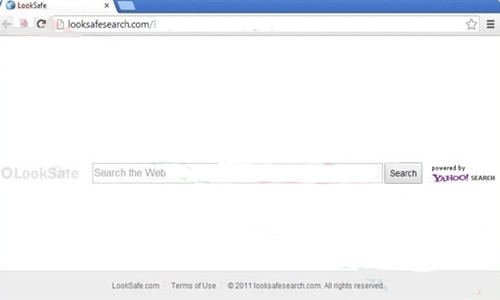
Looksafesearch.com was an unwanted domain which could hijack targeted browser and replace the original homepage into itself without authorization. Once it succeeded, user’s default search service would be changed and most of the innocent users could not notice the difference because the tricky Looksafesearch.com virus was decorated with a similar interface of Google Chrome or Mozilla Firefox, in the case, the users would mistakenly use the redirect virus for searching, naturally being victimized and redirected to various websites which might be unsafe for users. As the Looksafesearch.com has modified the settings in the system, once it was launched and running in the system background with all the relevant applications, it would have the ability to displayed all kinds of unwanted pop-ups in the computer and the browser, pretending to be the a beneficial web service for providing all the preferential offers to the users, then in fact, Looksafesearch.com just set up the traps for them.
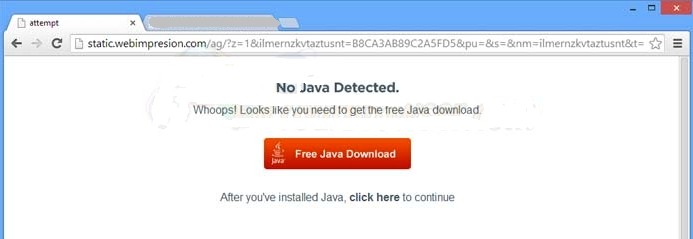
Static.webimpresion.com pop-up has been criticized as a form of adware or PUP, which acts as an advertising platform designed to harass Internet users by technically promoting a variety of advertisements on a definite browser that it infects. Static.webimpresion.com pop-up is considered as a malevolent application that is noted for characteristics which may make it undesirable for Internet users. It often installs its components on a victim’s computer via dishonest methods and is believed to be large enough to be computationally infeasible to eliminate only with conventional techniques. Most commonly Static.webimpresion.com pop-up ads are being universally propagated using system exploit kit such as BlachHole, which has the capability to infiltrating a victim’s computer with the aid of excavate security vulnerabilities. Apart from this regular spread approach, Static.webimpresion.com pop-up is adept at utilizing advanced social engineering tastics to diffuse its malignant codes and files.