Information Security and Control Act message is a counterfeit one that attaches Garda (Irish police) logo in the corner of the screen and an email address with the name resembles the genuine one to make it look official. Such fake message raged in 2012 and has cheated wide range of PC users and Android phone users into submitting a fine of 100 Euro to release it by sealing the whole screen. Legal as Information Security and Control Act virus Android lock looks like, it is a form a virus, which is identified as ransomware, supported by Trojan. With the help of typical technique of a Trojan, Information Security and Control Act virus manages to display the counterfeit page with corresponding language, governmental departments according to the detected IP address and the language of the target system. In other word, Information Security and Control Act virus Android malware is capable of extracting personal information of victims.
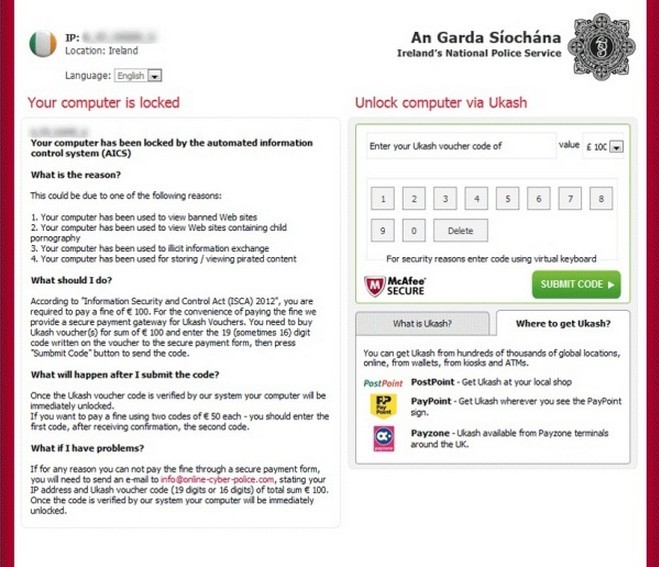
(The most widely seen version of Information Security and Control Act virus)
As of the day when computers are connected through Internet, network security grows with the development of the Internet. Infiltration of Information Security and Control Act virus is one of the infections that is good at taking advantage of network. By exploiting vulnerability on installed programs, especially browsers (e.g. IE, Mozilla Firefox, Google Chrome), or distributing links to download virus through chat tools/E-mails, ISCA virus manages to propagate vicious codes and implant its Trojan into the web of the victim. Shortly after that, Information Security and Control Act virus starts to read its payloads:
※ Discharges its copies to catalog like %Application Data%\{random}.exe under the current user in C Disk.
※ Creates Mutex to assure that no other programs will be able to run before Information Security and Control Act virus when the Windows starts.
※ Adds its auto startup item to
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run CryptoLocker = “%Application Data%\{random}.exe”
※ Adds values in database under
HKEY_CURRENT_USER\Software\CryptoLocker
HKEY_CURRENT_USER\Software\CryptoLocker\Files
※ Acquires encryption key by connecting to a couple of websites pointing to its remote server.
※ Search for all system catalogs and mapping drivers to overwrite them and encrypt the source ones to urge victims to submit the non-existent ransom so fix in the counterfeit message.

From the aforementioned payloads, it is easy to understand that Information Security and Control Act virus is capable of disabling build-in services of a target computer. Therefore, victims is likely to encounter some of the troubles listed below:
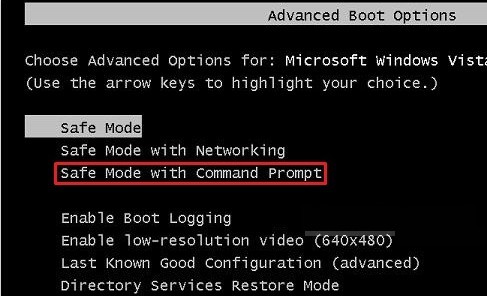
※ Safe Mode with Networking cannot be accessed.
※ Safe Mode with Command Prompt cannot be accessed.
※ F8 key will not take users into ‘Windows Advanced Options’ section.
※ White screen happens in Safe Mode.
※ System Restore and System Repair cannot complete.
It is worth of the mentioning that the longer Information Security and Control Act virus survives on a target computer, the more dysfunctions will be met, and sadly, more infections and residual damages will occur even after one successfully removes Information Security and Control Act virus. All these are due to the backdoor formed after it modifies database to its satisfactory. To close the backdoor timely and avoid being plagued by additional troubles, efficient and feasible method is in desperate need. Utilization of anti-virus programs are always needed to help troubleshoot problems in the first place. Yet it is not sufficient to help remove Information Security and Control Act virus completely since the ransomware affects driver and running process to make installed security utilities pinpoint the fake directory. According to what victims told, running Malwarebytes Anti-malware in Safe Mode can only help delete a couple of dangerous files without thorough removal of ISCA virus. More over, given that all build-in services to help troubleshoot problems are disabled, manual method is the ultimate way that stands a chance to remove Information Security and Control Act virus completely.
Actually, one can be free from ransomware like Information Security and Control Act virus if one takes safety precautions regularly to prevent any occurrence of vulnerability.
※ Download the up-to-date patches for installed browsers and apply them into use.
※ Always activate Windows Firewall or the ones of other reputable anti-virus programs.
※ Adopt IDS (Intrusion Detect System) to analyze collected information from computer networks or computing system in an attempt to help detect any action violating security policy and sign of under attack.
※ Utilize Web Monitor to help fliter queries and give proper search results as well as superviser International information.
※ Block connections to vicious web sites at gateway.
※ Update your virus signatures on a regular base.
※ Do not click open any attachments in an Email sent by strangers.
※ Do not accept and run files/ documents sent through chat tools casually.
※ No visit to unknown foreign web sites, especially the ones containing pornographic content or offering video downloads.

Situation One: ‘Safe Mode with Networking’ is available.
★ Boot into Safe Mode with Networking.
> Stay at the sealed screen by Information Security and Control Act virus.
> Press Alt,Ctrl and delete key together.
> locate power icon at the right bottom of the blue screen.
> Please hold shift key and click on power button together.
> Select Restart.
> Select Troubleshoot with arrow keys.
> Select Advanced options.
> Hit Restart button at the right bottom of the screen.
> Please hit F5 to get into safe mode with networking.
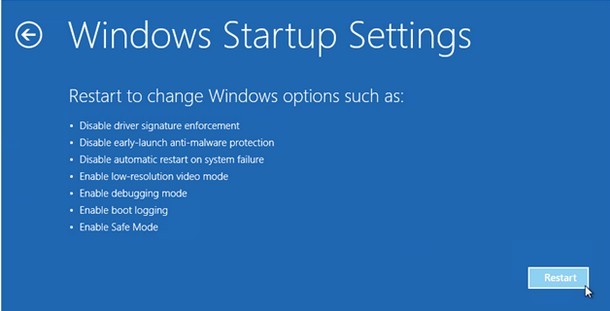
(Generally speaking, Windows XP would be corrupted so drastically that unable to run any forms of safe mode.)
> As the computer is booting but before Windows launches, keep tapping on “F8 key” continuously.

> “Windows Advanced Options Menu” prompts up.
> Highlight “Safe Mode with Networking” option.
> Press Enter key.
★ Disable startup items associated with Information Security and Control Act virus in Safe Mode with Networking.
> Start screen.
> Type ‘Task’.
> Hit Enter key.
> Find and tick items related to Information Security and Control Act virus.
> Press ‘Disable’ option to remove Information Security and Control Act virus.
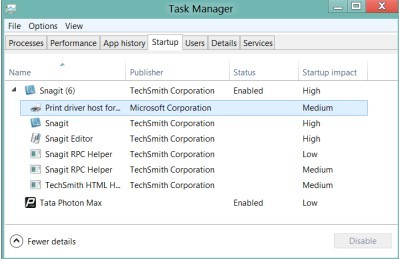
> Start menu.
> Launch Search/ Run box.
> Type ‘msconfig’.
> Hit Enter key.
> Find and tick items related to Information Security and Control Act virus.
> Press ‘Disable All’ option to remove Information Security and Control Act virus.
★ Re-manage database (registry editor)
> Move your mouse over lower right screen.
> Click Search charm.
> Type ‘regedit’.
> Hit Enter key.
> Press and hold Ctrl+F to search for Winlogon.

> Locate key labeled Shell in the right pane.
> Right click on it and replace it with ‘explorer.exe’ to help remove Information Security and Control Act virus.
> Click “start”.
> Put ‘regedit’ in Run box.
> Press Enter.
> Press and hold Ctrl+F to search for Winlogon.
> Locate key labeled Shell in the right pane.
> Right click on it and replace it with ‘explorer.exe’ to help remove Information Security and Control Act virus.
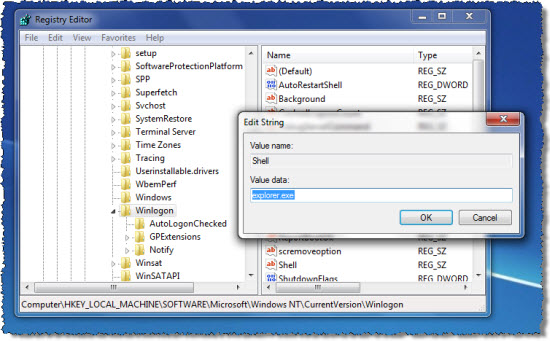
★ Show hidden files to remove Information Security and Control Act virus.
> Stay at the sealed screen by Information Security and Control Act virus.
> Open Windows Explorer by clicking on Windows Explorer application from Start Screen.
> Select View tab on Windows Explorer window, you will get numbers of options.
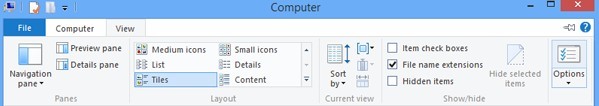
> Tick ‘File name extensions’ and ‘Hidden items’ options.
> Navigate to Roaming folder and Temp folder respectively in Drive C to remove files with abnormal name, such as serial numbers with random letters.
> Open ‘Control Panel’ from Start menu and search for ‘Folder Options’.
> Under View tab to tick ‘Show hidden files and folders and non-tick Hide protected operating system files (Recommended)’ and then click ‘OK’.
> Navigate to Roaming folder and Temp folder respectively in Drive C to remove files with abnormal name, such as serial numbers with random letters.
★ Save changes, reboot to normal mode to see if Information Security and Control Act virus is gone.

Situation 2: ‘Safe Mode with Command Prompt’ is available.
★ Boot into Safe Mode with Command Prompt.
> Please press Alt,Ctrl and delete key together, you will see a blue screen with a power icon at the right bottom.
> Please hold shift key and click on power button together.
> Please select Troubleshoot with arrow keys.
> Select Advanced options.
> Hit Restart button at the right bottom of the screen.
> Please hit F6 to get into safe mode with command prompt.
> As the computer is booting but before Windows launches, keep tapping “F8 key” continuously.
> “Windows Advanced Options Menu” comes up.
> Highlight “Safe Mode with Command Prompt” option.
> Press Enter key.
★ Create a new user account from cmd.
> Type ‘explore’.
> Hit Enter key to see if you are able to see the desktop.
> Created a new user account with administrator right.
★ Remove Information Security and Control Act virus in the newly created user account.
> Restart the computer normally.
> Enter into the newly created user account.
> Follow steps depicted in the ‘Safe Mode with Networking’ section after booting into Safe Mode with Networking.
Situation 3: none of all forms of safe mode is available.
★ Reboot your computer and log into ‘Repair Your PC’.
> Insert Windows XP CD into the drive (if Autoplay kicks in, exit out of it).
> Click on Start -> Run.
> Copy and Paste ‘sfc /scannow’ within the text box.
> Windows File Protection Service scans all protected files and verifies integrity, replacing any files with which it finds a problem.
> Be patient and allow this process to proceed completely.
> Restart your computer once this process is completed.
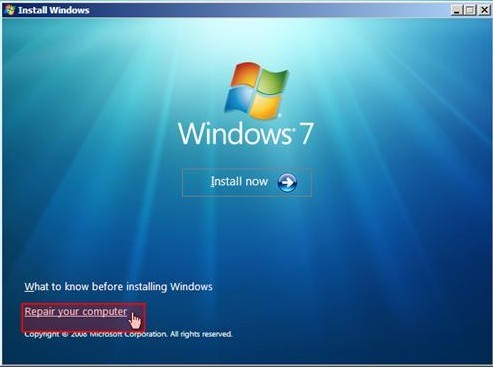
> Put Windows 7 CD in your optical drive
> Restart to boot from the DVD.
> On the “Install Windows” screen, make the appropriate selections for language, time, and keyboard, and then click “Next”.
> On the next screen, click “Repair Your Computer”.
> In “System Recovery Options”, select which operating system you want to restore if any are listed, and click “Next”.
> The “System Recovery Options” screen shows up and select “Startup Repair”.
> Start Screen.
> Type ‘Advanced’.
> Click Settings category.
> Select Advanced startup options.
> General PC Settings screen appears.
> Scroll down to the bottom to select Advanced startup.
> Press on Restart now.
> Select Troubleshoot.
> Select Advanced options.
> Click on Automatic Repair.
> Log in the User Account you wish to repair.
> Automatic repair will now start.
> After a while, your computer will automatically restart; please leave it to complete all the process.

> Insert Windows Vista DVD and restart the computer with the DVD in.
> ‘Press any key to boot from CD or DVD’ is displayed in black background.
> Press any key to start the booting process.
> A new screen will appear saying ‘Windows is loading files’.
> Another small progress bar appears after several minutes.
> Select your language and keyboard language and click Next button when you are given options.
> Click on the Repair Your Computer option at the bottom left of install screen.
> Once the ‘Vista installation’ is located, highlight it and then click the Next button.
> You will see the picture below:
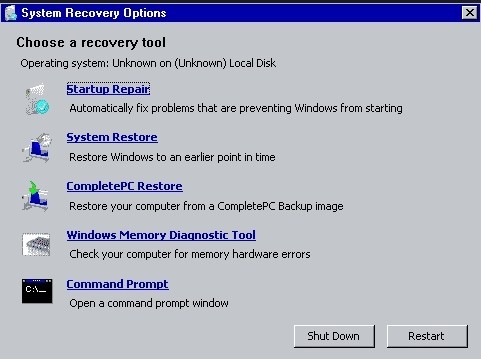
> Click on Startup Repair and let the wizard finish.
> It is perfectly normal that the computer restarts after it finishes the process.
> stay on safari displaying Information Security and Control Act virus.
> Go to Safari menu.
> Choose ‘Reset Safari’.
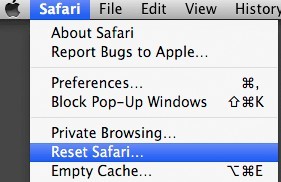
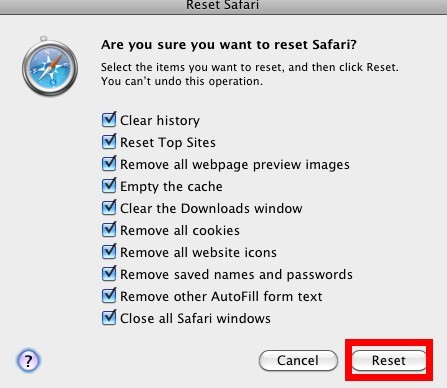
> Tick all given options.
> Press ‘Reset’ to confirm the change.
> Click on the search icon on the right-up corner of the screen.
> Type safari (the browser that has Information Security and Control Act virus) on the search box.
> Choose safari by clicking on it once.
> U.S.A. Cyber Crime Investigations virus will be gone by now.
Many computer users may encounter the slow performance of system after the removal of Information Security and Control Act virus. Here introduces common methods to help users speed up their computers effectively.
1. Clean up hard drive regularly. Hard drive is one part of system, which is responsible for storing and providing relatively quick access to large amounts of data. Suppose that users don’t clean up hard drive termly, it must include a large number of useless files such as songs, games, pictures, video files, etc. As a consequence, the redundant data stored on hard drive can occupy high system resource so that to cause sluggish system performance. Thereupon computer users are obliged to clean up hard drive regularly to maintain PC’s normal operation.
2. Remove additional programs that unneeded. In many cases, computer users may forget the specific programs installed on PC which are needless thoroughly. However those extra programs may take up large amounts of RAM to slow down the performance of system significantly and even lead to other unexpected problems on computer such as constant freezes. Hence, it is recommended to remove additional programs or unwanted applications from computer in order to optimize the performance of computer.
Important Tips:
Documents can be deleted by Information Security and Control Act virus Android malware if it has loaded down the codes to do so. Hence it is necessary to backup important documents. If one finds that personal information is abused, one can go to www.google.com/remove.html and submit the information that one doesn’t want Google search engine to inquire. As regard to the residual damages, among which are search result redirect problem, endless popup issue, obtaining unrelated search results, hijacked homepage, additional installations of unknown programs, sluggish PC performance and error messages, one should go to the security board to search for solutions to specific Android virus and particular issues in a bid to regain healthy computer. The last but not least, change all password that once typed onto the computer after removing all suspicious items and remove all potential Android infections, restart the computer to save changes.
