TeslaCrypt is a new type of ransomware that severely affects users’ PCs while encrypting personal files with state of the art hack technology. One of the main disrupting skills TeslaCrypt adopts is leading Windows screen locker that usually appears to users in the form of a bogus notification on the monitor, forcibly limiting every regular PC routine for PC users. However, the precondition of the attacking activities by TeslaCrypt ransomware cannot be short of the rock-ribbed personal files encryption on a targeted machine. This may refer to people’s photos, videos, documents, etc. According to the announcement by TeslaCrypt scam, users can view the complete list of encrypted files through clicking “Show encrypted files” on the screen alert. The encryption algorithm used by TeslaCrypt ransomware is the Advanced Encryption Standard (AES), which has generated a unique public key for a targeted computer that can be used to decrypt all personal files stored on affected system, regardless of Windows 7, Windows XP, Windows Vista or Windows 8 in recent. To get the private key for decryption, TeslaCrypt threat generally demands victims to pay a sum of money about $500 USD in Bitcoins or $1000 USD in PayPal My Cash Cards.
One fact must be realized that TeslaCrypt only serves as a hazardous PC infection categorized ransomware and it requires timely elimination in order for the restriction and encryption security issues to be resolved. Nevertheless, to mislead innocent PC users, TeslaCrypt may also claims that any attempt to remove or corrupt the program will lead to instant & lasting disruption of the one of a kind private key by the server. It is certainly inveracious so that users should try their best to get rid of TeslaCrypt ransomware once being informed of its abnormal symptoms. By adding a series of harmful files on the compromised machine such as HELP_ TO_DECRYPT_YOUR_FILES.txt, TeslaCrypt virus cannot be handled with conventional technique. Without prompt interaction, this stubborn TeslaCrypt ransomware may result in other variety of damaging issues on the computer that it attacks. This may include the sluggish PC performance by occupying high system resource, rebarbative website traffic, unknown system errors displaying on the desktop, extra installation of spyware, malware or other unclear subjects. In some serious scenarios, TeslaCrypt ransom virus may also lead to computer crash and further data loss.
Note: TeslaCrypt ransowmare cannot be handled by easy approach. If you cannot get rid of TeslaCrypt threat alone and need some help during the removal, please be free to contact VilmaTech Certified 24/7 online expert here, who would like to offer professional and real-time support.
The payload of TeslaCrypt ransom virus may be delivered by compromised websites including some P2P file sharing web pages or some legitimate social communicate websites. PC users may also get infected with TeslaCrypt infection by opening some distrusted links or attachment from a spam email. Apart from those propagating methods, TeslaCrypt ransomware may also sneak into your computer without asking for any approval via freeware/shareware carrying the activation code of the virus. Simply put, PC users should be cautious when using any unreliable Internet resource to avoid unwanted damages and infections.
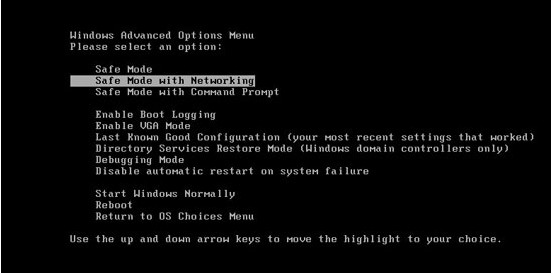
1. Boot your computer into Safe Mode with Networking.

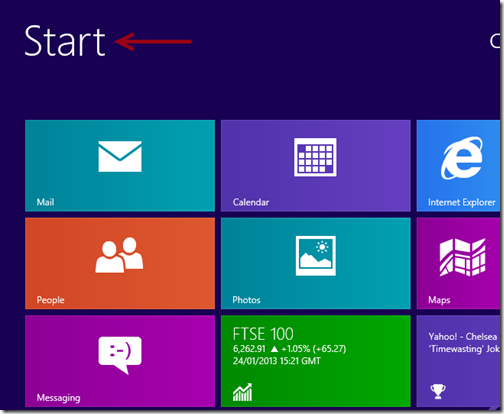
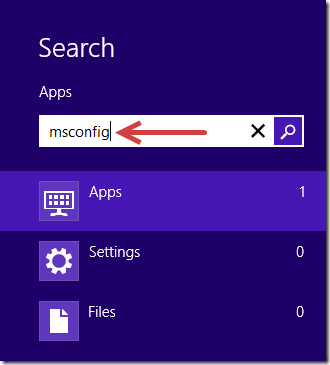
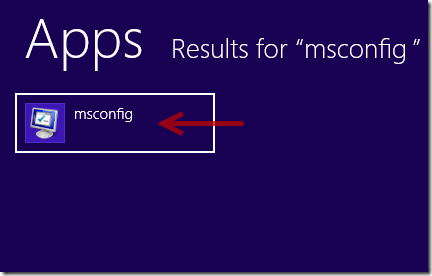
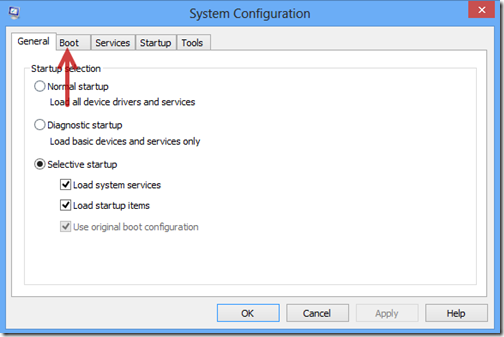
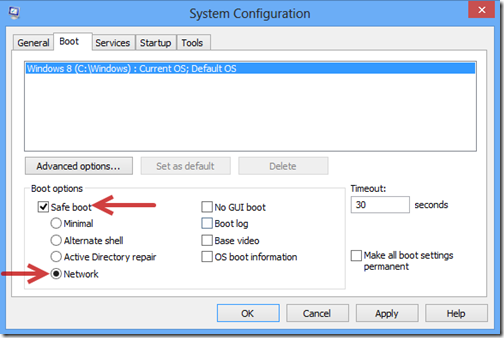
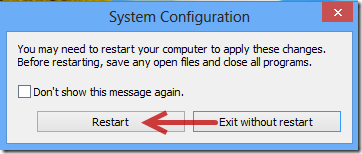
2. Clean up all files and registry entries created by TeslaCrypt ransom virus.
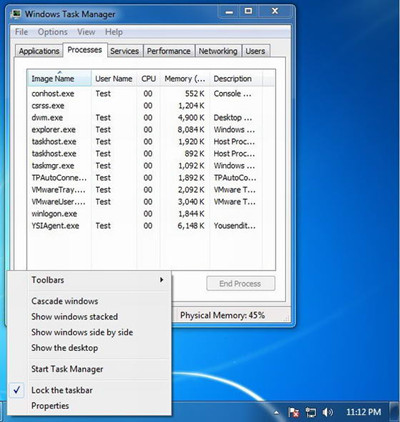
%AppData%\Protector-[random].exe
%AppData%\result.db
%UserProfile%\Desktop\TeslaCrypt.lnk
%AllUsersProfile%\Start Menu\Programs\TeslaCrypt.lnk
HKEY_CLASSES_ROOT\CLSID\[random numbers]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\”Shell” = “[SET OF RANDOM CHARACTERS].exe”
TeslaCrypt has been popularly recognized as one form of dangerous ransom virus that is designed by cyber criminals for illegal purpose. This newly released ransom virus mainly attacks Windows compatible PCs, especially those exist in the surrounding of vivid system vulnerabilities. By making use of a variety of dishonest ways, TeslaCrypt ransomware can always sneak into a user’s computer without any permission. Once being installed, TeslaCrypt infection will utilize advanced codes and created registry files to disrupt the machine that it affects. Typically, the user’s personal files would be encrypted by the leading Advanced Encryption Standard (AES) technology. To get the files decrypted and system released, TeslaCrypt ransomware would demand users to pay a sum of money in bitcoins or PayPal My Cash Cards. It is certain that TeslaCrypt must be removed timely in order to keep the safety of affected machine as well as privacy.
Note: Manual removal is a high level task, no single mistake is allowed. If you are not familiar with the operation and do not want to make mistake, you are welcome to ask help from VilmaTech Certified 24/7 online expert here for further solution.