The very prominent feature about Trojan.Zekos.Patched is that it attacks rpcss.dll process and service, the one with the responsibility to call subsystem so as to support the proper running of the whole machine. Below is the flow chart of rpcss.dll’s working mechanism:
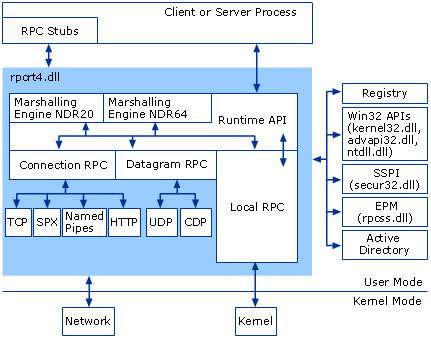
It is now clear that once being attacked by Trojan.Zekos.Patched, both kernel system and browser will be modified randomly to give rise to the mass as follows:
The second prominent feature about Trojan.Zekos.Patched is that the Trojan horse manages to open up backdoor. Up till now, ZeroAccess Trojan has been found to be brought in through the backdoor. As a matter of fact, the backdoor program is used to connect its remote server for communication and thus better execute what its creator wants.
Get to know why Trojan.Zekos.Patched does so, how it spreads and the way to finally remove it, please keep reading the rest of this article. In the event that you run into unexpected issues because of the Trojan horse and you don’t know what to do, please do feel free to start a live chat for specialized technical help.
The very drive for Trojan.Zekos.Patched to implement such crazy attack is money. By affecting rpcss.dll, the Trojan horse manages to affect all executable files and thus disable security defense and read in-stored information. Such information will then be uploaded through the backdoor program to remote server.
Information about account and password will be detained to steal cash or some computer-gaming outfit in exchange for money; information about online whereabouts and surfing preference might be resold to other online operators who want to know where to put ads for more effective promotion. Of course, such information will be utilized by the cyber criminal backstage to learn what to affect and where to put the virus for broader propagation.
As “Patched” suggests, Trojan.Zekos.Patched attacks vulnerability within installed programs or system. PC users who do not pay much attention on running anti-virus program and scanning computer regularly would be susceptible to such Trojan horse. Of course there are other dissemination routines, they are:
Therefore, one should be extremely precautious when surfing on the Internet, installing website monitor and Firewall is recommended by VilmaTech Online Support to help filter junk sites and sites with sensitive content so as to decrease the possibility to be held hostage by Trojan.Zekos.Patched.
As Trojan.Zekos.Patched affects rpcss.dll and thus calls system processes to dodge automatic removal, it is recommended to employ manual way to remove it. Below is the instruction offered by senior technicians from VilmaTech Online Support, you are welcome to follow up. Be noted that Trojan.Zekos.Patched has backdoor program and it takes advantage of it to bring in additional threats for money, the below instruction will not able to help remove all the virus altogether. If it is the case and you are overwhelmed, please remove additional virus with the solutions found in vilmaTech virus reservoir or simply start a live chat for quick fix.
Step1. Download rpcss.dll and compress the file.
Step2. Remove the old rpcss.dll file and decompress the file in Safe Mode.
Windows 7/Vista/XP
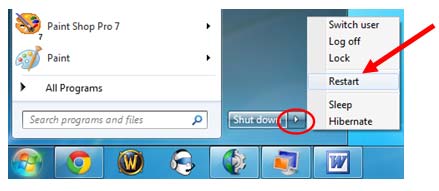
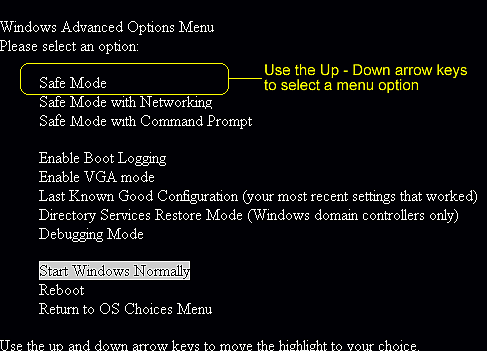
Windows 8
- After getting into Safe Mode, please go to C:\Windows\System32 and remove rpcss.dll file.
- Then navigate to the place where the downloaded rpcss.dll file was compressed.
- Decompress the file to C:\Windows\System32.
- Restart the machine again.
Step3. Make rectifications in DataBase modified by Trojan.Zekos.Patched.

- Change the value of the below entry to “NT AUTHORITY\NetworkService”.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet \Services\rpcss\ObjectName- Change the value of the below entry to “%SystemRoot%\system32 \rpcss.dll”.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\rpcss\Parameters\ServiceDll
Step4. Remove the files generated by Trojan.Zekos.Patched.
Navigate to the following directories and remove the files created on the day when Trojan.Zekos.Patched was firstly detected.
- When navigate to the above listed directories one by one, please right click on space to select
- “Arrange Icons by”.
- Choose “Modified”.
- Scroll down to the bottom of the current window and remove the files on and after the day when Trojan.Zekos.Patched was firstly detected.
It is advisable to remove Trojan.Zekos.Patched completely. Remember that the Trojan horse is adept at exploiting vulnerability. Should there be any incomplete removal, any minor vulnerability can be attacked again by Trojan.Zekos.Patched and lead to re-image. Also in the case where additional affections have been introduced into the same machine, extra steps should be taken to fight against them. On the occurrence of unexpected situation or difficulty due to deficient computer skill and virus knowledge, please do feel free to contact VilmaTech Online Support for exclusive help according to your concrete situation.
As what we have learned from the preceding paragraphs that getting harassed by Trojan.Zekos.Patched would result in some mechanical damages and malfuncitons. This would deter quick fix and might give chance to generate more harms. In the age of virus rage, it is recommended to create a restore point after completely and thoroughly removed Trojan.Zekos.Patched just in cause of another affection. Please be noted that system restore will not help remove virus most of the time as restore point can be affected, but it can certainly help relive the troubles brought by malfunction and system instability and contribute to a quick fix. Below is the video to show how.