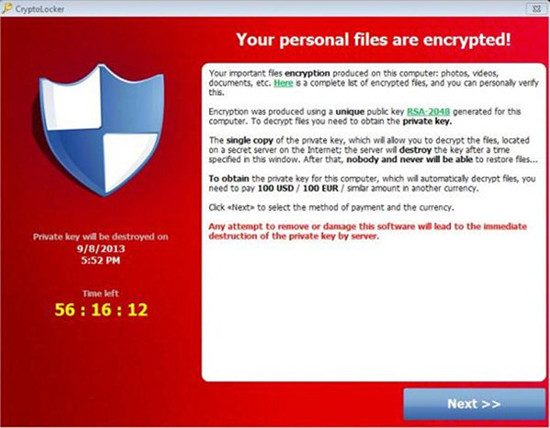
The alert of “Your personal files are encrypted” reflected on the Cryptolocker virus screen is carefully crafted tactic to trick online computer users and blackmail money from them. The true nature of Cryptolocker virus is an aggressive ransomware, work centralizes in distributing fake warning under the disguise of legitimate authentic enforcement agency to threaten target computer and Android phone users they have been violating specific law articles. And Cryptolocker virus and Cryptolocker Android malware encrypt user files and won’t allow for restoring those unless a certain amount of money is paid. “Your personal files are encrypted” Cryptolocker virus generally gives users’ an authentic impression by displaying seemingly sufficient evidence. Now, you may have a view of the “Your personal files are encrypted” Cryptolocker virus Android lock screnshot as following.
Note: Are you frustrated with the “Your personal files are encrypted” Cryptolocker virus removal? To quickly and completely remove such virus, you can Live Chat with VilmaTech Online Experts now.
Cryptolocker virus is classified as the so-called Trojan horse ransomware epidemic across world around September 6 2013, infiltrates on user computer just via the way of masquerading as an email attachment. Once opened, the intrusive virus executable codes then proceed to encrypt all files on the victimized machine. In most cases, the Cryptolocker virus hardly allows being identified until its encryption process accomplishes. In a word, the propagation exploited by such Cryptolocker virus is to take advantage of innocuous email attachment purportedly attributed from legitimate company, just need users once click, it can let itself automatically infiltrates on users’ computers. The principle of such ransomware is ordinary. Usually Cryptolocker virus accomplished achieves its release just by users opening its vividly crafted virus emails.
Cryptolocker virus focuses on striking unsuspecting online computer users especially those unwary computer users are used to straightforward opening emails before acquiring what is going on. Only when the malicious email is opened, the Cryptolocker virus may constantly boosts its payload to get itself installed in the documents and settings folder with a random name first. Later after that, such encrypted ransomware adds a key to the registry, which can be contributable for it running on startup. The payload carrying in the infected computer starts to encrypt files inhabited on all local hard drives and mapped network drives. The main goals mainly encrypted by the “Your personal files are encrypted” Cryptolocker virus refer to those data files with certain extensions, including Microsoft Office, OpenDocument, and other documents, pictures, and AutoCAD files.
In most case, the Cryptolocker virus occurs on user computer with a full screen message states your important files encryption produced on this computer: photos, videos, documents, etc. In addition, the pop-up virus page reads to decrypt files you need obtain the private key. Obviously, the hijackers just utilize the notorious trick to entice target computer users to pay for a fine of $400 USD to over $2,100 USD. If user has paid for the demanding fine in order for restore, the Cryptolocker virus wouldn’t have decrypted personal files, kept the important files even more those workgroup files shared by colleagues, resources on company servers encryption instead. In a word, though you pay for the Cryptolocker virus to unlock or decrypt files, anything within its reach it still encrypts.
See also: http://blog.vilmatech.com/cryptolocker-virus-remove-cryptolocker-ransomware-permanently/
Cryptolocker virus puts up its money demand page, requires the payment in form of (Bitcoins or MoneyPak). The worse thing it not merely blackmail money from virus screen but also underground steals confidential data. Cryptolocker virus can conceal and sneakily corrupt your PC without any trace, and on the face of the victimized computer seemingly runs fine, however it is only a front. The catastrophic failure or dramatic slowdown of an individual computer must happen once the Cryptolocker virus deletes critical system elements. And the problems including disabling the OS, overloading network, and other negatively affect the system’s operability. Under the situation of the Cryptolocker virus constantly operates virus codes to produce some fatal problems on the victimized computers.
Note: To quickly remove the “Your Personal Files Are Encrypted” Cryptolocker virus from the victimized computer, you can live chat with VilmaTech Online Support now.
Want to counter the effect of this Cryptolocker virus? Bring your infected computer to safe mode with networking while you restart Windows or actually hitting F8 key for getting there. Read on the next part.
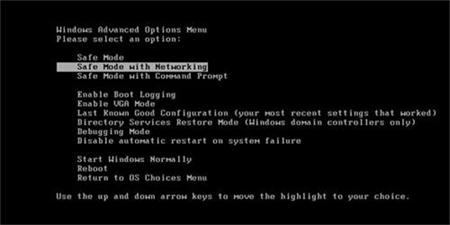
1. Totally shut down the infected computer. Find out F8 key on the keyboard from the infectious computer’s keyboard. If the keyboard doesn’t work, you may plug in an external wired one to have a try again.

2. Press Power button to boot up the infected computer, but before Windows launches (after skipping the first interface), you have to hit F8 key to reveal out Windows Advanced Options.
3. As you can see the page that it says safe mode, safe mode with networking, safe mode with command prompt, etc. Highlight safe mode with networking by pressing Up-Down keys and hit Enter key. Wait for a moment, Windows is loading files to the desktop.
1. Start and login the infected computer until the Cryptolocker virus screen shows on.
2. Press the Ctrl+ Alt+ Del key, it will bring you to the Switch User interface.
3. Tap the “Shift” key on the keyboard by your left hand, click on “Shut down” button. Click on Restart option. In the ‘Choose an Option’ screen, you need select “Troubleshoot.”
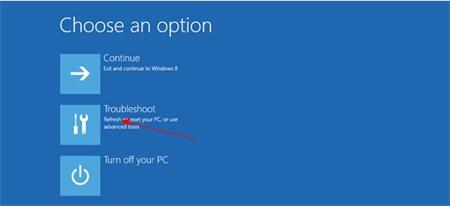
4. Click on ‘Advanced Options’, and in the following window you need choose “Startup setting.”
5. Choose “restart.” Press F5/5 key to highlight Safe Mode with networking option, hit enter key.
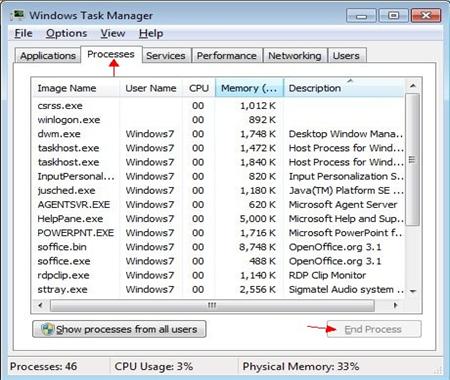
End the Cryptolocker virus process. Press Ctrl+ Esc+ Shift (Windows7/vista) or Ctrl+ Alt+ Del (Windows XP/ Windows 8) to open Windows Task Manager. Scroll down and locate at random Cryptolocker virus file and click on it. You last need click the End Process button.

Delete Cryptolocker virus files from Local disk. But you need show hidden files first.
1. Click on Start button. Click “Control Panel.” And click on Appearance and Personalization.
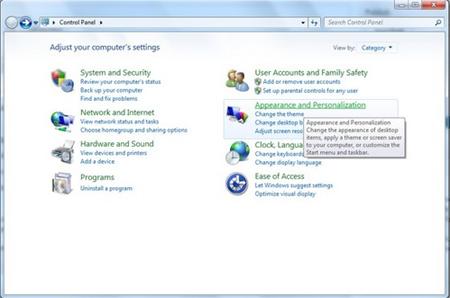
2. Double click on Files and Folder Option.
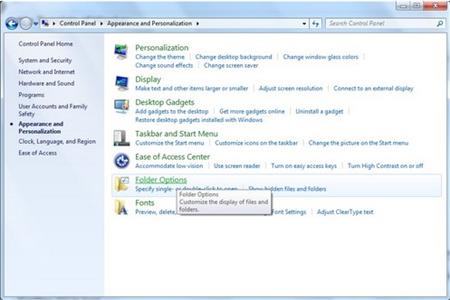
3. Select View tab. Check “Show hidden files, folders and drives.” Uncheck “Hide protected operating system files (Recommended). Then click ok to finish the changes.
4. Open Local disk, and remove Cryptolocker virus files refer to below files. You can click on Start Button and click My Computer or Computer. You then open there.
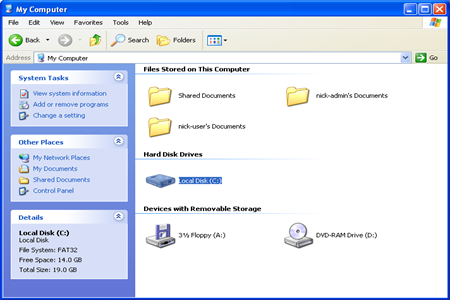
Delete the Cryptolocker virus registry entries.
1. Press Windows+ R key to reveal out Run box. Type regedit in Run window and click Ok.

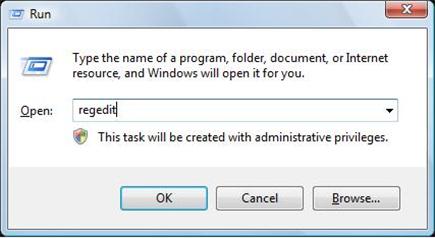
2. In the Registry Editor window, you need navigate to the below path. You then need to find out “Shell” and right click on it. Click on Modify.
3. The default value data is Explorer.exe If you see something else written in this window, remove it and type in Explorer.exe.
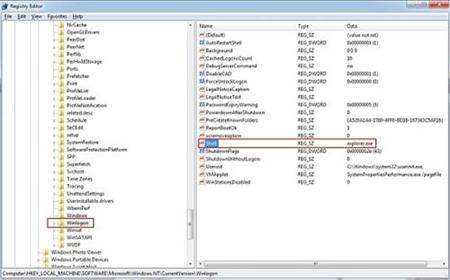
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\
4. Besides that, you still need delete Cryptolocker virus registry entries, you can refer to the below registry entries.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\[random].exe
HKEY_LOCAL_MACHINE\SOFTWARE\ Cryptolocker virus
HKEY_CURRENT_USER \Software\Microsoft\Windows\CurrentVersion\Policies\System ‘DisableRegistryTools’ = 0
HKEY_LOCAL_MACHINE \SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system ‘EnableLUA’ = 0
You need reboot the infectious computer with regular mode to active the virus removal.
Note: Still have troubles with completely removing such aggressive virus files and registry entries? You may Live Chat with VilmaTech 24/7 Online Experts to get further help.
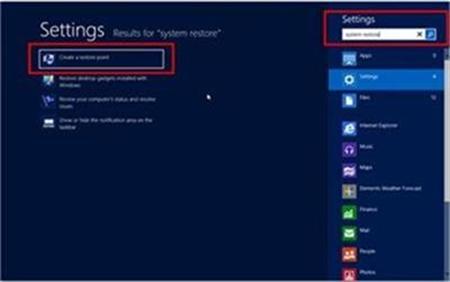
1. To restore from a restore point you will first have to navigate to the Systems Protection tab by typing “System Restore” in the Windows 8 Search bar.
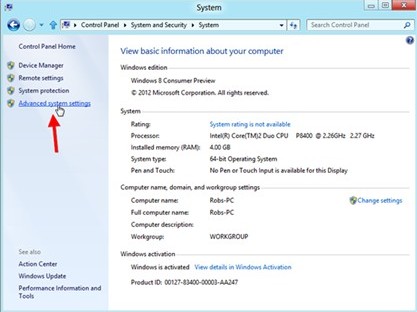
2. Open up the control panel and select “System and Security.”
3. Then select “Advanced System Settings.”
4. In the next window, click on the “System Protection Tab.”
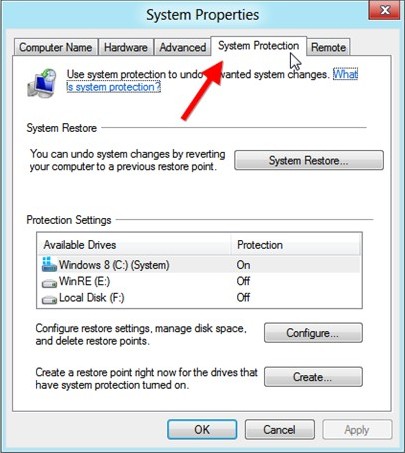
5. In the same window, click on System Restore button.
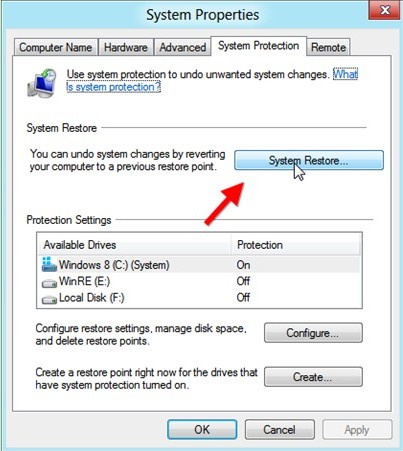
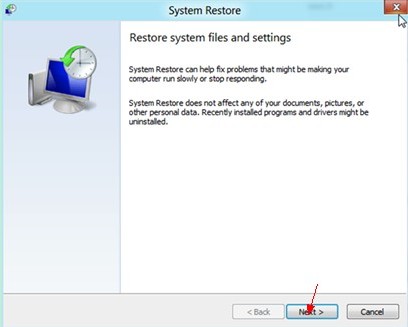
6. Next it will show you System Restore Wizard. Click on “Next” to continue. (But you need backup the existing encrypted file first; rename the file to its original name; right click on it and select Property; click on Previous Versions tab; select one available previous and click on Restore button).
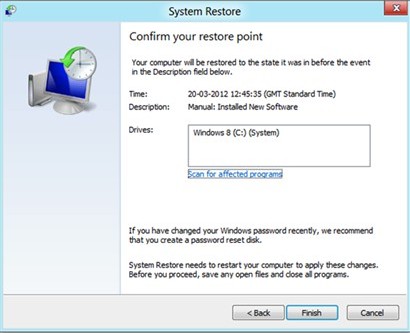
7. In the next window asks that restore point is better to take, click on it and click Next button again. Later after that you’ll find the following window asking you to confirm your choice. Click on Finish button and Windows will automatically complete the restore for you.
The latest ransomware Cryptolocker virus Android malware is proven possible to make the total failure on the victimized machine and collect any reachable confidential data fro illegal commercial benefits. The most common symptom for such pC/Android ransomware is to encrypt users all privacy files using asymmetric encryption, which implies that the decryption process involves a public and private key, therefore, Cryptolocker virus requires victimized computer users pay in order for private key. It is similar the big family of FBI ransmoware, locks user’s computer/Android phone and displays amounts of threatening warnings intended to force the innocent victims into paying a random, and also commonly utilizes the nasty rick indented to be an enforcement agency. The only difference is Cryptolocker virus also produces files encryption. Extra tips: Can’t completely fix the Android lock “Your personal files are encrypted” Cryptolocker virus by yourself? You can live chat with VilmaTech 24/7 Online Experts