
OpenAI live-streamed the Spring Update online, which was held the day before Google’s annual I/O conference, whetting the appetites of media and internet population. So, what has been updated in GPT-4o, and has OpenAI retained its absolute power in the field of large models? Why did netizens exclaim, “You’re still a master” after watching the demo? I have spent a day intensively reading all kinds of media, bloggers, organizations, as well as promotional videos, interpretations, analysis and testing experiences from OpenAI officials, and this article is here to clarify the OpenAI Spring Update, which is called the “Little Spring Festival Gala in the Science and Technology Sector”.
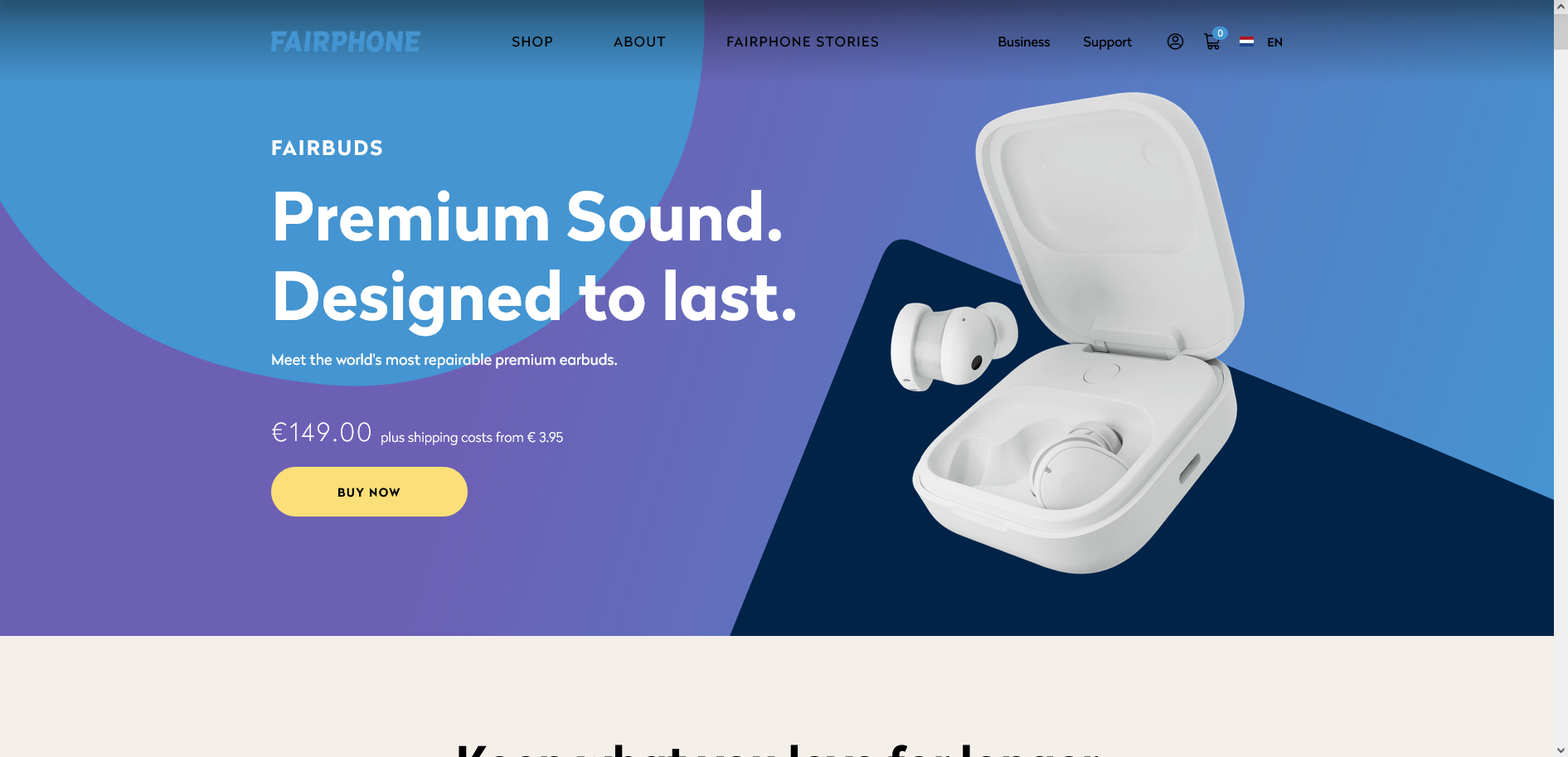
Fairphone Launches ANC Headphones with Replaceable Batteries
The Dutch tech company that launched the Fairphone series of models launched Fairbuds headphones on April 9. Fairbuds supports active noise cancellation, IP54 level dust and water resistance, and like Fairbuds, the company’s earlier cell phone and headset, Fairbuds is as modular as possible in terms of the design of components, with the silicone cover of the headphones, the battery and the charging case, and other components can be manually serviced and replaced by users. The Fairbuds are priced at €149 and are available in black and white.
Windows 11 24H2 Blocks Third-party UI Customization Tools
According to Neowin, Microsoft has intentionally blocked some well-known third-party UI customization tools in the upcoming Windows 11 24H2 release. Currently, the tools known to be affected include StartAllBack and ExplorerPatcher, both of which have the primary function of restoring the old style taskbar and start menu. Running these tools on 24H2 will see a warning that says “This app cannot run because it causes security or performance issues on Windows” and asks users to contact the developer for an updated version. In reality, however, the block is based on the filename, and the exe program can be used as usual by changing its name to something else. Additionally, 24H2 was found to include a feature flag that prevents older versions of the taskbar that remain in Windows 11 from being enabled by default. This could indicate that Microsoft plans to completely remove the old taskbar in future versions of Windows 11.

Why did you fall in love with Ingress? A thousand gamers have a thousand Hamlets in their hearts, but one thing is for sure: this game, which relies on real space and real time, not only promotes mainstream cultural identity, but also shapes a unique community subculture.
I don’t know how many old players still remember this slogan, which used to be the publicity slogan of a hand game called “Ingress”, which was officially released in December 2013, and has gone through ten years by now. For a handheld game, Ingress has already been very long-lived.

If there are some people in the world who will be less interested in folding screen phones, I think a lot of them will be folding screen phone users: heavy body, parameter castration, experience reduction. It’s cool to be able to fold your phone, but the price you have to pay is usually too much to bear. However, this may not include vertical folding phone users, because they are usually less sensitive to performance, and more in pursuit of the ultimate thin and light portable, so you will also find that today’s manufacturers in the roll of vertical folding cell phone products, as if in the creation of a new fashion items, trendy accessories, “cell phone” is reduced to one of the still important function only. But again, this is not my cup of tea at all. In short, the folding screen phone was a big hit when it came out, and I’ve been shaking my head ever since. I was the one shaking my head pretty hard.
But the new vivo X Fold3 series was like a shot in the arm that went straight to my head. Instead of the usual cover-ups, ramblings and careful euphemisms that I had heard when I first learned about it, my friends at vivo read out loud and clear what it was all about – thin, light and as light as the iPhone 15 Pro Max, with the same weight as the iPhone 15 Pro Max, and the same amount of weight as the iPhone 15 Pro Max. Pro Max weight, 8Gen3, image is not weak straight plate, Apple eco-friendly.
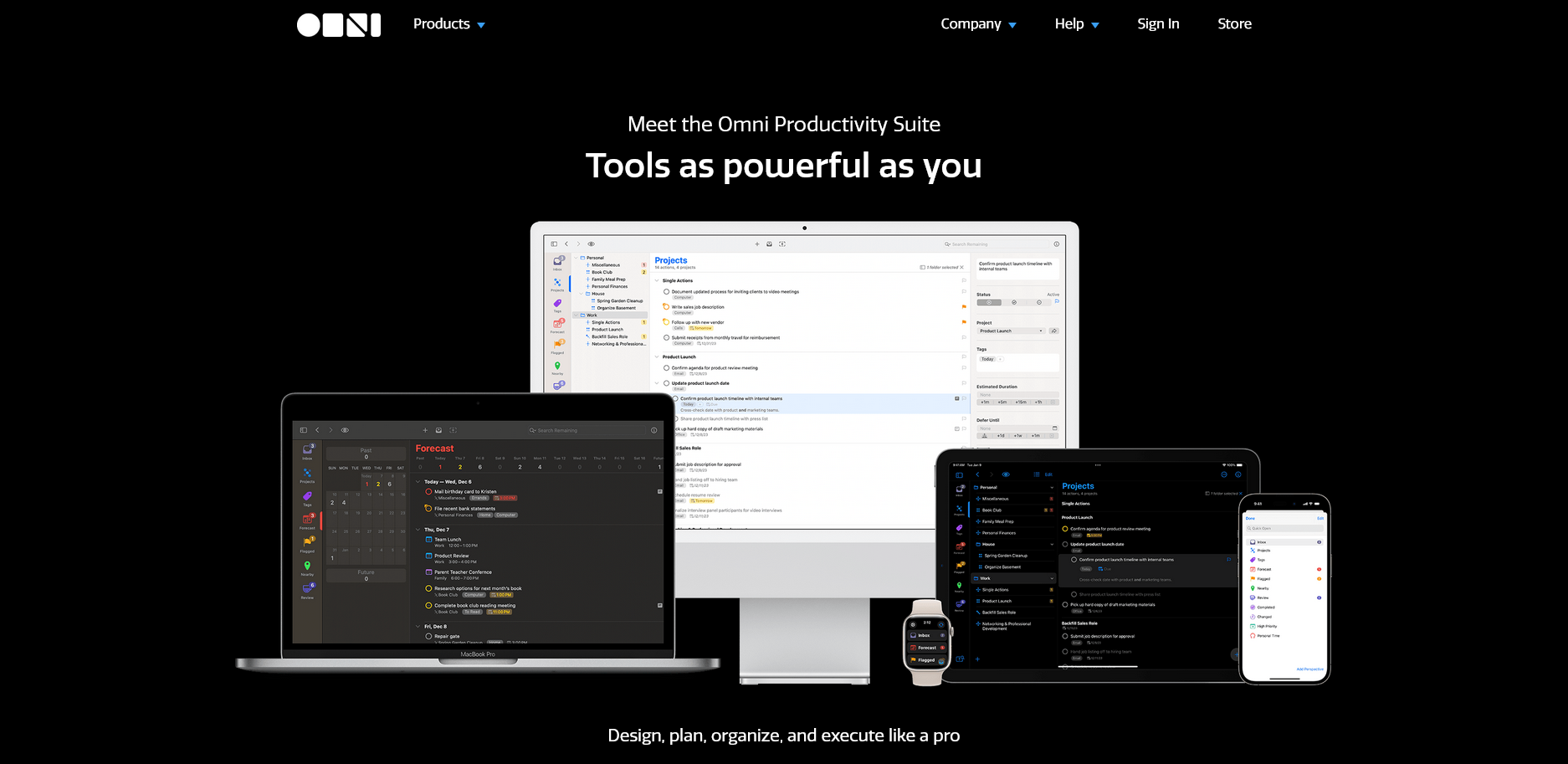
It’s been a long time coming! OmniFocus, GTD’s ace app that has been continuously updated and maintained for more than 10 years, has finally received the OmniFocus 4 update. In this update, OmniFocus 4 focuses on refactoring the app with the new technology SwiftUI, and focuses on the mobile experience by updating its UI design on iOS and iPadOS, which gives the whole app a new look and aligns the UI experience of the clients on all platforms. At the same time, OmniFocus 4 has also been rewritten with SwiftUI to bring some of the features that were once exclusive to the Mac to the mobile version for the first time.
StrongVPN is a leading company designed with an aim to protect everything in your digital life – from your data, to your identity, to your Smart Home. It not only offers fastest seamless streaming, but also protects your devices and private data with end-to-end encryption and state-of-the-art VPN protocol WireGuard. This VPN allows you to surf the web anonymously and bypass web restriction from wherever you are. It can protect up to six devices simultaneously on all major operating systems. Check out the StrongVPN Review 2024 and learn how it works to make you get total freedom online.
Proton VPN is a high-rating and reliable VPN service. over 1 million users are using this Proton VPN. Proton VPN provide 30-day money-back guarantee. Almost users are satisfied with Proton VPN service. Proton VPN practices strict no-logs policy. They never log users’ internet traffic and other personal information. Proton VPN builds huge network with 5,127 VPN servers in 91 locations. It provides fast and stable speed, and you can access any websites from anywhere and anytime. Proton VPN uses the military grade encryption called AES-256 bit and multiple advanced features to ensure online privacy and security for customers. Your sensitive data like payment types, bank account, ID number, logins and passwords will be protected by this AES-256 encryption. This encryption method is unbreakable encryption which can’t be decrypted by anyone. Proton VPN applies multiple VPN protocols including OpenVPN, PPTP, L2TP, SSTP and IPSec/IKEv2 to offer highly security for users to surf online randomly.
Have problem is selecting a proper VPN service? Let us help you find what you need. VPN has become a common product especially after the Congress allowed ISPs to sell users’ browsing histories to the third parties without users’ permission. More and more users purchased VPN to reclaim their privacy. Selecting the right VPN is very important. The most important aspects are that the VPN has servers in the locations you need, supports the protocols you want, and has a client if you need to use one. Unlocator is one of such good VPN services. We made every effort to ensure that this review was accurate and fair. Get more information in this Unlocator review.
Good news! For a limited time, StrongVPN is offering the biggest discount of the new year. For StrongVPN users, you can get an extra year for FREE when you purchase the yearly plan. Normally the cost for a monthly plan is $11.99/month. But now you can get it at just $3.97/month and you will get the overall protection for 12 months! This is a super saver offer and highly economical. Save 66% off of your StrongVPN subscription by using our exclusive discount. StrongVPN is an US-based VPN service that offers blazing fast speeds, 10 simultaneous connections, unlimited data and bandwidth, Smart DNS, and a 30-day full-refund policy. It is the most secure and reliable VPN solution you’ve been waiting for. Get globe internet privacy internet from StrongVPN from now on!