Win32/Zbot.gen!AP stems from Win32/Zbot.gen family that can be traced back to early 2009. It is the most notorious among the newly published versions as it sticks to a target machine as if there’s no way to remove it. Anti-virus programs simply work to only flag Win32/Zbot.gen!AP without solution and have to allow svchost.exe to pop up, CPU to be consumed significantly, redirect issues to happen.
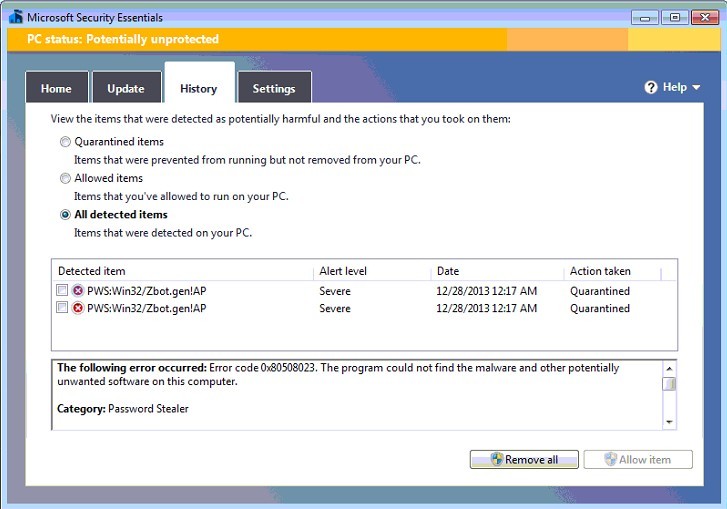
Given this, Global PC Support Center has tested Win32/Zbot.gen!AP for multiple times on the platform of WinXP SP3 to bring about a list of its vicious conducts hereby to come to your knowledge:
If one navigate to “Generic Host Process for Win32 Services [svchost.exe]”, one will find an obvious fact that something is monitoring activities and a weird terminal is connected without knowledge.
The above provided analysis has make it perfectly clear that getting infected with Win32/Zbot.gen!AP will lead to lower Internet browser security, disabled the computer’s firewall, information lost, unauthorized access and direct control of an affected computer. To safeguard your computer as well as information, it is wise to remove Win32/Zbot.gen!AP. Due to high elusiveness, removing Win32/Zbot.gen!AP needs computer knowledge to carry out manual removal. If you don’t know how to proceed the below offered instruction, get one-to-one assistance from specialized expert at VilmaTech Online Support.
One – End running processes related to Win32/Zbot.gen!AP or have been injected with .dll.
Windows 8
Windows7/vista/XP

Steps:
Two – Remove desktop.ini files generated by Win32/Zbot.gen!AP to make sure that it won’t flood all its components back on the occurrence of incomplete removal.
ⅰSince desktop.ini file is hidden, we should unveil hidden items first.
Steps:
Windows 8
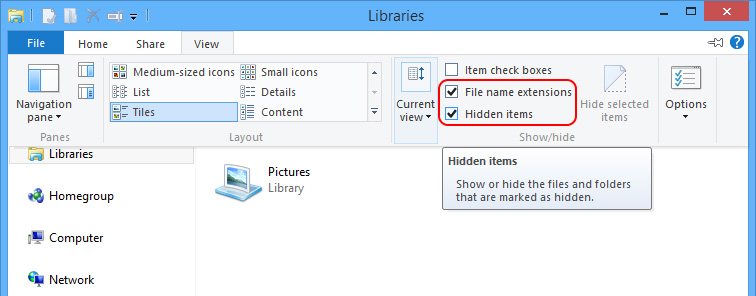
Windows 7/XP/Vista
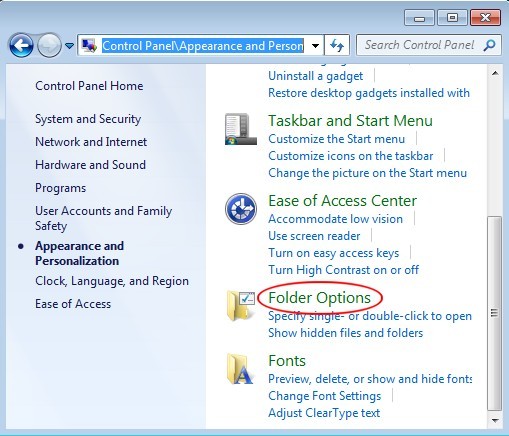
(Tip: remove the following files by the way.)
- Temp files under C:\Windows\System32
- All files and folders under C:\WINDOWS\SoftwareDistribution.
- D:\autorun.inf
- C:\Program Files\Internet Explorer\iexplore.com
- C:\Program Files\Common Files\iexplore.com
- C:\WINDOWS\1.com
- C:\WINDOWS\iexplore.com
- C:\WINDOWS\finder.com
- C:\WINDOWS\Debug\[name] Programme.exe
- C:\Windows\system32\command.com (the one that is created on the date Win32/Zbot.gen!AP emerged)
ⅱRun anti-virus programs to find out the directory Win32/Zbot.gen!AP locates.
ⅲ Use cmd line to help remove all the desktop.ini file shown in the place where Win32/Zbot.gen!AP locates.
Steps:

(Tip: one should empty out Dustbin including desktop.ini file there.)
Three – Access Registry Editor to Remove the following given keys and values.
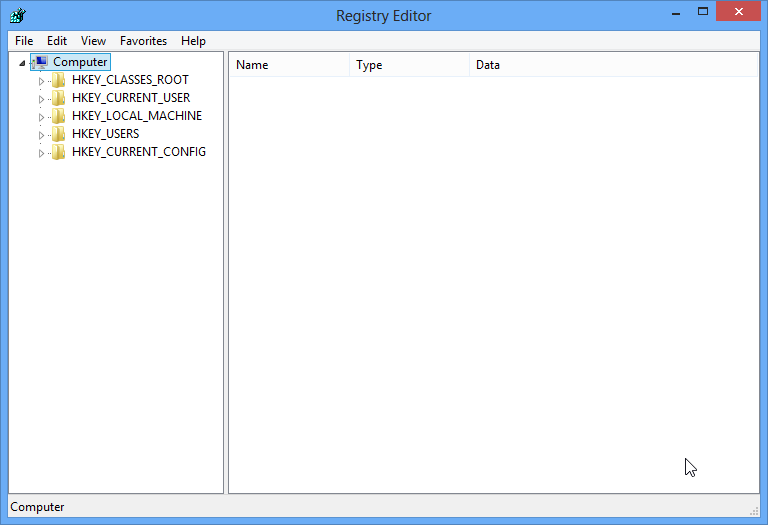
HKEY_CLASSES_ROOT\CLSID\{51716C09-6B08-4CCF-B526-718E912C0573}
HKEY_CLASSES_ROOT\CLSID\{51716C09-6B08-4CCF-B526-718E912C0573}\InprocServer32
HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\CLSID\{51716C09-6B08-4CCF-B526-718E912C0573}
HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\CLSID\{51716C09-6B08-4CCF-B526-718E912C0573}\InprocServer32
HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ EXPLORER\SHELLEXECUTEHOOKS{51716C09-6B08-4CCF-B526-718E912C0573}
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run{random file name} = “%Application Data%\{random folder name}\{random file name}.exe”
Final
PWS:Win32/Zbot.gen family is generated by Zeus kit, the one is crazily peddled on network black market. Therefore it is tough to eliminate its supply. What we need to before the successful elimination is to enhance overall security and use high vigilance when surfing online. Most PC users won’t pay much attention to Win32/Zbot.gen!AP since it doesn’t cause many more troubles. However, Win32/Zbot.gen!AP targets password and it affects system memory to trigger tangled problems that cannot be repaired completely, which plants the seeds for additional affection. Since some vicious components are so confusing that anti-virus programs are not able to remove Win32/Zbot.gen!AP completely, it is recommended to adopt manual method. On the occurrence of difficulties, you are welcome to use online PC security service from VilmaTech Online Support for exclusive solution to your concrete situation. Be noted that any ignorance of a piece of vicious item will lead to failure.