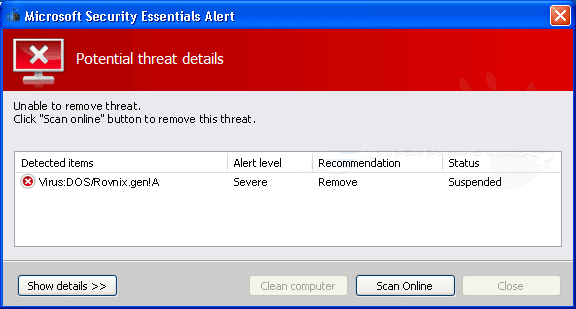
DOS/Rovnix.gen!A is categorized as Trojan horse. It possesses some basic features of a Trojan horse; but being a member of Rovnix family, the Trojan is capable of affecting volume boot record so as to load unsigned kernel-mode drivers on a target machine. Since boot record does not belong to any disk, DOS/Rovnix.gen!A manages to stay on a machine without being removed even when the victims try disk format.
When its settlement is fixed, the Trojan horse would then have a chance to write its own data to the end of a physical drive in an attempt to execute its copies in pivotal sections, such as startup and security service. With the modified driver, DOS/Rovnix.gen!A will be able to add self-made values and keys into Database. By doing so, the random modifications will not be rectified back easily and automatically by the system.
The last but not least, the files generated by DOS/Rovnix.gen!A have the System (S) and Hidden (H) attributes present in attempt to hide the file in Windows Explorer; as soon as the entire installation is finished, the DOS Trojan would delete its original executable file. With the two methods combined, DOS/Rovnix.gen!A manages to control the machine to the greatest extent without being caught and removed.
The situation allows of no delay. Below is the manual instruction offered by experts. Should you have difficulties in understanding the steps or carrying out the instruction, please do feel free to contact VilmaTech Online Support and get exclusive help according to your concrete situation.
A
Change the partitions.
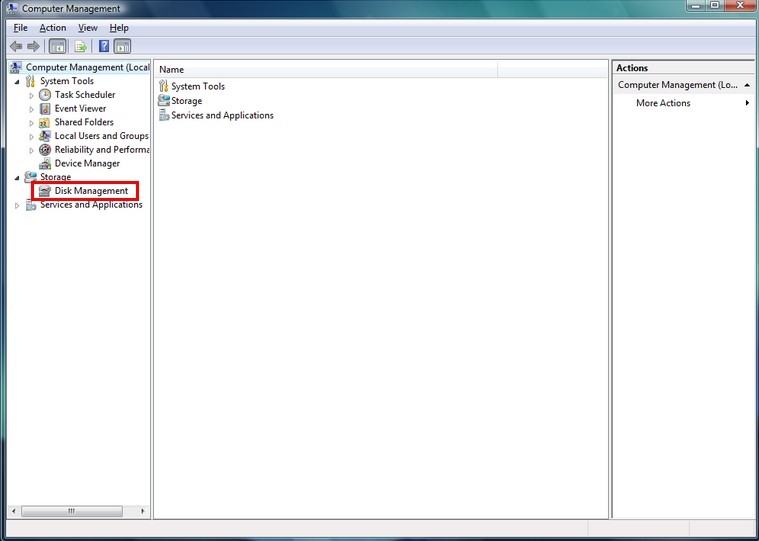
B
Implement hard disk low level format to remove Virus:DOS/Rovnix.A.
C.
remove the items generated by Virus:DOS/Rovnix.A when the Trojan was firstly found.
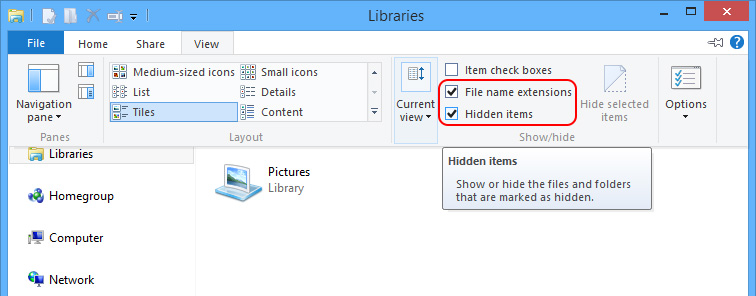
Before navigating to the below listed directories to remove Virus:DOS/Rovnix.A, one should unveil all the hidden files. Steps are as follows.
Windows 7/XP/Vista
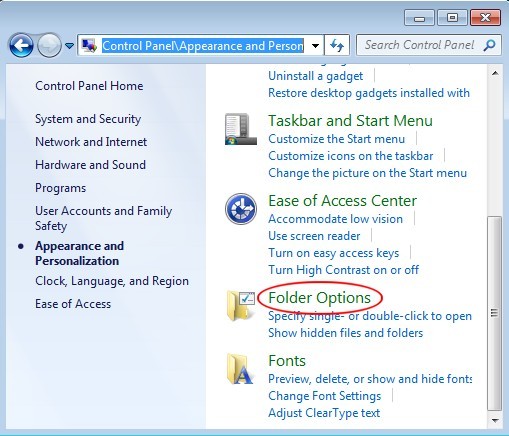
Windows 8
%Program Files%\Common Files\
C:\Windows
C:\Windows\System32
C:\Users\[your username]\Documents\
C:\users\user\appdata\local\
C:\Program Files\To remove the items generated on the day when Virus:DOS/Rovnix.A attacked the machine, please:
- Right click on the space of the window that’s under inspection.
- Hover mouse over “Arrange by” to select “Day”.
- Scroll down to the bottom of the window to remove the related items.
It is highly recommended to create a restore point after removing Virus:DOS/Rovnix.A. Though the restore point will not help removing virus all the time; it at least would eliminate many more mechanical issues that could hinder quick removal which is required to stop further harms. Here’s the video to show how to create a restore point.
Damaging computer is not what DOS/Rovnix.gen!A aims at. As a matter of fact, Virus:DOS/Rovnix.A provides a botnet for rent, which is the major way that Virus:DOS/Rovnix.A earns money (the ultimate goal). There are other ways to help its maker to get additional income: