The VirLock term comes down to one type of ransomware that is distributed by Internet fraudsters for illicit subjects, typically money extortion. The main vulnerable groups of the VirLock ransom virus refer to individuals using multiple platforms such as Windows operating system, Mac OS as well as Android phone system. In computers, the typical exploits VirLock ransomware implement directly give rise to allow malware distributors to block a user’s private files for data kidnapping while restricting normal access to targeted operating system. VirLock ransomware usually appears to a user in the modality of a concoctive pop-up Window, allegedly claiming that “Your computer was automatically blocked” due to certain pirated software that has been found on the machine. The obstruction and restriction seem to be temporarily with a sum of fine, generally getting up to $230 – $250 USD. Apart from traditional modes of payment, the anonymous system supported by VirLock ransomware is also compatible for BitCoins so that to acquire benefits through a more comprehensive platform.
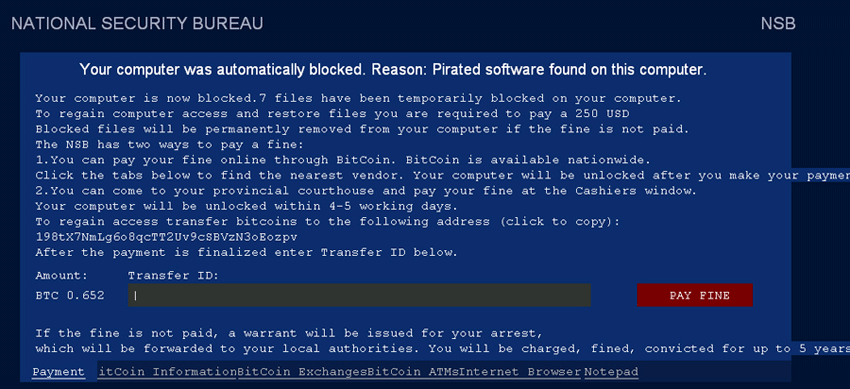
To increase its illusion, VirLock ransomware embezzles a legitimate, authoritative name from the United States law enforcement – National Security Bureau. In accordance with the alert, victims are also informed of a further survey or even arrest will be carried out without demanded forfeit. The extreme purpose of warning from VirLock ransomware is to mislead users into believing that they are in big trouble unless paying fine on time. There is no doubt that VirLock ransomware has nothing to do with any law enforcement agency and is only one type of malware that is adept at leveraging the victim’s surprise, fear to intimidate them into paying ransom demanded. Users must never pay money for VirLock ransomware and should terminate the infection from compromised machine at any cost. Otherwise, VirLock ransomware may keep blocking user’s sensitive files on targeted operating system, hampering them to access machine regularly. For worse results, VirLock Ransomware may start connecting to distant controller, allowing hackers to take control of affected machine without any authorization.
Attention: Manual interaction is known as the best way to get rid of VirLock Ransomware, as the virus may block all antimalware tools from running for self-protection. If you are not familiar with manual operation and do not want to make worse result. Please be free to contact VilmaTech Certified 24/7 online expert here who will be glad to help you out of trouble.
Similar as another latest released invasive KEYHolder Ransomware, VirLock ransom virus can always sneak into a user’s computer, Android phone through a wide array of dishonest ways. For instant, VirLock ransomware may arrive as part of another malware’s payload, some examples of which are multi-component Trojan infection, Rootkit virus, fake antivirus program and more. As a state of the art ransom infection, VirLock virus is skilled in making use of exploit kits which could explore the vulnerabilities on the affected machine in order to stealthily drop and execute the malware. For some common methods, KEYHolder Ransomware may be distributed by some web sites that have been attacked and controlled by cyber criminals. In addition, no matter which version of computer OS or Android system that is adopted, users should never download any distrusted application through networks or opening spam email carrying infected code of KEYHolder Ransomware.
1. Safe Mode with Networking
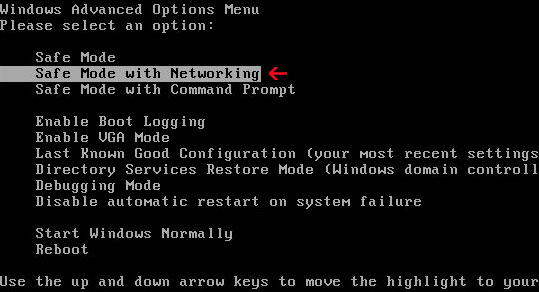
VirLock Ransomware has blocked your PC from running in regular mode. So you are required to log in the Safe Mode with Networking for better operation. Here is the guide:
a. Restart infected machine.
b. Before Windows logo appears, press F8 key on the keyboard.
c. In the pop up Windows Advanced Options Menu, use the arrow key to highlight Safe Mode with Networking.
d. Enter to log in the mode.
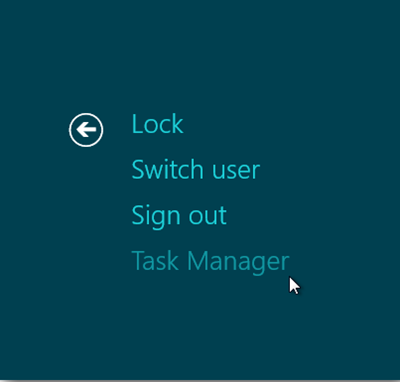
a. Start up infected Win 8 PC. Press Ctrl+ Alt+ Del combination key to show Task Manager window.
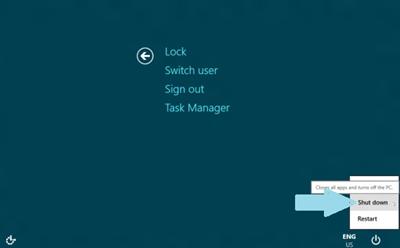
b. Hold “Shift” key while clicking on “Shutting down” button.
c. It’s time to click on Restart option.
d. Navigate to “Choose an Option” window; in the list of options, select “Troubleshoot”.
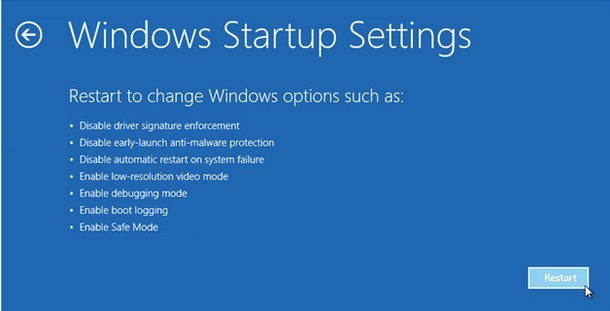
e. Follow the steps: “Advanced Options” and then “Windows Startup Settings”.
f. In the “Windows Startup Settings”, click on “Restart” button. Now your PC will be rebooted into Safe Mode with Networking automatically.
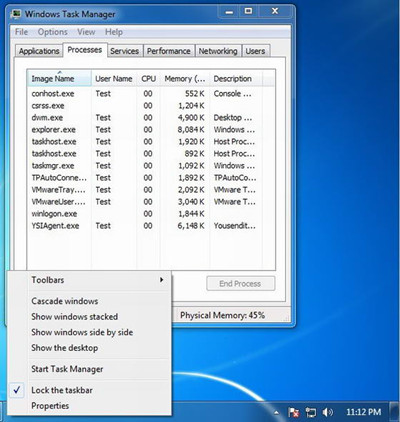
2.Open task manager to stop the running progress of VirLock Ransomware.
3. Click on the “Start” menu on the monitor. Go to “Search programs and files” box; and remove all files relative to VirLock Ransomware.
%AllUsersProfile%\random.exe
%Temp%\random.exe
%AllUsersProfile%\Application Data\.dll HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Random “.exe”
4. Open Registry Editor to clean up all its registry entries.
To do so, you need to open “Start” Menu again, type the command of “Regedit” into search box and Enter. Now the Registry Editor will be seen; and you can right click to remove all registry entries relative to VirLock Ransomware.
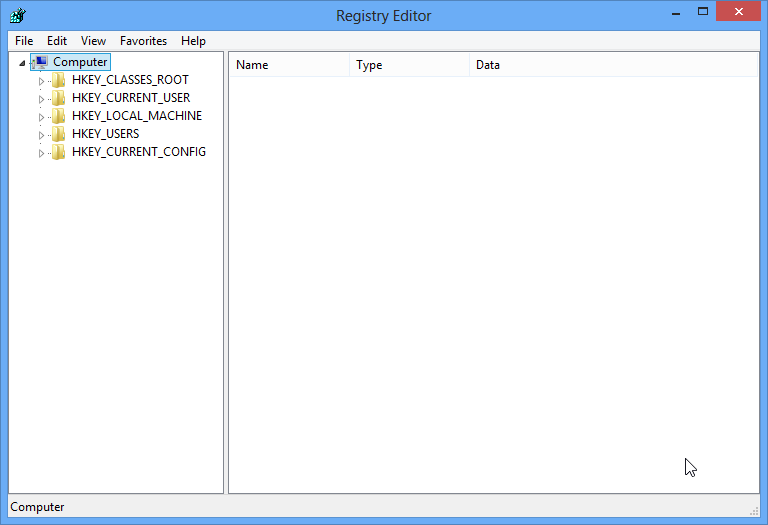
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
KEYHolder Ransomware has been recognized as one hazardous infection for computer users as well as Android users. It can always sneak into a user’s machine through a variety of invasive methods. The process is usually beyond any permission or knowledge. Once being installed and executed, KEYHolder Ransomware will generally block affected machine and certain files for the purpose of demanding users to pay a sum of money in order for the restriction to be removed. To increase its authenticity, KEYHolder Ransomware also misappropriates the name of National Security Bureau, one authoritative department in nation. One must fact that the main purpose of KEYHolder Ransomware is to disrupt affected machine for illegal money extortion as well as other damaging activities. It has nothing to do with the legal organization, but is only a fraud tool operated by cyber criminals. As a result, users should take action as long as being abnormal symptoms of KEYHolder Ransomware are noticed.
Note: Manual removal of KEYHolder Ransomware requires certain expertise. No single mistake is allowed. If you cannot deal with the operation alone, you’d better ask help from VilmaTech Certified 24/7 online expert here for real-time support.