Category: Trojan Horse
OS attacked: Microsoft Windows
Alias:
Trojan-Dropper.Win32.Pihar.uu
Mal/Rorpian-D
Trojan:Win32/Alureon.FK
Trojan.Win32.Alureon
Symptoms:
Several ways are available for Backdoor.Pihar virus to get onto a computer without authorization or knowledge:
It is believed that many victims have encountered the same situation where installed anti-virus programs detect Backdoor.Pihar without the ability to remove it. You’ll know the reason when finish the entire article and the manual removal method is trawled through according to the infiltration way that Backdoor.Pihar virus applies. Any question or emergency will be solved if you resort Global PC Support Center and get its experienced technicians for help.
When Backdoor.Pihar virus finally lands on a target machine, drivers are numerated to be affected so that the subsequent file modifications can be undertaken smoothly. Temp files (directory: C:\Documents and Settings\[UserName]\Local Settings\Temp\)are the next target of Backdoor.Pihar virus. To re-write the temp file with “0x6D07CF72201234A07AB57FB3FC00B9E5A0B3678E” or the like, Backdoor.Pihar virus is enabled to further intercept the service supported by system processes and generate additional executable or .dll files in the target machine.
In most cases, svchost.exe is caught in sight when Backdoor.Pihar virus is affecting a computer. As a consequence, Backdoor.Pihar virus is enabled to stay on a target machine for a loner period of time for more possible information collected by JavaScript technique or tracking cookies. By doing so, Backdoor.Pihar virus manages to get additional money by reselling the collected information to other spammers or achieve broader infiltration to attack the most-visited web sites.
Due to the activities described in the preceding paragraphs, backdoor can be formed thereafter to jeopardize the entire mechanism and security. The backdoor can be easily exploited by infections. Thus the below mass can be anticipated:
It is an emergency to remove Backdoor.Pihar virus. However, the scenario is that Backdoor.Pihar virus reappears right after each reboot. That’s because desktop.ini and other legit system items have been made as its affiliate. Therefore, to remove Backdoor.Pihar virus manually needs high level of computer technology; otherwise, deficient technology will lead to omission and failure due to the inability to recognize vicious items. Follow the below instruction to remove Backdoor.Pihar virus yourself only when computer skills are available; otherwise, use recommended online PC security service and get one-to-one assistance for a quick removal.
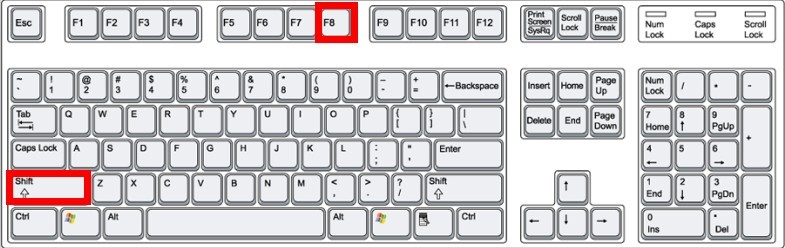
One – Enter into Safe Mode where some vicious executable files will not be activated, making a smoother removal.
Windows 7/Vista/XP
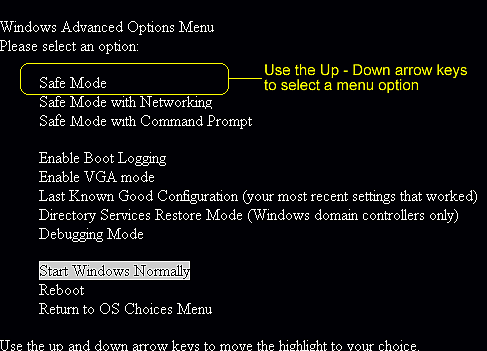
Windows 8
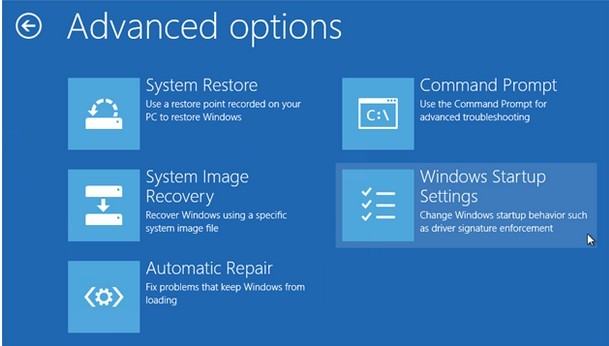
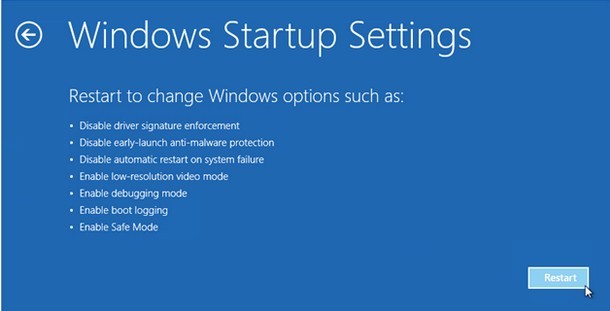
Two – Access Database to modify values and remove some generated vicious items by Backdoor.Pihar virus.

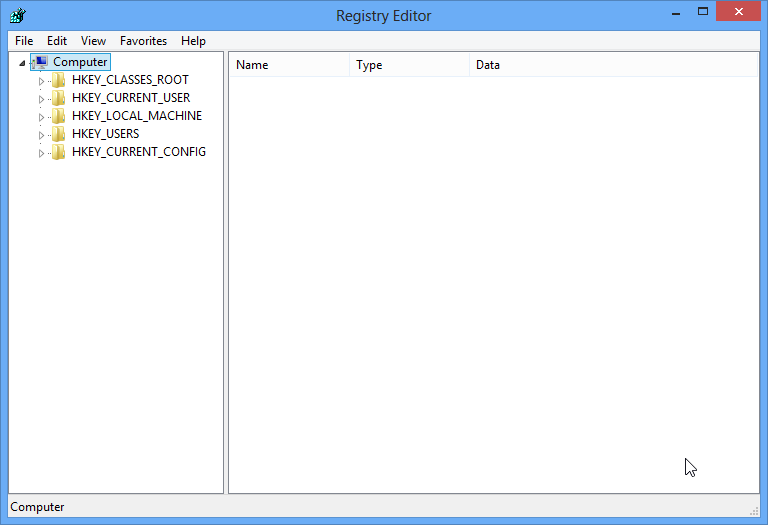
HKEY_CLASSES_ROOTWindowFiles\Check_Associations
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_[RANDOM HEXADECIMAL DIGITS]
HKEY_LOCAL_MACHINESOFTWAREClientsStartMenuInternetINTEXPLORE.pif\ToP
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun\[random numbers and letters]
HKEY_CLASSES_ROOTCLSID{random numbers} shellOpenHomePageCommand.
HKEY_CURRENT_USERSoftwareVB\Check_Associations
Three – Unveil all hidden items and remove vicious items related to Backdoor.Pihar virus with extra prudence.
Windows 8
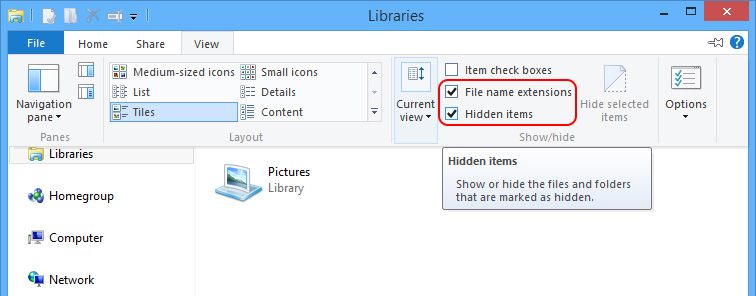
Windows 7/XP/Vista
1. When all hidden items are unveiled to surface, navigate to the following listed directories to find and delete every files and folders named after Backdoor.Pihar virus.
- C:\windows\winstart.bat
- C:\windows\wininit.ini
- C:\windows\Autoexec.bat
2. Next, browse to c:\windows\System32 and remove any item created on the day Backdoor.Pihar virus was detected including services.exe, svchost.exe and the like.
3. Remove all temp folders under System32.
4. Scan for Backdoor.Pihar virus with anti-virus program to locate the place it exists and use command line afterward to help remove all the desktop.ini file there in an attempt to prevent Backdoor.Pihar virus from reclaiming all deleted items back on the occurrence of incomplete removal or accident running of executable files.
5. Remove all the below listed files finally:
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\[RANDOM HEXADECIMAL DIGITS].tmp
- %Windir%\Temp\[RANDOM HEXADECIMAL DIGITS].tmp
Three –Enter into System Service and exterminate as well as other associated services.
Windows 8
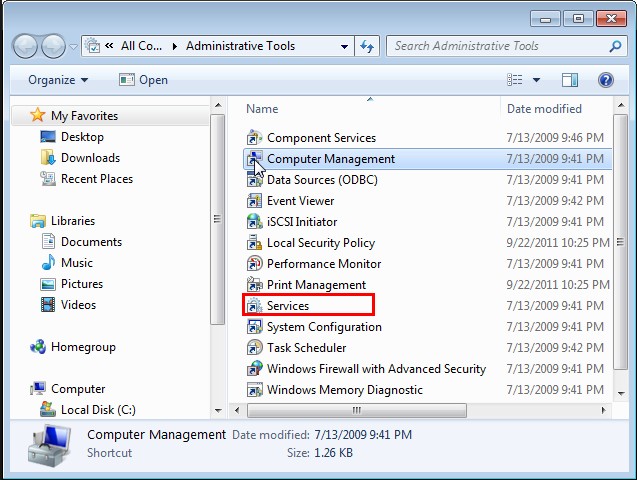
Windows7/vista/XP
Hold Win key and R key at once to type “services.msc”; hit Enter key to remove/disable the following listed services, if any.
- bing-redirect.com
- hellodolly2.com
- hellokitty2.com
- kordelashop.com
- ns1google.com
- wooody27.com
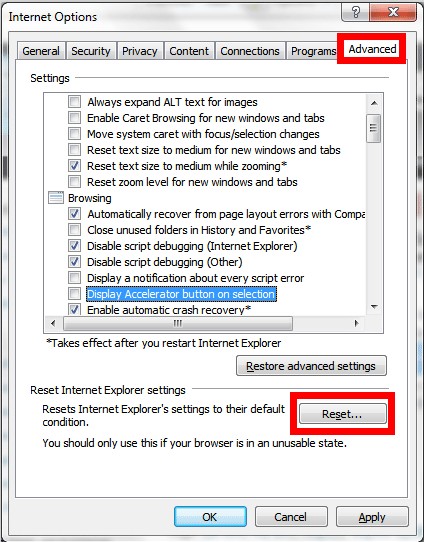
Four – Reset browsers since Backdoor.Pihar virus downloads vicious codes from designated web sites benefit from DNS modification.
Internet Explorer
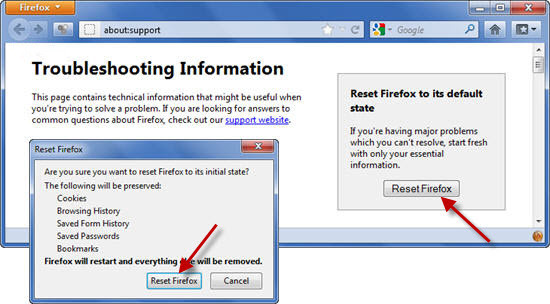
Mozilla Firefox
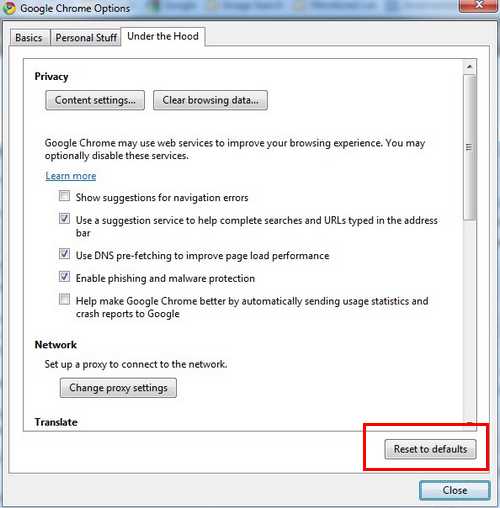
Google Chrome
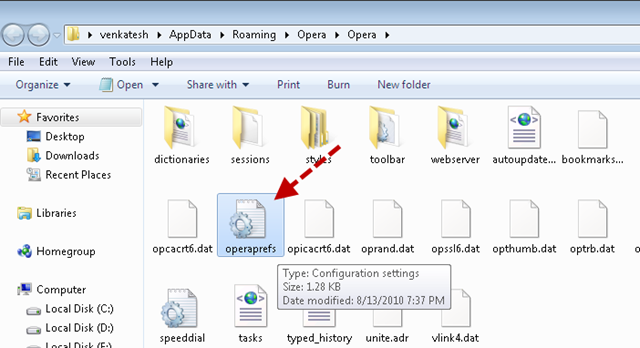
Opera
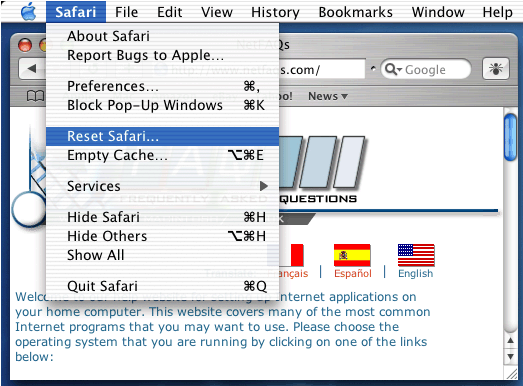
Safari
Five – Run full scan with reputable anti-virus program again, try to remove any possible items.
Notice:
Backdoor.Pihar virus is adept at opening backdoor after a series of malicious deeds, which impose difficulty in a complete removal since any piece of vicious item would help Backdoor.Pihar virus survive the above given instruction. Thus one should apply extra attention during the removal process. VilmaTech Online Support would like to hereby remind victims of the severity remove exterminate system running process or system items mistakenly, the machine would fall into zombie. The above manual removal instruction has been tested for multiple times under the circumstance where no additional infections have been introduced in. Should it be the case and it is overwhelming you, it is recommended to get specialized help for timely solution.