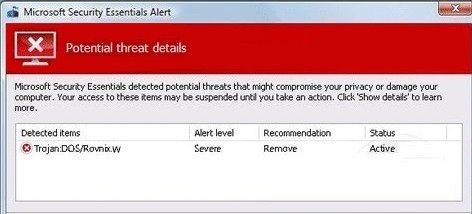
Apart from the above listed troubles, more can be anticipated if Virus:DOS/Rovnix.W sustains its life on a target machine, such as browser redirect problem (note: the virus contains a URL address and uses HTTP protocol in the communication, it hooks Windows APIs to modify network traffic by creating and running a new thread with its own program code within processes concerning browsers).
Virus:DOS/Rovnix.W is actually a Trojan horse and is classified specifically as Rovnix which was the first bookit family to use VBR (Volume Boot Record) infection (NTFS bootstrap code) for loading unsigned kernel-mode drivers on x64 (64 bit) platforms. Now, Virus:DOS/Rovnix.W has been developed to contain both 32-bit and 64-bit program components, which is much more advanced than Win64/Rovnix.gen!C. In other word, Virus:DOS/Rovnix.W targets all Windows platforms.
Unlike the average Trojan horse, DOS/Rovnix.W replaces the original VBR (Volume Boot Record) of the hard disk drive with its own data. That is to say, disk format will not help remove Virus:DOS/Rovnix.W thoroughly as boot record does not belong to any disk.
Besides, there are other evil deeds that enable the DOS/Rovnix Trojan hinder automatic removal. When it is settled, it writes its own data to the end of a physical drive so that Virus:DOS/Rovnix.W manages to place and execute its copies in pivotal sections within a target system, such as startup, security service without too much disturbance; add self-made values and keys into Database to consolidate the malicious modifications. It is worthy of the mention that the files generated by the virus have the System (S) and Hidden (H) attributes present in attempt to hide the file in Windows Explorer, which is the reason why duplicate system running processes are increasing and man-made security programs are confused not to help remove Virus:DOS/Rovnix.W automatically. The root cause of aborted automatic removal is that the virus would delete its original executable file when the entire installation is finished, making it possible to escape even the most powerful automatic removal when it still utilizes the typical vicious way to infiltrate a target machine.
Below is the best solution offered by VilmaTech Online Support. Be noted that computer specialty is required to carry out the steps correctly and completely. On the occurrence of any obstacles that cannot be solved, senior technicians are right here to provide instant and professional assistance.
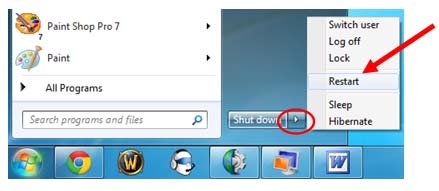
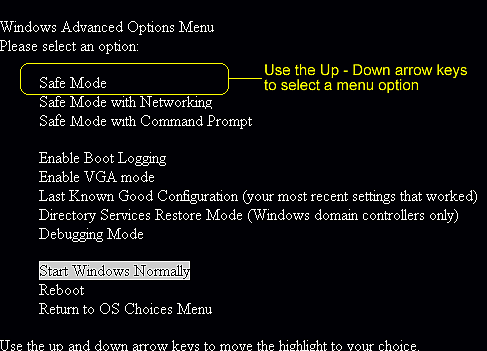
Step1. Access Safe Mode to remove Virus:DOS/Rovnix.W.
Windows 7/Vista/XP
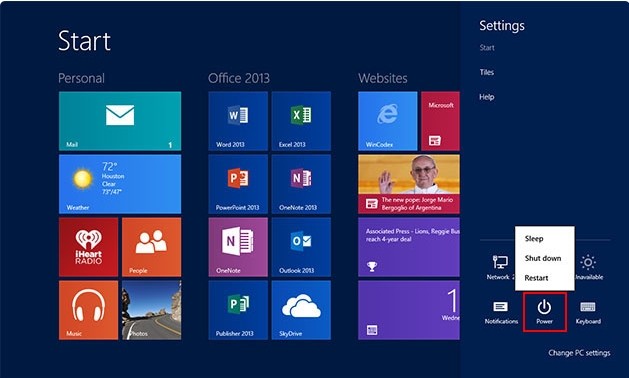
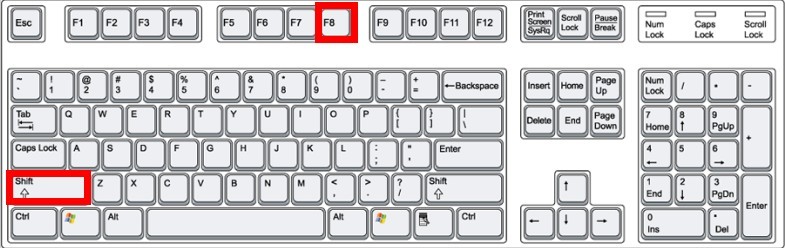
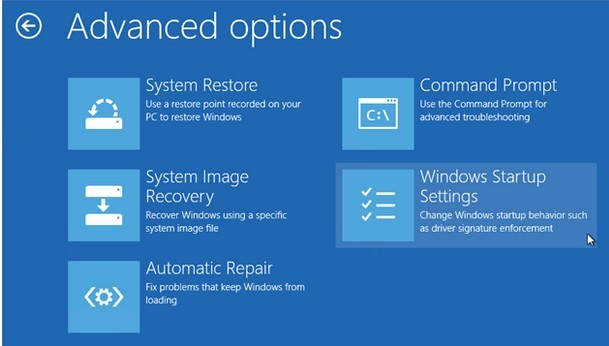
Windows 8
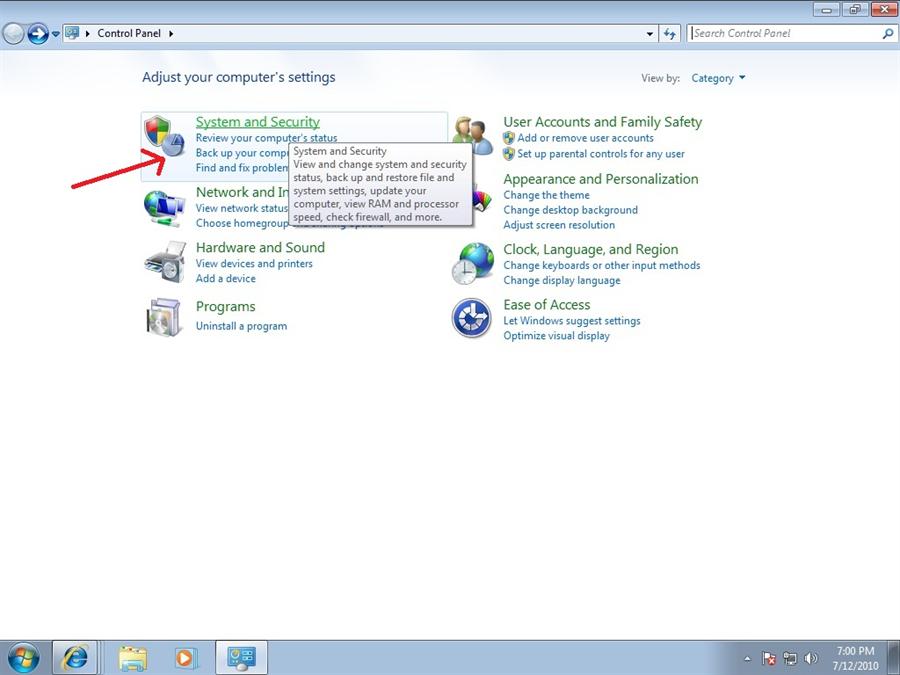
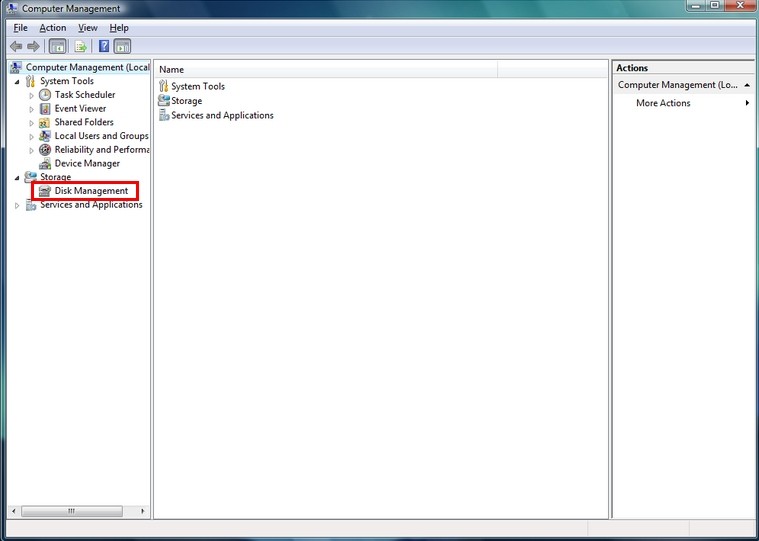
Step2. Change the partitions for Virus:DOS/Rovnix.W removal.
Step3. Implement hard disk low level format to remove Virus:DOS/Rovnix.W.
Tip: low level formatting must be executed with extreme caution. A wrong choice on which storage device to zero would lead to total, absolute, irrecoverable destruction of your critical data.
Virus:DOS/Rovnix.W’s payload is downloading and executing additional modules from the C&C server (rtttt-windows.com C& C domain has been detected). It works in multithreading mode to communicate with the malicious driver; it also sends an encrypted buffer to the malicious driver to be written to hidden storage and injected into processes. Virus:DOS/Rovnix.W can use multiple payloads and can be used to provide a botnet for rent which is how Virus:DOS/Rovnix.W earns money (the ultimate goal).
As described above, Virus:DOS/Rovnix.W attacks DOS and arouse hard drive failures. With drivers being overwritten, software concerned will be weakened not to play fully. Consequently, vulnerability is formed to be readily detected and exploited by any destructive infections concealed in the Internet. This would definitely lead to system security as well as information security. What Virus:DOS/Rovnix.W collects is mainly operating system version, language settings and online whereabouts. When the collection is done, it connects to the URL contained in its iframe field automatically and sends gathered information to its remote machine.
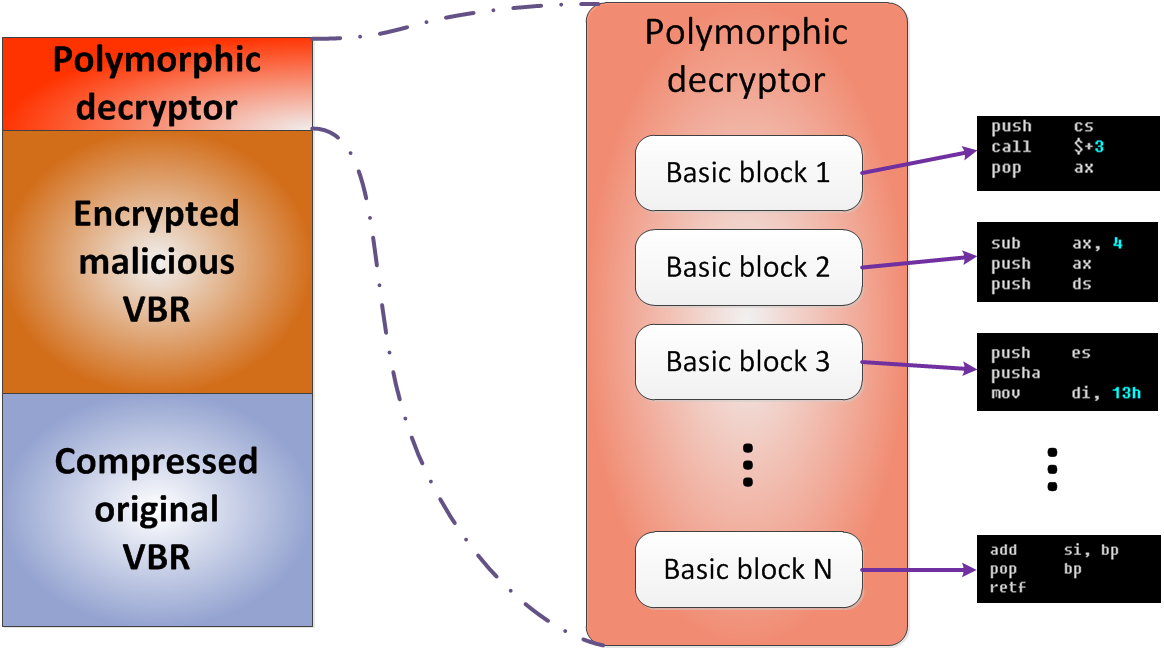
It is extremely hard to remove Virus:DOS/Rovnix.W permanently as the virus owns a great many dissemination routines:
Any carelessness would recruit Virus:DOS/Rovnix.W. What can be done the most is to remove it completely and follow good PC practice thereafter. Let’s make it a point to remove it completely as any remnant would retrieve Virus:DOS/Rovnix.W, occupy limited internal storage, give rise to error messages due to incompatibility or conflict in the future. It should be advised that extra mechanical problem thereby can complex the removal procedure; while the above steps are designed exclusively to Virus:DOS/Rovnix.W. If you are overwhelmed by its problems and know little about DOS, it is recommended to contact VilmaTech Online Support and get specialized technical help right away to tackle down Virus:DOS/Rovnix.W as well as all the incidental issues.