The Metropolitan British Police virus belongs to the category of ransomware that originates from the infamous Trojan Urausy family. Being designed as a typical computer/Android locker virus, the Metropolitan British Police virus always restrict the access to compromised machine and demand ransom form victims. Generally, the Metropolitan British Police virus uses the name of Serios (misspelled “Serious”) Organised Crime Agency (SOCA) which serves as a non-departmental public body of the Government of United Kingdom to strengthen its authenticity. The Metropolitan British Police virus can permeate onto a PC or Android Phone through exploiting system vulnerabilities and drop a malign Reveton or Citadel Trojan to aggressively lock user’s access to Windows as well as Android system.
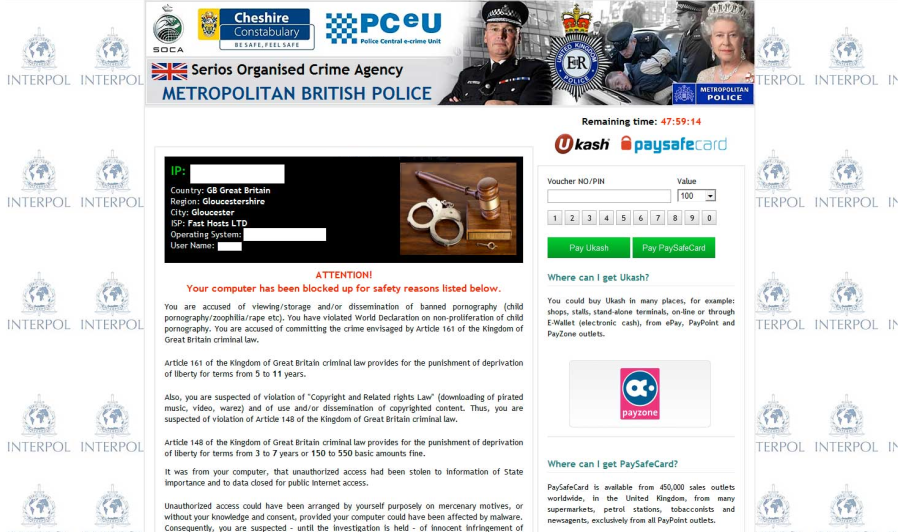
Once the Metropolitan British Police virus infiltrates on a target machine successfully, it will display a bogus notification to puzzle PC users, which states that “Your computer has been blocked up for safety reasons listed below” and PC users are accused of the illegal activity that involved with banned pornography against the Kingdom of Great Britain criminal law. And then, to release blocked PC and avoid worse punishment, victims would be asked to pay a certain fine (£100, £200, £300) through Ukash or PaySafeCard vouchers with 48 hours. However, the Metropolitan British Police virus is similar with other ransomware such as Canadian Association of Chiefs of Police virus (Read more) and infamous Police Central E-Crime Unit Virus (PCeU) ransomware, turning up to be a dangerous malware threat on PC that is independent of the legitimate government organization. Hence, PC users should ignore the misleading alert from Metropolitan British Police virus thoroughly and never pay the non-existent fee for the purpose of getting rid of the locked machine.
Note: The Metropolitan British Police virus manual removal requires computer expertise. If you meet any trouble, please feel free to contact VilmaTech certified professionals 24/7 online here for the further help.
The Metropolitan British Police virus displays the fake lock screen whenever the victims start their affected Windows. It replicates its copies constantly so that to spread and mess up system settings. Basically, the Metropolitan British Police virus will target the Windows boot sector in order to allow its program to run voluntarily. By default, the Metropolitan British Police virus hides its components deeply on system to avoid build-in operating system’s protection such as Firewall. At the same time, the Metropolitan British Police virus would disable the operation of programs on affected PC. In other words, victims are not able to run any applications installed on their PCs normally, including antivirus programs. Moreover, the Metropolitan British Police virus can excavate system bugs in order to allow additional threats (eg. browser hijack virus, Trojans, worms, and rogue virus). The more threats existed on PC may cut off the network, slow down the performance of system significantly, cause a blue screen of death and even computer crash.
Delaying removing the Metropolitan British Police virus, it can open ports of system to permit third party to access compromised machine and take control of it in the end. Hence, it is obligatory to remove the Metropolitan British Police virus timely once being notice of its existence. However, the Metropolitan British Police virus has the capability to disable the function of programs on PC that contain the antimalware tools. There is not any perfect antivirus that can catch all computer infections in the world. New viruses are found daily and although all kinds of security applications have significantly improved the detection of new viruses, technology used by used by virus authors continually changes as they try to avoid detection and even disable the operation of antivirus programs. Victims should figure out other effective approach to remove Metropolitan British Police ransomware permanently.
Note: Certain expert skills will be required during the manual removal procedure to avoid wrong operation which may damage your computer permanently. If you have any problem or question during the whole removal process, please contact VilmaTech Support agents 24/7 online for more detailed instructions.
1. Safe Mode with Command Prompt
For Windows 7, XP & Vista
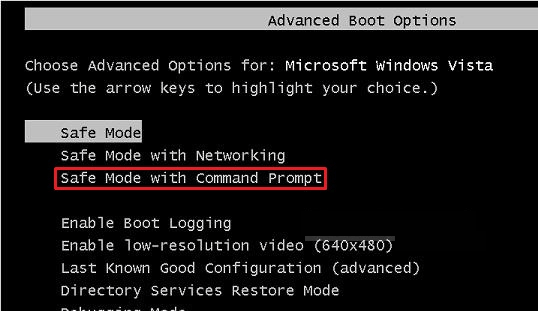
Reboot in “Safe Mode with Command Prompt”. To do this, restart the computer and before the Windows logo appears, tap the F8 key, a menu will appear, choose Safe Mode with Command Prompt and press the Enter key on the keyboard.
For Windows 8
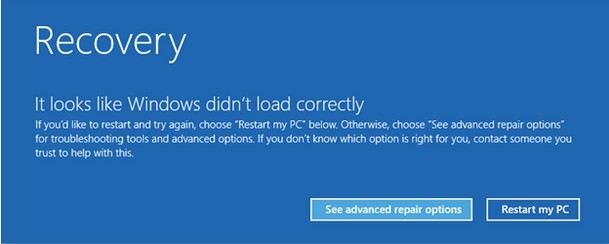
a. Start your computer, hold down the Shift key and hit the F8 key (Shift+F8) repeatedly. The Recovery Mode Window would pop up, choose the option of See advanced repair options.
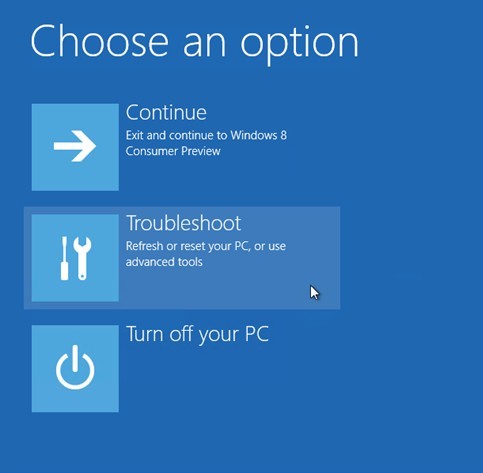
b. The Choose an option screen will appear, choose the Troubleshoot option to continue.
c. You will get there options in the Troubleshoot Window, click on or select the Advanced Options.
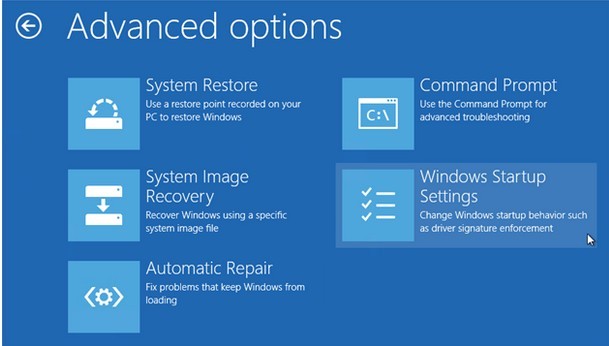
d. Now the Window Startup Settings option will come up. Click on Restart Button to continue.
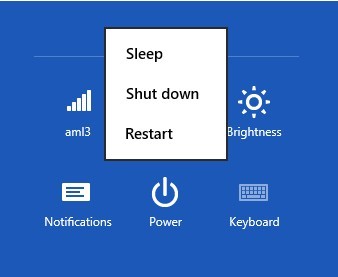
e. Highlight the Safe Mode with Command Prompt option or press number key 6 to enable Safe Mode with Command Prompt.
Tips: If you have any problems during the operation, you are welcome to contact VilmaTech Online Experts for real-time help.
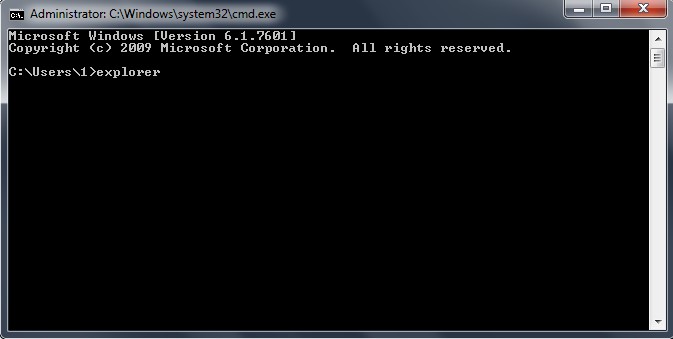
2. When the CMD (cmd.exe) Window pops up, type explorer and press Enter. It will show up your desktop.
3. Show hidden files of Metropolitan British Police virus.
4. Delete all related registry entries in your computer like these:
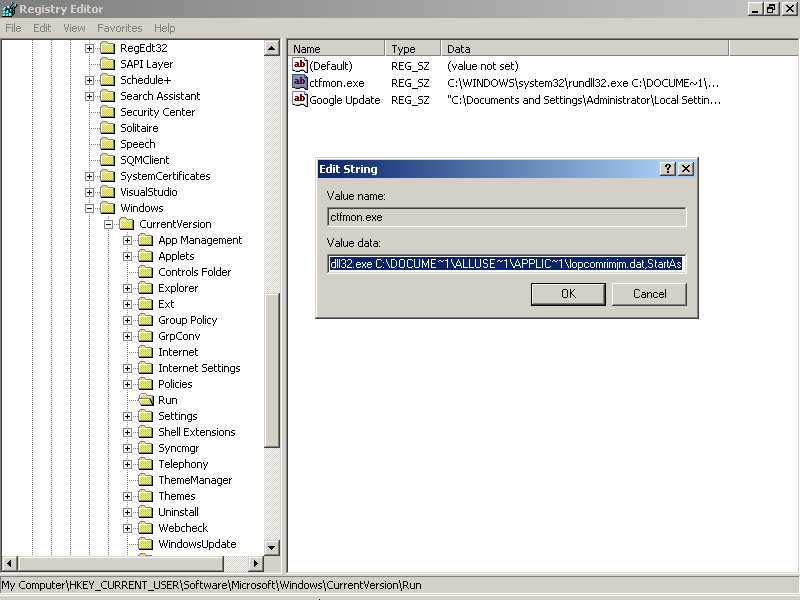
HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Toolbar\\10
HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Toolbar\\Locked
HKLM\Software\Microsoft\Windows\CurrentVersion\Run\Random.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{8AD9C840-044E-11D1-B3E9-00805F499D94}
5. Navigate and remove the associated files of Metropolitan British Police virus as follows:
%systemroot%\system32
%Temp%\.exe
%StartupFolder%\ctfmon.lnk
Ransom virus is categorized as dangerous malware that is created by cyber criminal intending for ransom money from victims. Ransom virus is classified of two forms. One of form is to encrypt files on computer system hard drive. In order to decrypt files, victims need the private key of which the copy is in remote hackers who threaten victims to pay for the decrypt key before time expire, otherwise they will destroy the decrypt key. An infamy encrypt ransom virus is called “CryptoLocker” emerged from Sept. 2013. The solution to release encrypted files is to clean hard drive and restore encrypted files from back up. Due to it propagates via emails, users should not open the attachments from unknown sources and those unsolicited with a fake notification of shipping or logistics.
The other form of ransomware will display a warning message that frames a case against victims and lock screen for fine. Victims will be accused of cyber criminals if they don’t pay after time limitation. This type is also called “non-encrypt” ransomware. This notorious ransom virus of this type raging recent years includes Trojan:Win32/Reveton, Trojan:Win32/Weelsof, Trojan:Win32/Urausy and Trojan:Win32/revoyem.
Trojan Reveton family is the most far-reaching and widely spread ransom virus in recent years. Trojan Reveton was firstly detected in the late 2011, Britain then it overwhelmed European computers and peaked in 2012. In early time, this Trojan family targeted at Microsoft Windows operating system but later it also attacked Mac OS X. And the later report had showed that computers in Australia, New Zealand and the USA were infected with this Trojan widely, which demonstrated that Trojan Reveton had been a global infection in 2012. Reveton family generated many variants since it was detected, such as Trojan:Win32/Reveton.V. Though it lost popularity in 2013, there was new version detected in October. Trojan Reveton arrives as a dll file and created files at startup folder. Afterward, it managed to modify the running programs so that victims could not access to desktop or security system to prevent against it. The outstanding symptom was the fake warning it gave ob screen declaring that you violated related laws of viewing pornography.
Victims were required to pay a fine before time limit; if not, their computers would not be unlocked and a criminal case would be against them. However, it pretended to be local law enforcement so as to scam victims’ money.
Similarly, Trojan Urausy family adopted the same means to trick users. Usually, it disguises as video plugins fooling users to install which are spread by exploit kits. This malicious Trojan gang infiltrated in computers sneakily and propagated their code to create their infected files and alter other regular processes. It attacked computers in a sudden when you found you’re disabled to access to Internet and running programs. Urausy family locked screen with bogus warning. Due to it supported many languages globally, it displayed the fake or corresponding legitimate institution with official logo according to victims’ IP address. It ransomed money via Ukash, MoneyPak or Paysafecard voucher. It was able to access to your webcam and took photo of victims for threaten. These Urausy family members include Metropolitan British Police virus, FBI Department of Defense Cyber Crime Center virus, Agence Nationale De La Sécurité Des Systèmes D’information virus (French), Australian Federal Police virus, BundesKriminalamt virus (German), etc.
In order to prevent from infection of metropolitan British Police virus and the similar scam, users ought to develop a good web surfing habit at first because some infection is attributed to careless. Here are some tips on how to avoid this kind of ransomware.
1. Never download the illegal video, images and programs from websites. Most of viruses hide on malicious websites which contains pornography, gambling, and violence, etc. which may attract you curiosity but they are under poor security easily compromised to various malware.
2. You should make sense that any law enforcements have no right to threaten you to pay for a fine to release your violence. And when it refers to international police institutions, you need to check the authenticity of the institutions because some of the names and logos are fabricated.
3. Whenever you are involved with the online business, you need to pay attention on the security. Pay on a reliable payment utility which can trace the receiver and ensure the security of you password and account information.
4. Although some security programs cannot detect this kind of ransom virus for it always updates its version, it is important to use authoritative antivirus and antispyware programs and maintain it updating virus database. Besides, keep firewall turned on, for it is the first guard for your computer.
The Metropolitan British Police virus is one of high-risk Android ransomware that locks target machine and demands ransom from victims. In the name of the Metropolitan British Police and Serios Organised Crime Agency (SOCA), the Metropolitan British Police Android virus pretends to be an authoritative organization and threaten victims to pay non-existent fine on it. Certainly that, PC users should never pay needless money on it and need to figure out the effective approach to remove Metropolitan British Police Android malware as soon as possible. Because the Metropolitan British Police virus has the ability to disable the operation of install programs such as antivirus applications. Therefore, auto removal has the low chance to remove Metropolitan British Police Android threat effectively and completely. It is strongly recommended for users to remove Metropolitan British Police Android scam through the almighty manual removal help.
Manual removal is a complex and hazardous process that may cause irreparable man-made damage to your computer. If you’re not professional, it is recommended that you back up Windows registry first before carrying out the approach. Can’t remove Metropolitan British Police virus by yourself? Please click to chat with VilmaTech Online PC Experts, your problem will be fixed effectively.