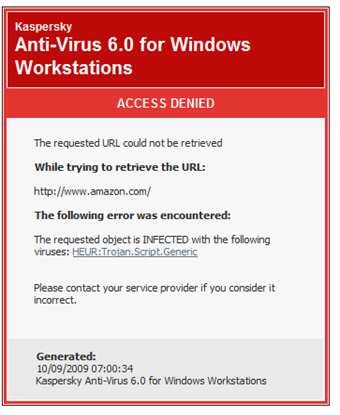
HEUR:Trojan.Script.Generic is a Trojan horse with additional capability added. As its names suggests. The Trojan horse possesses the typical abilities such as opening up backdoor, stealing information, modifying some drivers and lurking deep in a target system as well as the ability to propagate, attack and make use of web browser techniques.
According to the reports from victims, getting HEUR:Trojan.Script.Generic would disable the access to most of the web sites but to a bogus Flash Player update page. Though installed anti-virus programs manage to pick it up, they do no effective work on the virus. To get more details about the Trojan horse and to get solution to it, it is recommended to keep reading. Should you have questions or confusions, please do feel free to start a live chat for prompt answers.
It is no happenstance to be affected by HEUR:Trojan.Script.Generic. As a Trojan horse, it could put its vicious codes after attacking some bugs on website or vulnerability on programs; also it could make bogus websites/programs to trap PC users in downloading its vicious codes unwittingly. Below is the conclusion on how HEUR:Trojan.Script.Generic spreads offered by VilmaTech Online Support:
The last but not least, if one of the machine is attacked by HEUR:Trojan.Script.Generic, others within the LAN (local area network) will also be under attack. Therefore, it is still necessary to enhance the network security awareness.
HEUR:Trojan.Script.Generic worms into a machine mainly by attacking the vulnerability in Script, “a small non-compiled program written for a scripting language or command interpreter”. Such technique is the one that helps most of the busy and oblivious PC users to log-into accounts. Once it has been captured by HEUR:Trojan.Script.Generic, it will be utilized to record confidential information such as log-in credentials.
But the very first thing that the Trojan horse does is not to steal the information. Something must to be set to guarantee a convenient access to the information. Once HEUR:Trojan.Script.Generic finds vulnerability in the installed program, it would numerate drivers concerning security services, programs and processes to degrade the overall defense so that no automatic removal can drive it away before collecting confidential information.
With the modified driver, the related processes will be affected to execute the commands released actually by HEUR:Trojan.Script.Generic. Even though the behaviors are suspicious and breaking the security policy, with the background processes, the computer will just follow the commands. In such case, HEUR:Trojan.Script.Generic manages to call the internal services easily to gain easy access to the valuable information stored in the target machine.
Once the desired information is collected, HEUR:Trojan.Script.Generic would transfer it to its remote creator through the backdoor it opens up. The Trojan horse can also help generate money by alleviating the installation of additional virus, Trojan horse especially. Therefore it is advisable to remove HEUR:Trojan.Script.Generic as soon as possible in an attempt to stop any further harms. Below is the instruction to show how when security utilities fail. Follow the steps carefully only when certain level of computer skills and virus knowledge are available; otherwise, please do start a live chat and get specialized technical help from VilmaTech Online Support.
Step1. Disconnect the Internet and close down all the restore points.
(tip: HEUR:Trojan.Script.Generic would affect all detected restore point to stick to a target machine.)
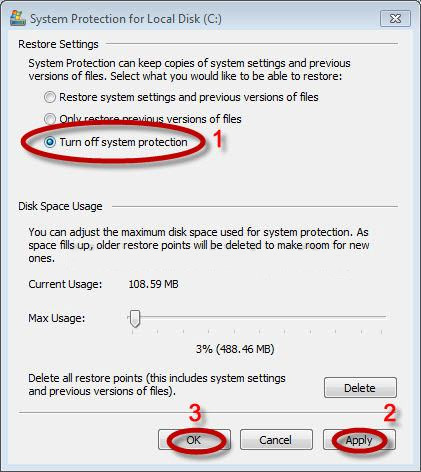
Step2. Remove restore file that HEUR:Trojan.Script.Generic may use to restore the removed items.

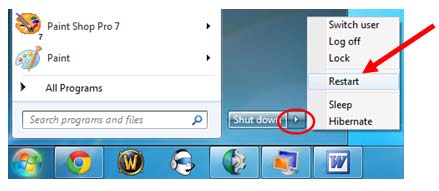
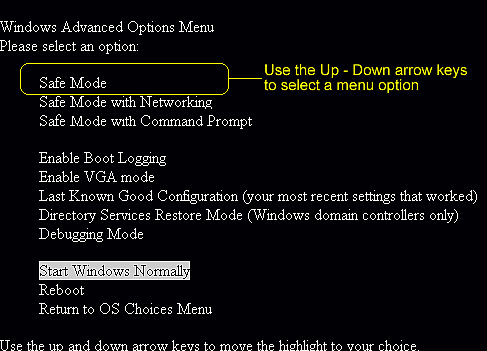
Step3. Restart the affected machine and get into Safe Mode.
Windows 7/Vista/XP
Windows 8
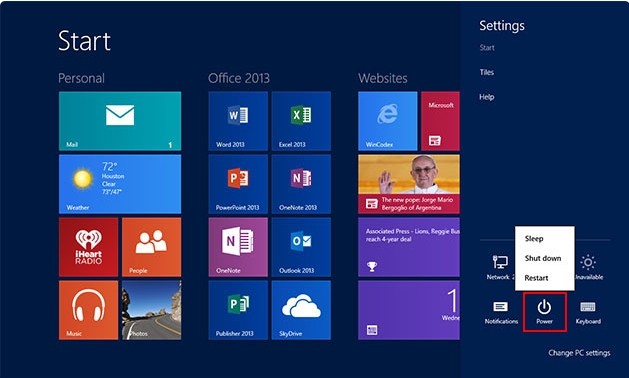
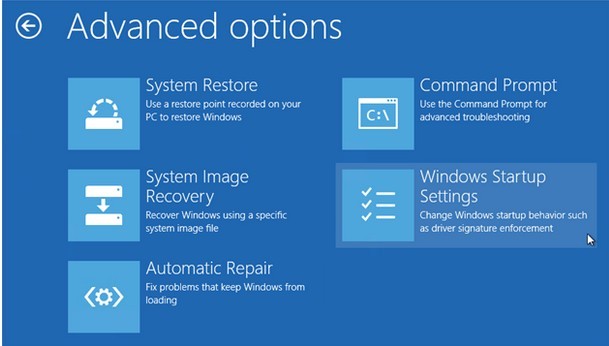
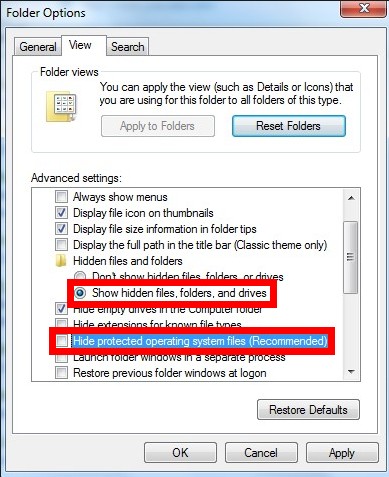
Step4. Show hidden files and folders to unveil the items hidden by HEUR:Trojan.Script.Generic.
Windows 7/XP/Vista
Windows 8
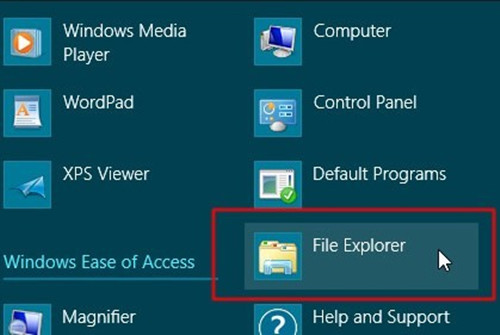
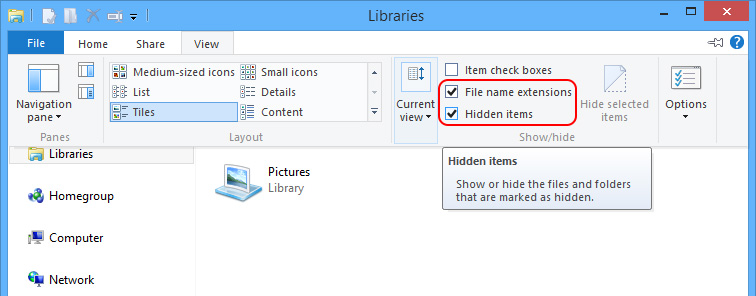
Step5. Remove all the files in the following listed folders.
C:\WINDOWS\Temp
C:\Documents and Settings\[user name]\Local Settings\Temp
C:\Documents and Settings\[user name]\Local Settings\Temporary Internet Files
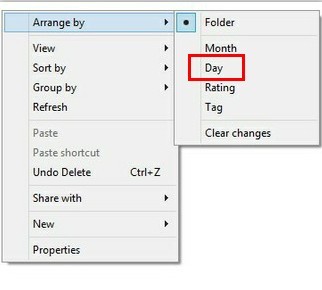
Step6. Arrange files by day to remove the items generated on the day when HEUR:Trojan.Script.Generic was firstly found.
Navigate to the following listed directories and to arrange the files by day with the steps:
C:\Windows
C:\Windows\System32
C:\windows\winstart.bat
C:\windows\wininit.ini
C:\windows\Autoexec.bat
C:\Users\[your username]\Documents\
C:\users\user\appdata\local\
C:\Program Files\
It is not to damage your machine and arouse malfunctions to make your life tough, HEUR:Trojan.Script.Generic is created to sneak into a machine for some confidential information such as bank account to get easy money illegally. Also, with the Script technique, the Trojan horse is capable of collecting online whereabouts, such information is what many online operators want for better promotion. By reselling such information, HEUR:Trojan.Script.Generic manages to generate profitable income for its creator.
as what we have learned from the preceding paragraphs that HEUR:Trojan.Script.Generic would compromise the overall machine and open up backdoor to transfer information as well as to help install additional virus for extra income. Therefore, one should check if there’s other infections apart from HEUR:Trojan.Script.Generic; if so, please remove any so that HEUR:Trojan.Script.Generic will not be triggered after the removal. If you do not know how to take down the additional infection, you can either seek the corresponding solution in VilmaTech virus reservoir or consult security assistance to get quick fix according to your concrete situation.
The restore point should be created and built after HEUR:Trojan.Script.Generic has been certainly removed completely and thoroughly. Be noted that the System restore functions cannot help remove a virus most of the time as virus nowadays has been developed with the capability of using restore point for persistent stay. But then creating a restore point could relieve the mechanical damages and inconveniences that would deter quick fix before additional infections are brought in to consolidate its settlement. Below is the video to show how: