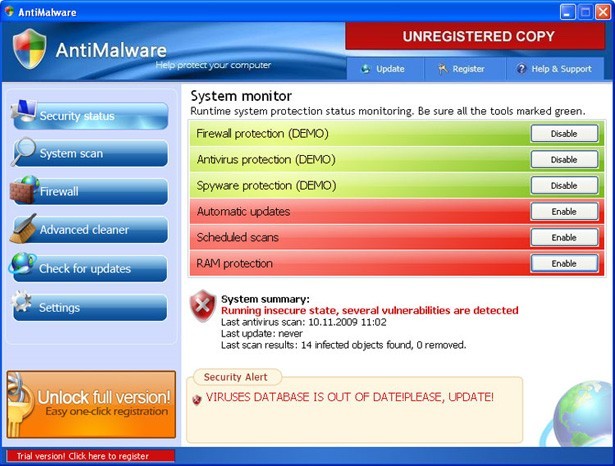
Antimalware misleads wide range of computer users into considering it as a PC caring application. Some download it willingly in a hope that Antimalware will live up to what it claims to safeguard computer effectively from being attacked by virus; while some get its icon on desktop somehow without the intension to uninstall it since Antimalware looks exactly like legit program and manages to issue threat warnings that are not detected by other installed anti-virus programs.
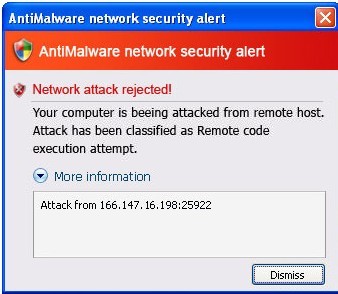
It doesn’t take long for one to realize that Antimalware is a rogueware:
※ Constant error reports are seen at each boot up.
※ Pop-up messages asking registration for Antimalware and noticing that protection will not be activated until a successful registration is made will not rest during surfing session.
※ Cursor occasionally freezes after Antimalware installs/ is installed.
※ Threats flagged by Antimalware cannot be found on the Internet.

Apparently, Antimalware aims at collecting money. It is wrong to think that it is fine if one doesn’t register for it. The hardship when removing Antimalware well explains the reason. Where an application wants something, it stays as long as it can. When Antimalware sets up in a system, it drops its registry keys into startup section, guaranteeing its auto launch at each PC boot. When the installation finished, Antimalware places its registry keys into running process in a bid to affect others for collecting information stored there. There are many registry keys being inserted into the target machine to serve Antimalware’s purpose of collecting information rather than torturing users with poor PC performance and endless popup messages. It is worth the attention that on the occurrence of modification by force in such case, the security defense will be definitely weakened to produce vulnerability, becoming more susceptible to virus that are piggybacked on programs and sensitive to vulnerability. That’s why there are not a few reports on additional infections seen after installation of Antimalware. In this case, one should remove Antimalware as soon as possible.
However, it is not an easy task. Because of those injected registry entries, Antimalware manages to be stick in the target machine without being removed or even detected by installed anti-spyware programs as they have made vicious items members of protected files by Windows. Therefore, to remove Antimalware, manual approach is the top alternative. Below are steps for PC users to get out of trouble by selves trawled through by VilmaTech online professionals. Try them out and rescue computers.

Step One. Running process of Antimalware should be terminated in the first place to avoid being hindered by error message telling failure is met because certain file is used at the moment.
⊙ Windows 8
Start screen > type ‘Task’ or ‘Task Manager’ > select ‘Process’ tab > find and select items associated with Antimalware > press ‘End’ to remove Antimalware.
⊙ Windows7/vista/XP
Hold Ctrl, Alt and Delete combination key together > select ‘Process’ tab > find and select items associated with Antimalware > press ‘End Process’ to remove Antimalware.
Step Two. Go to Control Panel to see if you stand any chance to detect Antimalware there; if so, right click on it to select ‘Remove’.
⊙ Windows 8
Move mouse to bottom-right corner of your desktop > choose ‘Control Panel’ in the pop-up sidebar > “Programs and Features” > remove Antimalware there.

⊙ Windows7/vista/XP
Start menu > select ‘Control Panel’ > choose ‘Uninstall Programs’ > remove Antimalware there.
Step Three. Show hidden files before finding out and removing any vicious items hidden by Antimalware in Drive C.
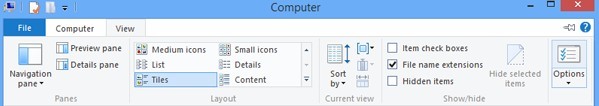
⊙ Windows 8
>Click on Windows Explorer application from Start Screen.
>Select View tab.
>Tick ‘File name extensions’ and ‘Hidden items’ options.
>Click ‘OK’.
⊙ Windows7/vista/XP
>Open ‘Control Panel’ from Start menu and search for ‘Folder Options’.
>Under View tab, tick ‘Show hidden files and folders and non-tick Hide protected operating system files (Recommended)’
>Click ‘OK’.
Step Four. Reset all installed browsers (e.g. IE, Mozilla Firefox, Google Chrome) to cleanse junk, if any, brought in by Antimalware.
⊙ Internet Explorer:
>Open Internet Explorer.
>Click on the Tools menu -> select Internet Options.
>In the Internet Options window, click on the Advanced tab -> click on the Restore Defaults button -> press OK.
⊙ Firefox:
>Click on the Firefox button -> Help -> Troubleshooting information.
>Locate the box on the left uppers corner of the web page.
>Click on ‘Reset Firefox’ button.
⊙ Google Chrome:
>Choose ‘Customize and Control Google Chrome’ menu.
>Select ‘Options’.
>Click ‘Under the Hood’ tab.
>Click ‘Reset to Defaults’ button.
Step Five. Make rectifications in Database after finding items associated with Antimalware under HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion, HKEY_CURRENT_USER\Software\Microsoft\Windows and HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows.
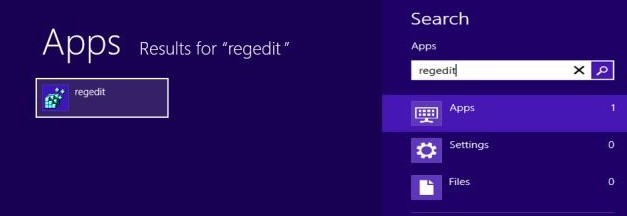
⊙ Windows 8
Move your mouse over lower right screen -> charms bar appears -> click Search charm -> type ‘regedit’/‘regedit.exe’ -> hit Enter key.
⊙ Windows 7/XP/Vista
Press Win key and R key together -> type ‘regedit’ (without quotation) in the box -> hit Enter key.
Kind reminder:
By reselling collected information to other spammers, Antimalware virus can also earn easy money without your registration for its service. Besides, because of the vulnerability after the installation of the rogueware, random files and folders, tracking cookies, strange add-ons, unfamiliar icons may be installed, which would absolutely slow down overall computer performance and even disable build-in services on the computer in some cases. It is not worth taking the risk of trying programs to remove Antimalware after many failures are met. Go straight to manual method even if you are not technically sound since computer professionals are always online ready to help. Use highly cautions when accessing database particularly; otherwise, any slight mistake may cause the compromised computer act weirdly and improperly.
