Any infiltration would incur some weird scenarios on a target machine since only vicious modification can guarantee that a virus would not be removed by build-in security utilities and services and that a continuous theft. However, some of the scenarios can be covert without arousing victims’ attention. Below is the list of the symptoms of Exploit:JS/Neclu.M affection, which would help you detect Exploit:JS/Neclu.M and take actions against the Trojan horse before more troubles are incurred thereby under the circumstance that it disables anti-virus programs:
To get to know the way that the Trojan horse land on a system and the dangers to be held hostage by it, it is advisable to keep reading. Should you have any question or emergency that you can’t deal with, you are welcome to contact VilmaTech Online Support and get specialized technical help.
As its name suggests, Exploit:JS/Neclu.M exploits the vulnerability existing within Java or Adobe Reader (the two indispensable components to offer a colorful vision of the Internet). Java is a network oriented programming language. It is now widely used to create applications that can be downloaded from the World Wide Web; while Adobe is utilized to display online images. All in all, the two components are all about the Internet and the Internet is the place where Exploit:JS/Neclu.M embeds awaiting any detected vulnerability.
Vulnerable Java and Adobe emerge when:
As stated above that Exploit:JS/Neclu.M owns a way to affect computer easily and widely; yet people should also be clear that the Trojan is a strong one, it does more than arousing mass on a target machine. JS (JavaScript) technology, the one that has been long employed by programmers to help alleviate the log-in process by remembering account and password, has been found to be adopted by the Trojan horse. With such technology, Exploit:JS/Neclu.M is capable of track down online whereabouts and thus record log-in credentials. People who did online shopping should change password after a complete removal as what VilmaTech Online Support advises.
Being a Trojan horse, Exploit:JS/Neclu.M possesses backdoor program. Such program will take advantage of the seldom used ports to connect its remote C&C server, questing new commands for improvements to deter some conventional removal and allowing unsolicited access from its cyber criminal to collected information. With the backdoor program wide open, additional infections can be anticipated.
What’s worse, the JS technology Exploit:JS/Neclu.M applies enables the Trojan to call background processes and thus modifies and overwrites drivers concerning security utilities and services, leaving malfunctioning computer protectors. In such case, manual removal is highly recommended.
Below is the instruction that could help with Exploit:JS/Neclu.M removal. Follow the instruction strictly to guarantee that no further problems would be incurred. Should you run into some difficulties in the middle of the removal due to deficient computer skills and virus knowledge, you are welcome to get exclusive assistance according to your concrete situation by starting a live chat window here.
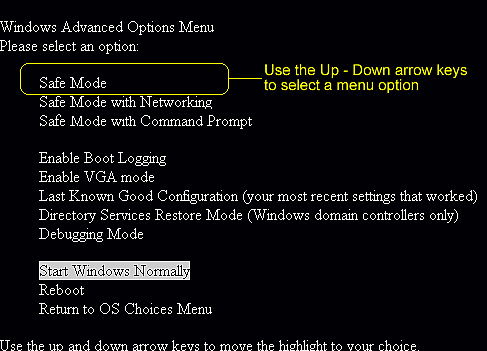
A – Enter into Safe Mode where some of the vicious parts will be disabled to run full scan for possible detection; if any, note down the detected directory.
Windows 7/Vista/XP
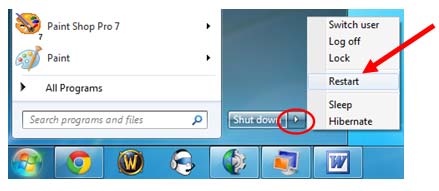
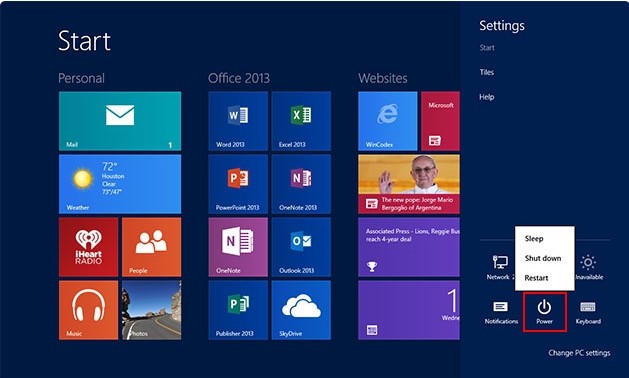
Windows8
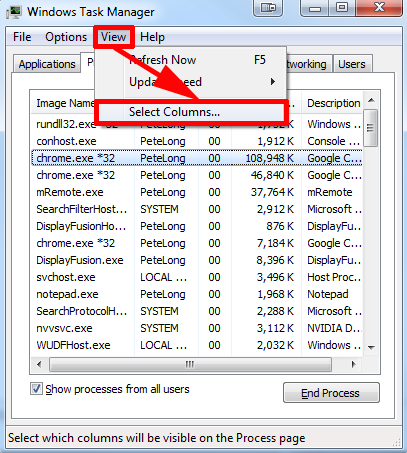
B – End the processes directing to Exploit:JS/Neclu.M’s directory.

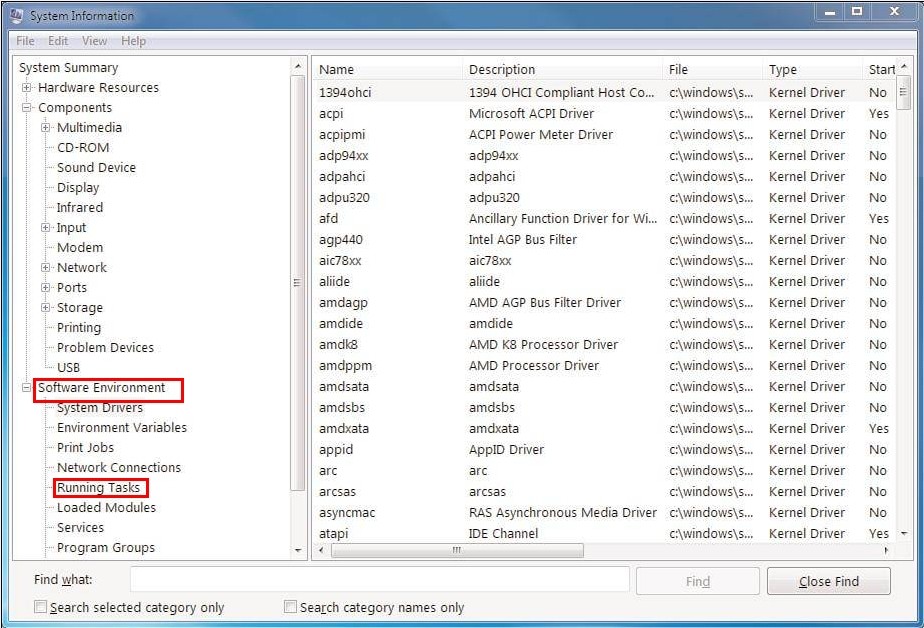
C – End the services with the path directing to Exploit:JS/Neclu.M’s and does not belong to system.
Windows7/vista/XP

Windows 8
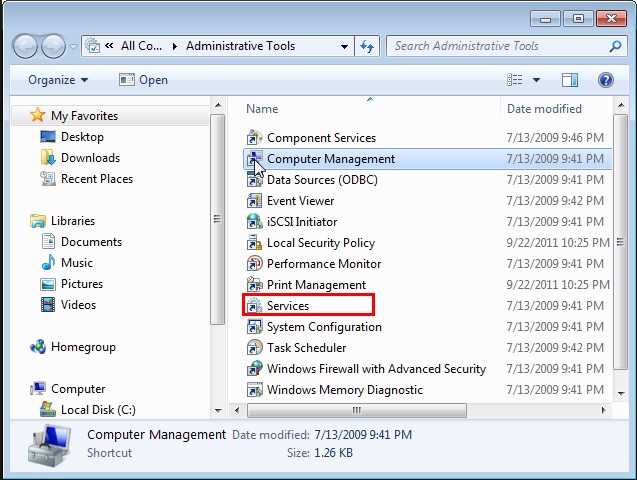
D – Show hidden items to remove files generated by Exploit:JS/Neclu.M.
Windows 7/XP/Vista
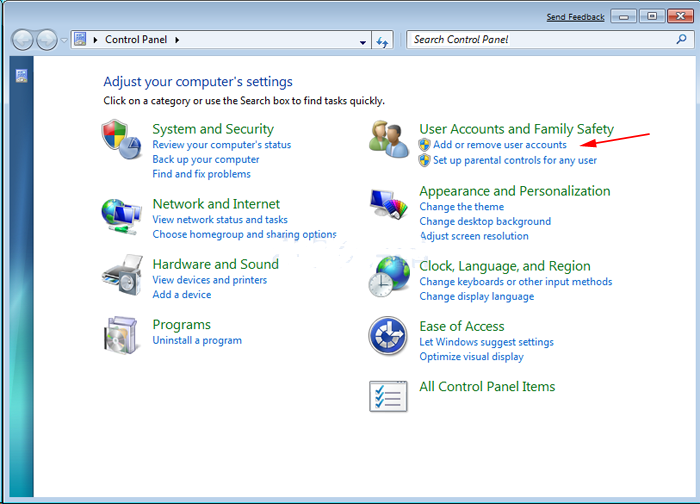
Windows 8
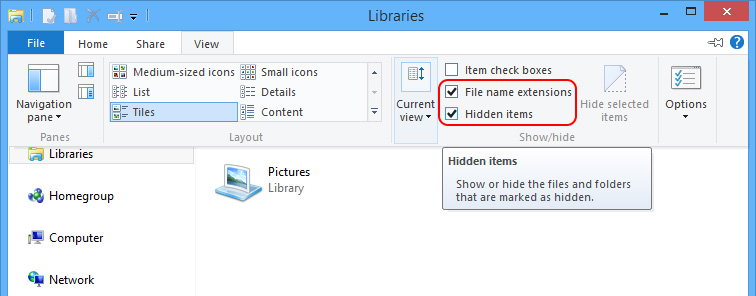
Step1. access to the following folders.
C:\windows\winstart.bat
C:\windows\wininit.ini
C:\windows\Autoexec.bat
%WINDIR%\SYSTEM32\
%APPDATA%\MicroLab\MyEngin\Common
Tip:
- %Windir% refers to the catalog that WINDODWS is situated.
- %Application Data% refers to Application Data folder for current user; it can be:
C:\Windows\Profiles\{user name}\Application Data (Windows98 and Windows Me)
C:\WINNT\Profiles\{user name}\Application Data (Windows NT)
C:\Documents and Settings\{user name}\Local Settings\Application Data (Windows2000, Windows XP and Server 2003)
Step2. arrange the files according to created date.
Step3. remove temp files in the following listed folders.
C:\Windows\Temp
%TEMP%\[messy code]temp_0\
C:\Documents and Settings\[user name]\Local Settings\Temporary Internet Files
C:\Documents and Settings\[user name]\Local Settings\Temp
People now knowing about the dangers and harms by Exploit:JS/Neclu.M want to know why virus like it keep attacking computers. The answer is simple and clear-cut. Cyber criminals live on creating virus. In other word, virus like Exploit:JS/Neclu.M attack computers for money. But how it gets money?
Complete removal is highly recommended. As what has been stated clearly in the article body that Exploit:JS/Neclu.M is capable of bringing in additional infections, removing the Trojan horse will not stop further damages and its re-image can be anticipated due to the vulnerability made by other brought in virus. If one reads the first paragraph clearly, one would know that certain level of computer skills and knowledge is required to carry out the above offered steps correctly and comprehensively for a final complete removal. Since Exploit:JS/Neclu.M is highly elusive, it generates mutex and produce more and uncertain items from its remote server to hinder universal removal method. But the above removal thread is providing the right track on removing Exploit:JS/Neclu.M. On the occurrence of inability to tell which are vicious and which are not during the removal procedure, it is advisable to ask senior technician from VilmaTech Online Support for quick fix.
It is recommended to do a defragment after Exploit:JS/Neclu.M’s complete removal as an OS optimization. With random items scattered on the target system and some corrupted items by Exploit:JS/Neclu.M’s random modifications, the internal storage is no longer ideally utilized. As a consequence, there’s no pickup on the PC performance even after removing the Trojan horse. Below is the video to show how.