Trojan.Inject.ED, unlike generic Trojan, takes advantage of controversy running processes or programs, such as iexplorer.exe, to inject vicious code so that build-in anti-virus programs are weaken to the extent where removing computer threats is impossible and DNS setting is manipulated to link to the URL that loaded with threats. In sum, Trojan.Inject.ED is a Trojan that serves to help embed additional computer threats into the target machine. However, nuances exit between Trojan.Inject.ED and Trojan Dropper. Trojan.Inject.ED injects vicious codes of threats into some processes or suffix while the latter drops infections directly.
For instance, when the a GIF file with its foot being injected with malicious link by Trojan.Inject.ED is visited, its content relevant to iframe will be parsed by Internet as HTML, which will definitely direct target to the URL contained in iframe when the target is viewing the picture.
Being developed on Microsoft Visual C++ platform, Trojan.Inject.ED targets Windows OS. Once it settles on a machine, it implants its startup item and generates values into corresponding sections. As a result, configuration will be changes to its satisfaction. The top sections Trojan.Inject.ED affects are startup section, security section and DNS section, so that it is capable of ensuring that each Windows start would woken it up to continue vicious deeds, that it will not be removed automatically and that designated sites will be connected to download more virulent data.
In effect, when DNS setting is manipulated, backdoor is coming into force. It can be inferred that additional infections, junks and files will be detected on an infection computer. Rovnix.gen!C is commonly seen during Trojan.Inject.ED affection period. With more exotic items injected into the target machine, mechanical damages such as considerably consumed CPU occur. Please do not forget that Trojan.Inject.ED belongs to Trojan horse, it is also capable of stealing information of the configuration as well as online whereabouts by recording keystrokes and using JS technique. For more Trojan.Inject.ED behaviors, please keep reading. Should there be any question, you are welcome to start a live chat window here for prompt response.
Usually speaking, Trojan.Inject.ED can be detected on a machine that is not protected well or by someone that doesn’t follow up good PC practice in daily life. It should come to your knowledge that any vulnerability can be easily exploited by the Trojan, whether it is within installed programs, system or downloaded web applications. Besides, extra carefulness is suggested to be applied when surfing on the Internet. Once visiting a web site that has bug, the connected machine will be forced to download malicious code without your knowledge. Therefore, the below acts are recommended to follow up in order to prevent infiltration and decrease the chance to get infections:
Though PC users want to remove Trojan.Inject.ED badly and anti-virus programs are able to pick it up, security utilities are not able to bring about the result everyone wanted after all. All anti-virus programs deal with infections according to attribute code. In other word, what can be automatically removed are the ones recording in virus reservoir to the exclusion of verisimilar items to system ones like autorun.inf, winlogon.exe, system.exe and svchost.exe.
What’s more, senior technician from Global PC Support Center has found out that Trojan.Inject.ED adopts complex SHA1 and employs UPX to protect itself from being modified as well as being tracked down easily and automatically. Therefore, manual removal method is highly recommended when removing Trojan.Inject.ED. However, it needs certain level of computer knowledge and skill. Should you be stuck in the middle of the removal due to deficient knowledge, please feel free to contact VilmaTech Online Support and ask for professional assistance.
Though manual removal method is considered to be the best option to remove Trojan.Inject.ED, one should know that it is a hard-core that utilizes desktop.ini to help recover the deleted items. Therefore, complete removal is required and extra carefulness is required not to touch any suspicious executable files so that Trojan.Inject.ED will not re-emerge frequently.
Step One – enter into Safe Mode before starting Trojan.Inject.ED removal.
Windows 8
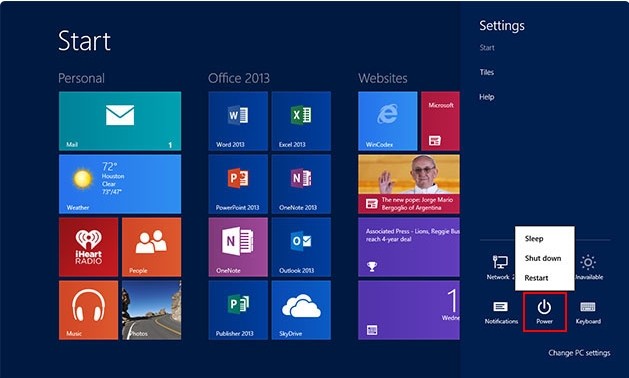
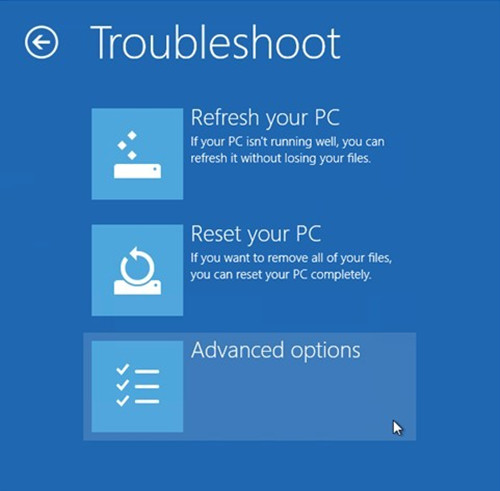
Windows 7/Vista/XP
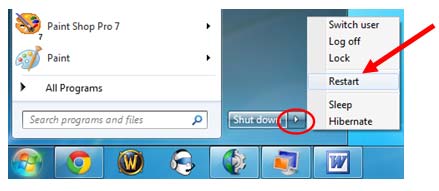
Step Two – enter into Database and remove items generated by Trojan.Inject.ED.
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun\[random numbers and letters]
HKEY_LOCAL_MACHINESOFTWAREClientsStartMenuInternetINTEXPLORE.pif\ToP
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{random numbers}
HKCU\Software\Microsoft\Windows\CurrentVersion\App Management\ARPCache\{random numbers}
Step Three – end associated running processes with Trojan.Inject.ED.
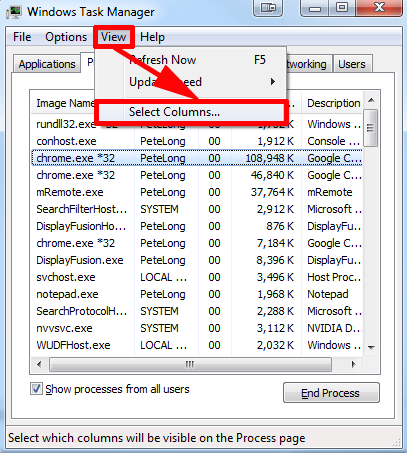

Step Four – show hidden items to remove items injected by Trojan.Inject.ED.
Windows 8
Access Windows Explorer and hit its View tab to check ‘File name extensions’ and ‘Hidden items’.
Windows 7/XP/Vista
Access “user accounts and family safety” contained in ‘Control Panel’ for ‘Folder Options’ to tick ‘Show hidden files and folders and non-tick Hide protected operating system files (Recommended)’ under View tab.
Files and folders to delete:
%WINDIR%\SYSTEM32\[random numbers and letters].dll
%TEMP%\[messy code]temp_0\[random letters]setup.exe
%APPDATA%\MicroLab\MyEngin\Common\DeleteSetup.exe
C:\Windows\system32\msconfig.com
C:\Windows\system32\regedit.com
C:\Windows\system32\rundll32.com
Trojan.Inject.ED is not created to impose harms to computers. Its purpose can be divided into two parts: 1) to obtain profitable income for its author; 2) to help propagate other products by the same author. As stated in the preceding paragraphs that Trojan.Inject.ED manages to steal information of configuration and whereabouts. One should be aware that there’s a great demand for such information since it helps spammers to develop infections with the ability to penetrate into as more computer as possible through detected vulnerability and put infections onto the most favorite web sites for a rapid spread.
The common scene when removing Trojan.Inject.ED is that it returns after every reboot or it re-emerges before long. The cause can be either incomplete removal or fail in following good PC practice. Be noted that Trojan.Inject.ED has the capability of injecting vicious codes into a target machine. One should thus check the entire local disk for suspicious items that are brought in by Trojan.Inject.ED. Otherwise, even a tiny piece of malicious item would be able to call it back. The last but not least, optimization is recommended by VilmaTech Online Support to be executed on installed browsers in case the modified DNS setting would keep redirecting PC users to malevolent URL and make re-infection possible. On the occurrence that Trojan.Inject.ED will not be tackled down after following the offered steps, additional items might have been injected. It is whereupon advisable to get specialized technical help by starting a live chat here and seek peace eventually.