Generic PWS.ak is a kind of Trojan horse virus which had been found on 2009 for the first time. Recently we have noticed that a few of anti-virus programs scan and detect out the Trojan Generic PWS.ak again. Most of the PC users never realize their computers have been infected by this virus at all. VilmaTech threat research lab believes Trojan Generic PWS.ak should be removed immediately otherwise it would bring more damage to PC system and create back doors to give malicious users access to the infected PC system. Once the computer has installed Trojan Generic PWS.ak, it will run high risky of losing bank account, credit card password, personal files and other important data. Moreover, Windows computer will be controlled maliciously by attackers who designed this Trojan virus and trying to proceed some illegal activities with the infected computer. PC users sometimes will be involved in legal cases because of violation of some privacy which the attackers actually did. Generic PWS.ak is also a worm spread via removable drives and mapped system drives in order to steal sensitive information and gaming account information from the compromised machine. It also injects itself into the system running process to hide itself from the user. This Trojan also executes upon every system boot and drops a dll file into %WINDIR%\system32 folder and injects the dll file into the all system running process. Due to this Trojan:Generic PWS.ak infection, system shows high percentage of processor or processor already in use, even when a computer user not running any application.

Trojan Generic PWS.ak can be installed on Windows PC through serval ways. When PC users visit malicious websites, or legitimate websites that have been hacked, they probably get the infection of Generic PWS.ak. The Trojan and other PC threats such as Trojan Win64/Sirefef.AK, PCEU Virus, Ukash Virus can be installed sneakily on the Windows PC through system vulnerabilities without users permission of knowledge.
Another method used to propagate this type of PC threat is spam email containing infected attachments or links to malicious websites. Cyber-criminals spam out an email, with forged header information, tricking you into believing that it is from a trusted source. For instance, they claim to be Christmas’s greeting cards, romantic videos, etc. Once you open,click and download the attachment, you will be redirected to malicious website and get the infection easily. In some cases, Trojan Generic PWS.ak is often packaged with pirated or illegally acquired software.
In order to avoid being infected by malware and viruses, VilmaTech suggest that PC users should be more caution when visiting website and downloading applications on the Internet. Never visit porn, gamble and other illegal web pages; never click on links from suspicious places; never download & install programs especially freeware on un-trusted website.
Windows registry will be changed maliciously when the PC get infection. The following registry values have been added.
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{GUID}\VersionIndependentProgID\: “IEHlprObj.IEHlprObj”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{GUID}\ProgID\: “IEHlprObj.IEHlprObj.1”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{GUID}\InprocServer32\: “%WINDIR%\system32\bgdferw0.dll”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{GUID}\InprocServer32\ThreadingModel: “Apartment”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{GUID}\: “IEHlprObj Class”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{GUID}\TypeLib\: “{GUID}”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{GUID}\TypeLib\Version: “1.0”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{GUID}\ProxyStubClsid32\: “{00020424-0000-0000-C000-000000000046}”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{GUID}\ProxyStubClsid\: “{00020424-0000-0000-C000-000000000046}”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{GUID}\: “IIEHlprObj”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{GUID}\1.0\0\win32\: “%WINDIR%\system32\bgdferw0.dll”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{GUID}\1.0\HELPDIR\: “%WINDIR%\system32\”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{GUID}\1.0\FLAGS\: “0”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{GUID}\1.0\: “IEHelper 1.0 Type Library”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj\CurVer\: “IEHlprObj.IEHlprObj.1”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj\: “IEHlprObj Class”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj.1\CLSID\: “{GUID}”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj.1\: “IEHlprObj Class”
HKEY_USERS\S-1-5-[Varies]\Software\Microsoft\Windows\CurrentVersion\Run\hjdsdse: “%WINDIR%\system32\oukdfgr.exe”
VilmaTech Threat Lab devote themselves to analyze the latest PC threat research and viruses removal instructions. Follow and finish steps as below, Trojan Generic PWS.ak can be removed from your infected computer completely.
Step One: Reboot Your Computer. Press”F8” on the keyboard before the Windows system has been launched.
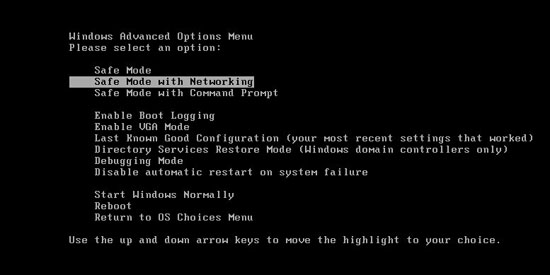
Step Two: Press CTRL+ALT+DEL or CTRL+SHIFT+ESC(this operation varies by different operating systems). Open the Windows Task Manager.
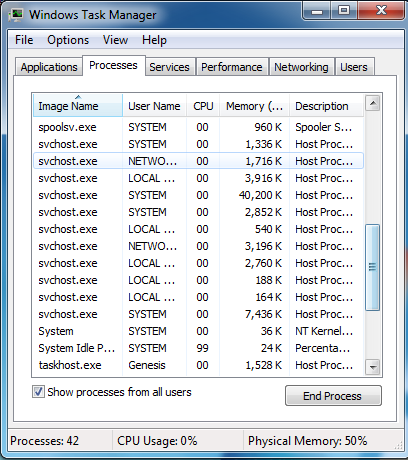
If it didn’t work, try another way by pressing the Start button and click on the Run option. This will start the Run tool. Type taskmgr in the blank and press OK. This can help you open the Task Manager.
Step Three: Click on Processes tab. Find the process by the name of random.exe. Then scroll the list to find required processes. Select it with your mouse or arrow keys on the keyboard and click on End Process button.
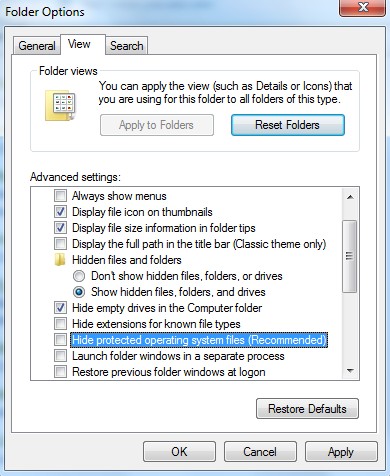
Step Four: Click “Start” menu — “Control Panel”. Search out the “Folder Options” and show hidden files in this area.
Step Five: Press Windows+R keys and then type regedit in Run box to open Registry Editor. Then delete the registry entries:
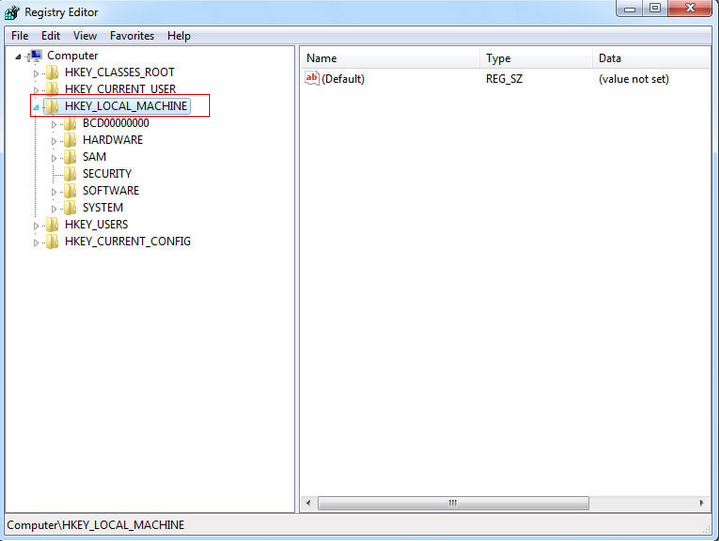
The above mentioned registry ensures that, the Trojan registers itself with the compromised system and executes itself upon every boot.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\KAVsys\Type:1
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\KAVsys\ErrorControl:1
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\KAVsys\Start:2
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\KAVsys\ImagePath:%WINDIR%\system32\drivers\klif.sys
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{GUID}\VersionIndependentProgID\: “IEHlprObj.IEHlprObj”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{GUID}\ProgID\: “IEHlprObj.IEHlprObj.1”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{GUID}\InprocServer32\: “%WINDIR%\system32\bgdferw0.dll”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{GUID}\InprocServer32\ThreadingModel: “Apartment”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{GUID}\: “IEHlprObj Class”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{GUID}\TypeLib\: “{GUID}”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{GUID}\TypeLib\Version: “1.0”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{GUID}\ProxyStubClsid32\: “{00020424-0000-0000-C000-000000000046}”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{GUID}\ProxyStubClsid\: “{00020424-0000-0000-C000-000000000046}”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{GUID}\: “IIEHlprObj”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{GUID}\1.0\0\win32\: “%WINDIR%\system32\bgdferw0.dll”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{GUID}\1.0\HELPDIR\: “%WINDIR%\system32\”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{GUID}\1.0\FLAGS\: “0”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{GUID}\1.0\: “IEHelper 1.0 Type Library”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj\CurVer\: “IEHlprObj.IEHlprObj.1”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj\: “IEHlprObj Class”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj.1\CLSID\: “{GUID}”
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\IEHlprObj.IEHlprObj.1\: “IEHlprObj Class”
HKEY_USERS\S-1-5-[Varies]\Software\Microsoft\Windows\CurrentVersion\Run\hjdsdse: “%WINDIR%\system32\oukdfgr.exe”
After you delete the malicious registry entries above, you need to remove the files which Generic PWS.ak added on your PC.
%WINDIR%\system32\bgdferw0.dll
%WINDIR%\system32\hyrteas0.dll
%WINDIR%\system32\oukdfgr.exe
%Systemdrive%\autorun.inf
%Systemdrive%\lhylec9x.cmd
If you are not confident of deleting the malicious registry keys and files hidden in the Windows system folder, or if you have any questions or doubt at any point, STOP and ask for VilmaTech assistance. VilmaTech online support will have real-time chat with you and give you some professional suggestion.

For More Information of Trojan Generic PWS.ak